Source: www.databreachtoday.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes In today’s rapidly evolving cybersecurity...
Day: November 5, 2024
Your Salesforce Data, Your Responsibility: Best Practices for Data Protection – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes As a Salesforce admin, securing,...
Expert Insights: Securing Your Cloud Data Across the Attack Timeline – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes Get inside the mind of...
The Math Behind the Cyber Resilience Stack: A Three-Layered Defense Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes In today’s digital landscape, cyber...
Police Doxing of Criminals Raising Ransomware-Attack Stakes – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Fraud Management & Cybercrime , Ransomware Incident Responders Say Disruptions Help, See No Spike in Median Ransom Payments Mathew J. Schwartz (euroinfosec)...
How to Evaluate Enterprise Browser Vendors – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Assess Your Organization’s Needs for Manageability and Efficiency Features Jason Trunk • November 4, 2024 Image: Island Not all enterprise...
210,000 Impacted by Saint Xavier University Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Saint Xavier University last week started notifying over 210,000 individuals that their personal information was compromised in a data breach...
US Sentences Nigerian to 26 Years in Prison for Stealing Millions Through Phishing – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A Nigerian national was sentenced to 26 years in prison in the US for stealing millions by compromising the email...
Google Says Its AI Found SQLite Vulnerability That Fuzzing Missed – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Google says a large language model (LLM) project was able to discover a vulnerability in SQLite, and its researchers were...
FBI Seeking Information on Chinese Hackers Targeting Sophos Firewalls – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The FBI is asking for public help in identifying the hackers behind a years-long campaign targeting Sophos edge devices. The...
City of Columbus Ransomware Attack Impacts 500,000 People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The City of Columbus, Ohio, is notifying 500,000 individuals that their personal information was stolen in a July 2024 ransomware...
Siemens and Rockwell Tackle Industrial Cybersecurity, but Face Customer Hesitation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs SecurityWeek has talked to representatives of industrial giants Siemens and Rockwell Automation to find out how they help customers address...
Businesses Worldwide Targeted in Large-Scale ChatGPT Phishing Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Barracuda Networks has observed a large-scale OpenAI impersonation campaign targeting the credentials of ChatGPT users. Threat actors have been sending...
An Inspiring Day: Three SWE Affiliates in Spain Hold Their Annual SWE Event
Discover the panel discussions, speakers, and hot topics at the 2024 SWE event held at Universidad Carlos III de Madrid. Views: 2
FIDO: Consumers are Adopting Passkeys for Authentication – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt There appears to be growing momentum behind the use of passkeys as an alternative identity verification tool to passwords, with...
SLSA Framework: What is It and How to Gain Visibility – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gal Ofri In Part 2 of this blog series, we uncover the details of SLSA provenance from end to end. Previously in...
MDR vs. MSSP: Making the Right Choice for Your Business – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shriram Sharma Protecting against cyber threats with limited resources presents an insurmountable challenge for most organizations. Managed security service models, including managed...
DEF CON 32 – OH MY DC Abusing OIDC All The Way To Your Cloud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – OH MY DC Abusing OIDC All The Way To Your...
Securing your software supply chain with CISA’s new SBOM guidance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens With new and increasing cyber threats abound, navigating global software regulations and staying informed and compliant can seem like an...
PCI DSS v4.0.1 Changes | Application Security PCI Compliance Requirements | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Contrast Marketing The deadline to comply with the latest version of the Payment Card Industry Data Security Standard (PCI DSS), v4.0.1, is...
Carahsoft to Host Webinar on Ensuring ICAM Survivability for Access in Disconnected, Degraded, Intermittent, and Low-Bandwidth (DDIL) Environments – Source: securityboulevard.com
Source: securityboulevard.com – Author: Heidi King MEDIA ADVISORY Strata Identity, Saviynt, and Oxford Computer Group to Present Strategies for Identity Continuity at the Tactical Edge BOULDER,...
DEF CON 32 – The Edges Of Surveillance System And Its Supply Chain – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – The Edges Of Surveillance System And Its Supply Chain Authors/Presenters:...
Is your air fryer spying on you? Concerns over ‘excessive’ surveillance in smart devices – Source: www.theguardian.com
Source: www.theguardian.com – Author: Robert Booth UK technology editor Air fryers that gather your personal data and audio speakers “stuffed with trackers” are among examples of...
APT36 Refines Tools in Attacks on Indian Targets – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Mehaniq vis Shutterstock Pakistan’s APT36 threat group is using a new and improved version of its core...
Okta Fixes Auth Bypass Bug After 3-Month Lull – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Ahmed Zaggoudi via Alamy Stock Photo Okta has addressed an authentication bypass bug that affects those with long...
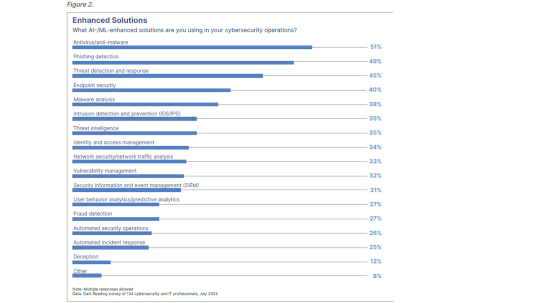
Antivirus, Anti-Malware Lead Demand for AI/ML Tools – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Artificial intelligence and machine learning tools are gaining traction in enterprises, and the rate of adoption is particularly notable...
OWASP Beefs Up GenAI Security Guidance Amid Growing Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Family Stock via Shutterstock Deepfakes and other generative artificial intelligence (GenAI) attacks are becoming less rare, and...
Google: Big Sleep AI Agent Puts SQLite Software Bug to Bed – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Krot Studio via Alamy Stock Photo Google has discovered its first real-world vulnerability using an artificial intelligence...
Name That Edge Toon: Aerialist’s Choice – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist When you let go of that trapeze, you really want your teammates to be ready to catch you. Send...
Can Automatic Updates for Critical Infrastructure Be Trusted? – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Paul Cunningham Source: Lasse Kristensen via Alamy Stock Photo COMMENTARY In July, the industry witnessed one of the largest technology outages...