Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: JHVEPhoto via Shutterstock Very swiftly after disclosing them, Citrix has issued patches for two vulnerabilities in its...
Day: November 13, 2024
Citrix ‘Recording Manager’ Zero-Day Bug Allows Unauthenticated RCE – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Brian Jackson via Alamy Stock PhotoSource: [Ed. note, Nov. 12 at 12:30 p.m. ET:...
Halliburton Optimistic Amid $35M Data Breach Loss – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Todd Strand via Alamy Stock Photo Halliburton, a multinational corporation known for its oil and gas products and...
Interlock Ransomware Detection: High-Profile and Double-Extortion Attacks Using a New Ransomware Variant – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Adversaries employ new Interlock ransomware in recently observed big-game hunting and double-extortion attacks against U.S. and European organizations in multiple...
The CISO paradox: With great responsibility comes little or no power – Source: www.csoonline.com
Source: www.csoonline.com – Author: Opinion 13 Nov 20246 mins CSO and CISOIT GovernanceIT Leadership Chief information security officers don’t have full command over their domains but...
9 unverzichtbare Open Source Security Tools – Source: www.csoonline.com
Source: www.csoonline.com – Author: Tipp 12 November 20248 Minuten Open SourceSicherheitSicherheitssoftware Diese quelloffenen Werkzeuge sind für IT-Sicherheitsentscheider und ihre Teams essenziell. Diese Open-Source-Tools adressieren spezifische Security-Probleme...
Hackerangriff auf Berufsförderungswerk Oberhausen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Das Berufsförderungswerk Oberhausen ist Opfer einer Cyberattacke. Auszubildende können derzeit nicht an ihren Rechnern arbeiten. Juice Verve – Shutterstock.com Nach der Cyberattacke...
GUEST ESSAY: The promise and pitfalls of using augmented reality– ‘AR’ — in cybersecurity – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Iam Waqas Augmented reality use cases have become prevalent in our society. The technology, which first emerged primarily in the...
Hacking the U.S. Air Force (again) from a New York City subway station – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. New York City during the holidays. Magical. Bringing together hackers from around the world to legally hack the U.S. Air Force....
Patch Tuesday Update – November 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra CVE/Advisory Title Tag Microsoft Severity Rating Base Score Microsoft Impact Exploited Publicly Disclosed CVE-2024-43530 Windows Update Stack Elevation...
6 Ways to Save Money on CMMC Costs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Jamie Leupold The DoD’s CMMC Final Rule becomes effective on December 16, 2024, and requires organizations who handle...
DEF CON 32 – The Hack, The Crash And Two Smoking Barrels – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, November 12, 2024 Home » Security Bloggers Network » DEF CON 32 – The Hack, The Crash And Two...
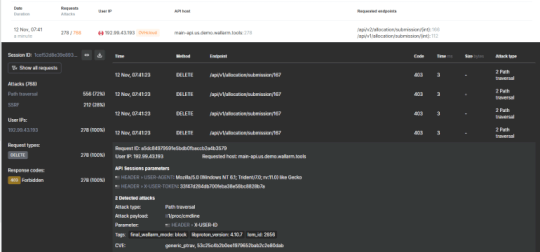
Context is King: Using API Sessions for Security Context – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tim Erlin There’s no doubt that API security is a hot topic these days. The continued growth in API-related breaches and increase...
Randall Munroe’s XKCD ‘Proterozoic Rocks’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored by Marc Handelman. Read the original post...
Scaling Global Protection: DataDome Expands to Over 30 Points of Presence (PoP) Worldwide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andrew Hendry At DataDome, our mission is clear: deliver unmatched bot protection with the highest performance standards for our customers. To this...
Is the latest book on “Pentesting APIs” any good? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp The folks over at Packt Publishing sent me a gift recently. It was a copy of one of their latest...
Infostealer Malware: An Introduction – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare Infostealer malware represents one of the most underrated threats to corporate and consumer information security today. These sophisticated remote access Trojans...
DEF CON 32 – Optical Espionage: Using Lasers to Hear Keystrokes Through Glass Windows – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, November 12, 2024 Home » Security Bloggers Network » DEF CON 32 – Optical Espionage: Using Lasers to Hear...
Fake IP checker utilities on npm are crypto stealers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ax Sharma Recently identified npm packages called “node-request-ip“, “request-ip-check” and “request-ip-validator“ impersonate handy open source utilities relied upon by developers to retrieve...
Top 5 Google Authenticator Alternatives in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Andrew Wan We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...