As part of their AG spotlight month, the Indigenous Peoples AG showcases their two co-chairs, two Indigenous women in engineering. Views: 0
Month: November 2024
SWENext Influencers: Meet Sophia Z.
Sophia is a SWENext Influencer who is passionate about showcasing STEM to young girls. Learn how she is advancing innovation in her community, including through an...
Respond to Fewer Alerts with Automated Grouping – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim Isn’t it annoying when multiple alerts are clearly related, but you can’t easily consolidate them into a single incident? This...
How to Motivate Employees and Stakeholders to Encourage a Culture of Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Courtney Chatterton Cybersecurity impacts us all. Third parties process and handle data every day, whether they’re tapping your phone to pay via...
Microsoft Adds Raft of Zero-Trust Tools and Platforms – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Microsoft this week launched a raft of cybersecurity initiatives that address everything from making Windows platforms more secure to adding...
Shift Left and Shift Up Workload Attack Surface Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Robert Levine Executive Summary: In today’s security landscape, the concept of a hardened perimeter is increasingly insufficient. With the rise of hybrid...
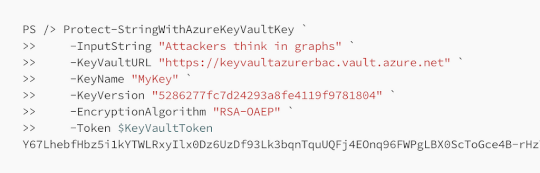
Azure Key Vault Tradecraft with BARK – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Brief This post details the existing and new functions in BARK that support adversarial tradecraft research relevant to the Azure...
Microsoft Veeps Ignite Fire Under CrowdStrike – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Redmond business leaders line up to say what’s new in Windows security. Microsoft vice presidents David “dwizzzle” Weston (pictured) and Pavan...
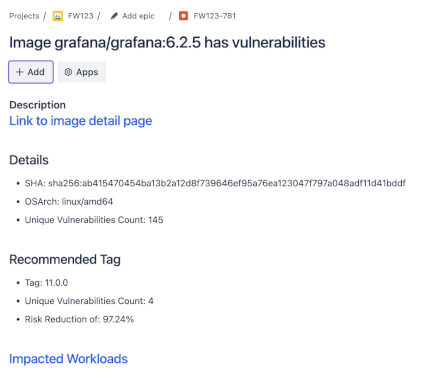
Fairwinds Insights Release Notes 16.1.11 – 16.2.4: CVE Mapping Updates – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dexter Garner Over the last few months, we’ve been working on making a number of meaningful updates to Fairwinds Insights. We’ve delivered...
CISOs Look to Establish Additional Leadership Roles – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy As cybersecurity challenges grow in complexity, chief information security officers (CISOs) are exploring new leadership roles to bolster their teams....
China’s ‘Liminal Panda’ APT Attacks Telcos, Steals Phone Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Jakub Krechowicz via Alamy Stock Photo A newly unveiled threat actor has been spying on mobile phones...
Alleged Ford ‘Breach’ Encompasses Auto Dealer Info – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo On Nov. 17, hackers that go by the aliases...
Apple Urgently Patches Actively Exploited Zero-Days – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Shahid Jamil via Alamy Stock Photo Apple has released security updates to address two zero-day vulnerabilities that are...
Small US Cyber Agencies Are Underfunded & That’s a Problem – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Daniel Michael Daniel, President & CEO, Cyber Threat Alliance November 20, 2024 5 Min Read Source: Skorzewiak via Alamy Stock Photo...
‘Water Barghest’ Sells Hijacked IoT Devices for Proxy Botnet Misuse – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Jiraroj Praditcharoenkul via Alamy Stock Photo A cybercriminal group is exploiting vulnerabilities in Internet of Things (IoT)...
African Reliance on Foreign Suppliers Boosts Insecurity Concerns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: CG Alex via Shutterstock Every night for five years, computers and network appliances from the headquarters of...
DeepTempo Launches AI-Based Security App for Snowflake – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Soure: Zoonar GmbH via Alamy Stock Photo Organizations are harnessing artificial intelligence (AI) to boost their security teams’ productivity...
RIIG Launches With Risk Intelligence Solutions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Olekcii Mach via Alamy Stock Photo As cyber threats get more sophisticated and the volume of attacks increase,...
SWEEPS Educational Initiative Offers Application Security Training – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jennifer Lawinski, Contributing Writer Source: Simon Turner via Alamy Stock Photo A coalition of universities, community colleges, and cybersecurity organizations has launched...
Name That Toon: Meeting of Minds – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist We love the work-from-anywhere trend, but we have to ask, what’s so important about this meeting? Send us a...
Fintech Giant Finastra Investigating Data Breach – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The financial technology firm Finastra is investigating the alleged large-scale theft of information from its internal file transfer platform, KrebsOnSecurity has...
Five Privilege Escalation Flaws Found in Ubuntu needrestart – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Five Local Privilege Escalation (LPE) vulnerabilities in Ubuntu Server’s needrestart utility have been discovered. These flaws, found by the Qualys Threat Research Unit...
60% of Emails with QR Codes Classified as Spam or Malicious – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: New cybersecurity findings have revealed that approximately 60% of emails containing QR codes are classified as spam, with a smaller subset being...
Chinese APT Group Targets Telecom Firms Linked to Belt and Road Initiative – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Cyber intrusions affecting telecom providers previously attributed to the Chinese hacking group LightBasin (UNC1945) are now believed to come from another Chinese-sponsored...
Apple Issues Emergency Security Update for Actively Exploited Vulnerabilities – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Apple has urged customers to apply emergency security updates, which fixes two actively exploited vulnerabilities on its devices. The fixes are included...
OWASP Warns of Growing Data Exposure Risk from AI in New Top 10 List for LLMs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Sensitive information disclosure via large language models (LLMs) and generative AI has become a more critical risk as AI adoption surges, according...
Hackers Hijack Jupyter Servers for Sport Stream Ripping – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Security researchers have uncovered a surprising new attack methodology for illegal sports streaming, which uses hijacked Jupyter servers. Aqua Security threat hunters...
One Deepfake Digital Identity Attack Strikes Every Five Minutes – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Fraudsters are using deepfake technology with growing frequency to help them bypass digital identity verification checks, Entrust has warned. The identity security...
Cybercriminals Exploit Weekend Lull to Launch Ransomware Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Ransomware gangs are increasingly targeting weekends and holidays, when cybersecurity teams are typically less staffed, according to a new report from Semperis....
Erneute Phishing-Attacke auf IHK-Unternehmen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hacker versuchen erneut an Daten von IHK-Unternehmen zu gelangen. janews – Shutterstock.com Cyberkriminelle lassen sich immer wieder neue Tricks einfallen, um an...