Source: www.securityweek.com – Author: Ryan Naraine The UK’s National Cyber Security Centre (NCSC) has published technical documentation of a sophisticated network backdoor being planted on hacked...
Month: November 2024
GreyNoise Credits AI for Spotting Exploit Attempts on IoT Livestream Cams – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Cybersecurity firm GreyNoise Intelligence is crediting an AI-powered tool for capturing attempts to exploit critical vulnerabilities in live streaming IoT...
In Other News: FBI’s Ransomware Disruptions, Recall Delayed Again, CrowdStrike Responds to Bloomberg Article – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide...
US, Israel Describe Iranian Hackers’ Targeting of Olympics, Surveillance Cameras – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The United States and Israel this week published a cybersecurity advisory describing the latest activities of an Iranian threat group,...
Ex-Disney Worker Accused of Hacking Computer Menus to Add Profanities, Errors – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A former worker hacked servers at Walt Disney World after being fired in order to manipulate computer menus by changing...
Get details right to safely implement DANE in Exchange Online, warn experts – Source: www.csoonline.com
Source: www.csoonline.com – Author: Experts welcome Microsoft’s announcement that Exchange Online can now handle Inbound SMTP DANE with DNSSEC to improve email security, but admins may...
Download the AI in the Enterprise (for Real) Spotlight – Source: us.resources.csoonline.com
Source: us.resources.csoonline.com – Author: Register Download the November 2024 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, InfoWorld, and Network World. See...
Introducing Hacker Dashboard: Your personalized HackerOne overview – Source:www.hackerone.com
Source: www.hackerone.com – Author: Martijn Russchen. Earlier this month, we introduced the all-new Program Directory with a fresh set of metrics and better filtering. Now, we’re...
Fired Disney worker accused of hacking into restaurant menus, replacing them with Windings and false peanut allergy information – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A disgruntled former Disney employee is facing charges that he hacked into the company’s restaurant menu systems and wreaked havoc...
Virginia State University SWE: Supporting Collegians in STEM Fields
Alicia Williamson, president of the Virginia State University SWE Affiliate, shares the innovative academic, social, and career readiness activities that VSU SWE has held on campus....
Celebrating National Native American Heritage Month With SWE
To mark the occasion, Society of Women Engineers (SWE) has compiled some of our top blog posts, podcast episodes, and magazine articles sharing the community’s stories...
Inclusion Is Innovation: How Microsoft Empowers Female Tech Leaders
Discover how Microsoft’s diverse workforce and inclusive culture drives innovation and creativity for women engineers. Views: 0
Exploring the U.S. Space Force: A New Era for Space Operations
Learn how the U.S. Space Force aligns with innovation and opportunity for engineers in this Q&A article. Views: 0
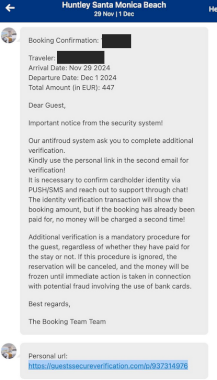
Booking.com Phishers May Leave You With Reservations – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story...
IoT Security Failures Can Be Sh*tty – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Gallagher It’s hard not to see IoT security failures in the news because they can be dramatic, and this week was...
DEF CON 32 – Welcome to DEF CON 32 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » DEF CON 32 – Welcome to DEF CON 32 by Marc...
GreyNoise: AI’s Central Role in Detecting Security Flaws in IoT Devices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Threat researchers at cybersecurity firm GreyNoise Intelligence discovered two security vulnerabilities in live-streaming cameras used in such sectors as industrial...
October Recap: New AWS Sensitive Permissions and Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Karen Levy As AWS continues to evolve, new services and permissions are frequently introduced to enhance functionality and security. This blog provides...
Cybersecurity Vulnerability News: October 2024 CVE Roundup – Source: securityboulevard.com
Source: securityboulevard.com – Author: Security Insights Team Keep Your Organization Safe with Up-to-Date CVE Information Cybersecurity vulnerability warnings from the National Institute of Standards and Technology...
Stop Supply Chain Invaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland The post Stop Supply Chain Invaders appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise. *** This...
Getting the Gist of CJIS – 5.9.5 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland What’s New in CJIS 5.9.5 as it Relates to Firmware Security? n the latest CJIS Security Policy, the FBI is...
Why Supply Chain Security Demands Focus on Hardware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Supply chain security for servers, PCs, laptops, and devices has correctly focused on protecting these systems from vulnerabilities introduced through...
ATT&CK v16: Worry-Free Updates in Tidal Cyber – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tidal Cyber We are thrilled to share that we have migrated Tidal Cyber’s Community & Enterprise platforms to v16 of MITRE ATT&CK®...
Microsoft’s Controversial Recall Feature Release Delayed Again – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt It’s going to be at least another month or more before Microsoft’s much-debated Recall feature for new Copilot+ PCs is...
Chinese Hackers Use Quad7 Botnet for Credential Theft – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Security Operations Hackers Using Password Spraying to Steal User Microsoft Account Credentials Akshaya Asokan (asokan_akshaya) • November 1, 2024 Image:...
Everfox Deepens Cyber Case Management Expertise with Yakabod – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Governance & Risk Management , Incident & Breach Response , Insider Threat Yakabod Deal to Strengthen Everfox’s Insider Risk, Cyber Incident Response...
Doctor Hit With $500K HIPAA Fine: Feds Worse Than Hacker – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Fraud Management & Cybercrime , Healthcare , HIPAA/HITECH Plastic Surgeon Paid $53K Ransom But Says ‘the Real Criminal’ Is HHS Marianne Kolbasuk...
Unfolding the Complexity of the AI Supply Chain: Securing the Pipeline – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: AI-Driven Security Operations , The Future of AI & Cybersecurity Presented by Palo Alto Networks 60 minutes The...
Verizon’s Trusted Connection Boosts Mid-Market Cybersecurity – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Making the Case for Stronger Mid-Market Cybersecurity Beth Cohen • November 1, 2024 Image: Shutterstock In a small Northeastern U.S....
EmeraldWhale’s Massive Git Breach Highlights Config Gaps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Tithi Luadthong via Alamy Stock Photo Earlier this week, researchers uncovered a major cybercriminal operation,...