Source: securityboulevard.com – Author: Paul Horn In today’s data-driven landscape, sensitive information—like PII (Personally Identifiable Information), PHI (Protected Health Information), and PCI (Payment Card Information)—sprawls across...
Month: November 2024
Google Cloud: MFA Will Be Mandatory for All Users in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Google is making multi-factor authentication (MFA) mandatory for all Google Cloud users in a phased rollout that starts this month...
DEF CON 32 – Your AI Assistant Has A Big Mouth: A New Side Channel Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, November 6, 2024 Home » Security Bloggers Network » DEF CON 32 – Your AI Assistant Has A Big...
Beyond Secrets Managers: 5 Alternatives for Securing Non-Human Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Kaplan Secrets managers have long been a reliable solution for safeguarding sensitive credentials like API keys, certificates, and tokens. For many...
Daniel Stori’s Turnoff.US: ‘Stranger Things – In The Sysadmin’s World’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
BTS #41 – Pacific Rim – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland In this episode, Paul Asadorian, Larry Pesce, and Evan Dornbush delve into the recent Sophos reports on threat actors, particularly...
CyberEdBoard Profiles in Leadership: Martyn Booth – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Leadership & Executive Communication , Training & Security Leadership , Video Dunhumby CISO on Building Resilience and Tackling Transformation Anna Delaney (annamadeline)...
Meta Loosens AI Rules for US Military Use – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Policy Shift Allows Military Contractors, Security Agencies Access to its AI...
Trump’s Return: Impact on Health Sector Cyber, HIPAA Regs – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: HIPAA/HITECH , Standards, Regulations & Compliance Experts on Potential Data Security and HIPAA Privacy Changes in Trump’s Second Term Marianne Kolbasuk McGee...
CrowdStrike Bolsters SaaS Security With Adaptive Shield Buy – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Endpoint Detection & Response (EDR) , Identity & Access Management , Next-Generation Technologies & Secure Development Purchasing Israeli Startup Will Expand SaaS...
Live Webinar | When AI Becomes Doctor, Nurse, and Security Guard – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Presented by Proofpoint 60 minutes Explore how artificial intelligence is revolutionizing healthcare by enhancing patient care, bolstering cybersecurity,...
10 Key Cyber Policy Questions as Trump Preps for Presidency – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Standards, Regulations & Compliance Burning Issues Include Russian Hacking, China’s Hitting Critical...
Keep Learning or Keep Losing: There’s No Finish Line – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Professional Certifications & Continuous Training , Training & Security Leadership Security Professionals Must Continually Hone Technical and Communication Skills Brandy Harris •...
Wie Hacker ML für Angriffe nutzen – Source: www.csoonline.com
Source: www.csoonline.com – Author: KI und maschinelles Lernen helfen Security-Teams, schneller auf Cyberbedrohungen zu reagieren. Aber auch Cyberkriminelle nutzen die Technik für größere und komplexere Angriffe....
Schneider Electric suffers data breach, exposing critical project and user data – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hackers have demanded $125,000 ransom in “baguettes” following Schneider’s third data breach in two years, spotlighting security concerns on the day the...
Was your last DocuSign-ed bill legitimate? Check again – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 06 Nov 20242 mins APIsPhishing A novel phishing campaign abuses DocuSign APIs to send fake invoices at scale. Threat actors are...
Nokia-Daten im Darknet aufgetaucht – Source: www.csoonline.com
Source: www.csoonline.com – Author: In einem Hackerforum werden Quellcode und andere sensible Daten von Nokia zum Verkauf angeboten. JRdes – Shutterstock.com Der bekannte Bedrohungsakteur IntelBroker behauptet...
Kicking dependency: Why cybersecurity needs a better model for handling OSS vulnerabilities – Source: www.csoonline.com
Source: www.csoonline.com – Author: Most organizations are still immature when it comes to identifying open-source dependencies that can usher in a host of problems when dealing...
Microsoft Authenticator passkey support to be native in January – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 05 Nov 20248 mins AuthenticationIdentity Management Solutions In statements that some labeled vague and confusing, Microsoft further embraced passkeys — and...
Teams, Slack & Co. absichern: So wird das Collaboration-Tool kein Security-Albtraum – Source: www.csoonline.com
Source: www.csoonline.com – Author: Einige der aktuell beliebtesten und nützlichsten Plattformen für den Informationsaustausch lassen unter Sicherheitsaspekten viel zu wünschen übrig. Hier sind einige der Probleme...
Man arrested in Canada allegedly linked to Snowflake data thefts – Source: www.csoonline.com
Source: www.csoonline.com – Author: US requested the arrest and extradition of a man accused of the Ticketmaster and AT&T hacks. Canadian authorities responding to a US...
Canadian Man Arrested in Snowflake Data Extortions – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A 26-year-old man in Ontario, Canada has been arrested for allegedly stealing data from and extorting more than 160 companies that...
What Is a VPN? Definition, How It Works, and More – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares VPNs encrypt your online traffic and allow you to change your IP address, making it appear as if you’re in...
How to Become a Chief Information Officer: CIO Cheat Sheet – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Business leaders are responsible for guiding a company and its employees toward successful goals. To accomplish this, leaders must hire...
Hacker-Powered pen tests at the U.S. Federal Government – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. When looking for a model to inform your own security posture, the Department of Defense would be a good place to...
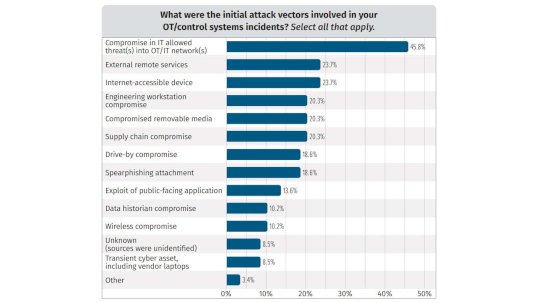
Attackers Breach IT-Based Networks Before Jumping to ICS/OT Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jennifer Lawinski, Contributing Writer Attacks against industrial control systems and operations technology systems are increasing, as adversaries find weaknesses in IT networks...
How to Outsmart Stealthy E-Crime and Nation-State Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Adam Meyers Adam Meyers, Senior Vice President of Counter Adversary Operations, CrowdStrike November 6, 2024 4 Min Read Source: Andrey Khokhlov via...
Canadian Authorities Arrest Attacker Who Stole Snowflake Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: GK Images via Alamy Stock Photo Canadian authorities arrested Alexander “Connor” Moucka, whom they believe orchestrated a malicious...
Attacker Hides Malicious Activity in Emulated Linux Environment – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Computer display with obfuscated codeSource: Grenar via Shutterstock Among the many constantly evolving tactics that threat actors are...
Android Botnet ‘ToxicPanda’ Bashes Banks Across Europe, Latin America – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Oneinchpunch via Alamy Stock Photo Researchers have designated a new botnet on the scene —...