Source: www.hackerone.com – Author: johnk. Please find below a list of Feature updates/releases that happened in our first quarter! You can find more details about each...
Day: December 15, 2024
Beyond Encryption: Advancing Data-in-Use Protection – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the ever-evolving landscape of cryptography, traditional encryption methods safeguarding data at rest and in transit remain foundational to cybersecurity...
Hacking Dropbox Live in the Heart of Singapore at h1-65 – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. HackerOne’s first live hacking event in Southeast Asia, h1-65, kicked off during Black Hat Asia in Singapore! As one of the...
Upcoming Speaking Events – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier HomeBlog Upcoming Speaking Events This is a current list of where and when I am scheduled to speak: I’m speaking...
Innovating with Secure Secrets Rotation Techniques – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn With the rapid expansion of digitized environments, the demand for effective and secure identity management has surged. Organizations are increasingly...
Proactive Approaches to Identity and Access Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Proactive Security Crucial in IAM? Have you ever weighed the impact of security breaches and data leaks on...
Navigating Cloud Security for Future Proofing Your Assets – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Cloud Security Imperative for Asset Protection? As businesses increasingly migrate their operations to the cloud, the demand for...
Gaining Confidence Through Effective Secrets Vaulting – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Secrets Vaulting Crucial in Today’s Cybersecurity Landscape? In a world increasingly dependent on cloud-based services, how do organizations...
DEF CON 32 – MobileMesh RF Network Exploitation Getting the Tea from goTenna – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Saturday, December 14, 2024 Home » Security Bloggers Network » DEF CON 32 – MobileMesh RF Network Exploitation Getting the...
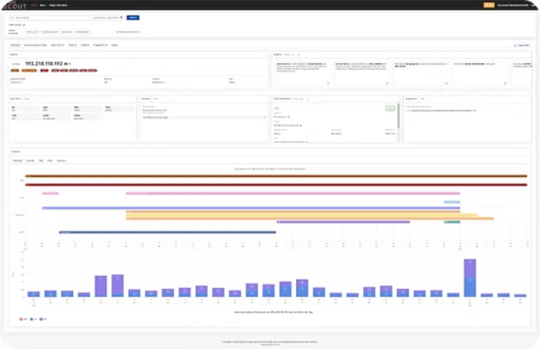
2024 Year in Review: Features and Improvements in Pure Signal™ Scout – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Monnier Team Cymru is excited to share our accomplishments in delivering new features and improvements in Pure Signal™ Scout. Thank you...
Feeling Reassured with Top-Tier API Security Measures – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Maximizing Your API Security Measures? If you’re a CISO or a cybersecurity professional, you understand the importance of...
How Can Strong Secrets Management Prevent Data Breaches – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your Secrets Management Strong Enough to Prevent Data Breaches? In an increasingly connected digital world, secrets management has emerged...
Scaling Your Cyber Defense with Advanced IAM Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn How Crucial is the Role of Advanced IAM in Scaling Your Cyber Defense? With the rise in cyber threats, businesses...
Living in the Age of AI: Reflections from a Year at the Helm of Cybersecurity – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: When I joined Proofpoint a year ago, I was humbled by the opportunity to lead a company at the forefront of cybersecurity....
How Proofpoint Is Redefining Cyber Threat Defense – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Proofpoint CEO Sumit Dhawan shares his vision for a safer digital future. getty When Sumit Dhawan stepped into the role of CEO...
The New Boardroom Mandate: Data Security As A Strategic Priority – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Ravi Ithal, GVP and CTO, Proofpoint DSPM Group. Ravi was also a cofounder of Netskope. getty It will come as no surprise...