The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Month: November 2024
Live Webinar | Harnessing Google Cloud Data & Analytics with GenAI: Transforming Insights into Action – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Artificial Intelligence & Machine Learning , Big Data Security Analytics , Cloud Data Security & Resilience Presented by LTI Mindtree Ltd ...
Live Webinar | Reimagine Your Cloud Transformation Journey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Application Security , Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Presented by LTI Mindtree Ltd 60...
Engaging with Boards to improve the management of cyber security risk.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2024 State of Multicloud Security Report by Microsoft Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Inside the Mind of a CISO 2024 The Evolving Roles of Security Leaders 2024 by bugcrowd
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Wie Business Integration die Cybersicherheit stärkt – Source: www.csoonline.com
Source: www.csoonline.com – Author: How-to 03 November 20244 Minuten Artificial Intelligence Viele Unternehmen kämpfen mit den wachsenden Herausforderungen in der Cybersicherheit. Business Integration kann helfen. Lesen...
5 Top Cybersecurity-Zertifizierungen: So pushen Sie Ihre CISO-Karriere – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cybersecurity-Zertifizierungen sind zwar keine Voraussetzung für den Job. Sie können jedoch den Lebenslauf von CISOs aufwerten und der Karriere einen Schub geben....
DEF CON 32 – Where’s The Money-Defeating ATM Disk Encryption – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Where’s The Money-Defeating ATM Disk Encryption Authors/Presenters: Matt Burch Our...
Cybersecurity Strong Strategy step by step Guide collected by Mohammad Alkhudari 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO’s Playbookto Cloud Security by Lacework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ten Strategies of a World-Class Cybersecurity Operations Center by MITRE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Identity Has Become the Prime Target of Threat Actors by Silverfort AIG.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
6 IT contractors arrested for defrauding Uncle Sam out of millions – Source: go.theregister.com
Source: go.theregister.com – Author: Brandon Vigliarolo in brief The US Department of Justice has charged six people with two separate schemes to defraud Uncle Sam out...
Oath Bug Bounty Program Update: $1M in payouts and expansion of the program – Source:www.hackerone.com
Source: www.hackerone.com – Author: Katrina Dene. This blog was written by Oath CISO and Paranoid in Chief Chris Nims and originally published on Oath.com. A little more...
Noma Security Raises $32 Million to Safeguard Gen-AI Applications – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Tel Aviv, Israel based Noma Security has emerged from stealth mode with $32 million in Series A funding led by...
DEF CON 32 – On Your Ocean’s 11 Team, I’m The AI Guy (Technically Girl) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – On Your Ocean’s 11 Team, I’m The AI Guy (Technically...
How Can FSOs Help with CMMC Compliance? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh As of now, the final rule for the Cybersecurity Maturity Model Certification has been published. The clock is ticking for...
Highlights of New York’s Cybersecurity Regulation 23 NYCRR Part 500 – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. September 4, 2018 – Eighteen month transitional period ends. Covered Entities are required to be in compliance with the requirements of...
Financial institutions told to get their house in order before the next CrowdStrike strikes – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones The UK’s finance regulator is urging all institutions under its remit to better prepare for IT meltdowns like that of...
The AWS Shared Responsibility Model: 3 Areas of Improvement to Make Today Part 3: Logging, Monitoring, and Alerting in AWS – Source:www.hackerone.com
Source: www.hackerone.com – Author: Justin Boyer. In the last two parts of this series, we discussed the AWS Shared Responsibility Model. We started with keeping your...
Normalyze to be purchased by Proofpoint – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Data Security, Mergers and Acquisitions October 30, 2024 San Francisco-based data security posture management firm Normalyze is set to be acquired by...
Proofpoint Expands Data Security With Normalyze Acquisition – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Data Loss Prevention (DLP) , Endpoint Security Normalyze’s AI-Powered DSPM Technology Boosts Proofpoint’s Data Visibility, Control Michael Novinson (MichaelNovinson) • October 29,...
Friday Squid Blogging: Squid Sculpture in Massachusetts Building – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Discovering programs is easier than ever with the new and improved Program Directory – Source:www.hackerone.com
Source: www.hackerone.com – Author: Martijn Russchen. Today, we’re excited to announce an overhaul of the HackerOne Program Directory! Since its launch, Hackers have been using the...
Chinese Hackers Use Quad7 Botnet for Credential Theft – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Security Operations Hackers Using Password Spraying to Steal User Microsoft Account Credentials Akshaya Asokan (asokan_akshaya) • November 1, 2024 Image:...
Everfox Deepens Cyber Case Management Expertise with Yakabod – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Governance & Risk Management , Incident & Breach Response , Insider Threat Yakabod Deal to Strengthen Everfox’s Insider Risk, Cyber Incident Response...
Doctor Hit With $500K HIPAA Fine: Feds Worse Than Hacker – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Fraud Management & Cybercrime , Healthcare , HIPAA/HITECH Plastic Surgeon Paid $53K Ransom But Says ‘the Real Criminal’ Is HHS Marianne Kolbasuk...
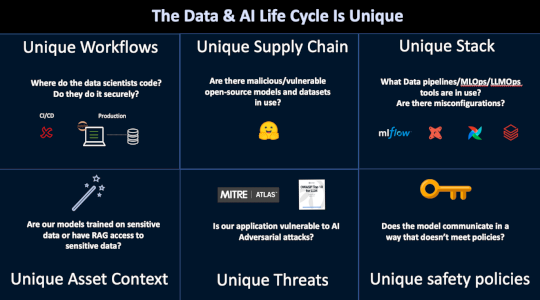
Unfolding the Complexity of the AI Supply Chain: Securing the Pipeline – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: AI-Driven Security Operations , The Future of AI & Cybersecurity Presented by Palo Alto Networks 60 minutes The...
Verizon’s Trusted Connection Boosts Mid-Market Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Making the Case for Stronger Mid-Market Cybersecurity Beth Cohen • November 1, 2024 Image: Shutterstock In a small Northeastern U.S....