Source: www.cyberdefensemagazine.com – Author: News team The specter of security vulnerabilities is a constant concern in today’s digital landscape. They’re the hidden pitfalls that can undermine...
Day: December 21, 2024
What Payroll Documents Do You Need to Pay Employees? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Bryan Driscoll We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Best SIEM Tools: Top Solutions for Enhanced Security – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
In Other News: McDonald’s API Hacking, Netflix Fine, Malware Kills ICS Process – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide...
Botnet of 190,000 BadBox-Infected Android Devices Discovered – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire More than 190,000 Android devices have been observed connecting to newly uncovered BadBox botnet infrastructure, cybersecurity firm Bitsight reports. The...
Embracing Technology for Impactful Change
Nancy Sun reflects on her 20+ year career in tech and shares how she used her engineering background to support neurodivergent children — including her own....
Year in Review: Explore SWE’s Highlights of 2024
As 2024 comes to an end, SWE reflects on the Society’s achievements and impact from the past year. Source Views: 1
SWE Diverse Podcast Ep 294: The Power of Perseverance With Secretary of Puerto Rico DTOP Eileen Vélez-Vega
Eileen Vélez-Vega reflects on her time as the first woman to be appointed Secretary and CEO of the Puerto Rico Department of Transportation and Public Works...
HeForSWE Affinity Group Spotlight on Allies
In their new spotlight month post, the HeForSWE AG asked women and men alike how they can be allies in the workplace. Source Views: 1
Ditch The Cloud Security Labels to Nail Detection and Response – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Today’s cloud security categories don’t do practitioners any favors when it comes to identifying the key requirements for detection and...
Is There a DDoS Attack Ceiling? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Today, it’s rare for a month to pass without reports of new distributed denial-of-service (DDoS) attacks. Lately, geopolitical instability and hacktivist groups...
DEF CON 32 – Laundering Money – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, December 20, 2024 Home » Security Bloggers Network » DEF CON 32 – Laundering Money Author/Presenter: Michael Orlitzky Our...
Will AI Drive Efficiency and Budget Growth? Risks, Rewards & Reality – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore The adoption of artificial intelligence (AI) in cybersecurity continues to spark intense discussions, especially around its impact on efficiency and...
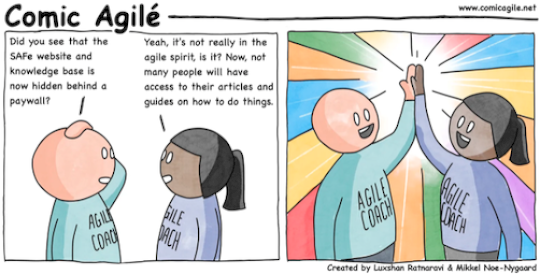
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #317 – Paywall – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the respected Software Engineering expertise of Mikkel Noe-Nygaard and the lauded Software Engineering / Enterprise Agile Coaching work of Luxshan Ratnaravi at Comic Agilé! Permalink *** This is a...
Log4Shell Vulnerability | Why it Still Exists and How to Protect Yourself | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Contrast Marketing Three years ago, Log4Shell was the worst holiday gift ever for security teams, particularly given that it was wrapped in...
AI-Powered Actions Cybersecurity Leaders Are Taking to Outwit Bad Actors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Gosschalk As a cybersecurity executive, your job is clear: protect business operations, safeguard consumers and ensure the security of your employees....
Diamond Bank Addresses Spoof Websites – Source: securityboulevard.com
Source: securityboulevard.com – Author: pmiquel Diamond Bank is a community bank with 14 branches and thousands of customers in the Southwest Arkansas region. The bank celebrated...
DEF CON 32 – Measuring the Tor Network – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, December 20, 2024 Home » Security Bloggers Network » DEF CON 32 – Measuring the Tor Network Authors/Presenters: Silvia...
Impart is now available in the AWS Marketplace | Impart Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Impart Security Blog Today, we are thrilled to announce that Impart is now available in the AWS Marketplace. More Streamlined Contracting AWS customers...
SAML (Security Assertion Markup Language): A Comprehensive Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data...
Bitter APT Targets Turkish Defense Sector with WmRAT and MiyaRAT Malware – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Dec 17, 2024Ravie LakshmananCyber Espionage / Malware A suspected South Asian cyber espionage threat group known as Bitter targeted a Turkish defense...
Friday Squid Blogging: Squid Sticker – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...