Source: www.databreachtoday.com – Author: Data Loss Prevention (DLP) , Endpoint Security Normalyze’s AI-Powered DSPM Technology Boosts Proofpoint’s Data Visibility, Control Michael Novinson (MichaelNovinson) • October 29,...
Day: October 30, 2024
Live Webinar | SD-WAN 3.0: APAC’s Next Phase of Network Transformation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cloud Next-Generation Firewall , Network Firewalls, Network Access Control , Security Operations Presented by Tata Communications 60mins The...
WhiteRabbitNeo: High-Powered Potential of Uncensored AI Pentesting for Attackers and Defenders – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The latest release of WhiteRabbitNeo (version 2.5) represents a leap forward in cybersecurity and DevSecOps. This generative AI tool—now available on...
Back to the Future, Securing Generative AI – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matt Honea Over the last 10 years, the top jobs in data analysis have evolved from statistics and applied modeling, into actuarial...
Recent Version of LightSpy iOS Malware Packs Destructive Capabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A recent iOS-targeting version of the LightSpy malware includes over a dozen new plugins, many with destructive capabilities, according to...
Google Patches Critical Chrome Vulnerability Reported by Apple – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Google and Mozilla on Tuesday announced security updates for their Chrome and Firefox web browsers, and some of the vulnerabilities...
Synology, QNAP, TrueNAS Address Vulnerabilities Exploited at Pwn2Own Ireland – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Synology, QNAP and TrueNAS have started patching and mitigating the vulnerabilities exploited recently at Pwn2Own Ireland 2024. Participants earned a...
Italian Politicians Express Alarm at Latest Data Breach Allegedly Affecting 800,000 Citizens – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Italian politicians called Monday for better protection of citizens’ online data following a probe into a hacking scheme that allegedly...
Proofpoint to Acquire Data Security Posture Management Firm Normalyze – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Enterprise cybersecurity giant Proofpoint announced on Tuesday that it has signed a definitive agreement to acquire data security posture management...
RedLine and Meta Infostealers Disrupted by Law Enforcement – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Law enforcement agencies in six countries this week announced disrupting the infrastructure associated with the RedLine and Meta infostealers. The...
Building Resilience: A Post-Breach Security Strategy for Any Organization – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the wake of a recent breach that compromised sensitive information, a healthcare organization sought my guidance on how to...
The 8 Best Network Monitoring Tools for 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jonathan Kalibbala Best overall: Progress WhatsUp Gold Best bare bones option: Cacti Best for growing companies: Nagios XI Best for device flexibility:...
Law Enforcement Deanonymizes Tor Users – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Schneier on Security Menu Blog Newsletter Books Essays News Talks Academic About Me HomeBlog The German police have successfully deanonymized...
UK Depends on Foreign Investment for AI, Hindering Scale – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Geo Focus: The United Kingdom , Geo-Specific Scaling Business Often a Challenge in the Country, Experts...
Election Threats Escalating as US Voters Flock to the Polls – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Election Security , Fraud Management & Cybercrime Foreign Influence Campaigns Intensify as Experts Tout Election Security Upgrades Chris Riotta (@chrisriotta) • October...
Private Firm Accessed Italian Govt Database: Prosecutors – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cybercrime , Fraud Management & Cybercrime Foreign Minister Tajani Condemns Conspiracy as ‘Threat to Democracy’ Akshaya Asokan (asokan_akshaya) • October 29, 2024...
Proofpoint Expands Data Security With Normalyze Acquisition – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Data Loss Prevention (DLP) , Endpoint Security Normalyze’s AI-Powered DSPM Technology Boosts Proofpoint’s Data Visibility, Control Michael Novinson (MichaelNovinson) • October 29,...
How PowerSchool Builds Their AI/ML Apps with Snowflake – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Presented by Snowflake 60 Minutes Snowflake provides the data foundation and building blocks for enterprise AI and Applications....
Why Shoring Up Cyber at Rural and Small Hospitals Is Urgent – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: When a large hospital in an urban area is shut down by ransomware, the IT disruption can be significant, but when a...
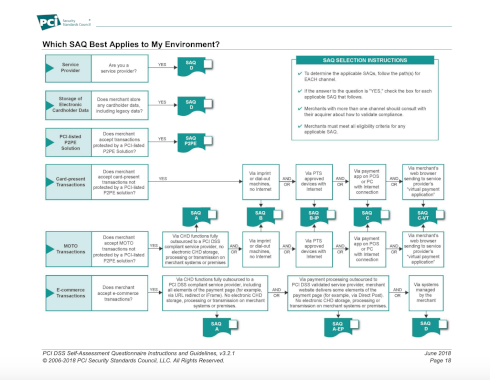
PCI DSS Self-Assessment Questionnaires: Choosing the Right Type – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security If you process credit card payments, you need to prioritize security. One way to guarantee this safety is by complying...
PCI DSS Compliance Levels and Requirements: A Complete Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security If your business processes credit card transactions, it needs to meet the Payment Card Industry (PCI) Data Security Standards (DSS)....
An Introduction to Operational Relay Box (ORB) Networks – Unpatched, Forgotten, and Obscured – Source: securityboulevard.com
Source: securityboulevard.com – Author: S2 Research Team Although not a new concept, Operational Relay Box (ORB) networks—often referred to as “covert,” “mesh,” or “obfuscated” networks—are becoming...
What Is Secrets Management? Best Practices and Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Modern apps require hundreds of secrets to function (API keys, cloud credentials, etc.). However, poor management of these secrets can...
Aembit Introduces Google Workload Identity Federation Support – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ashur Kanoon Aembit today announced support for Google Workload Identity Federation (WIF). While Google WIF issues short-lived security tokens for accessing GCP...
Test Data Management Best Practices: Handling Sensitive Data Across Multiple Databases – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Horn Handling large volumes of sensitive data in testing environments is challenging. You need to protect customer information, financial records, and...
DEF CON 32 – AppSec Village – Got 99 Problems But Prompt Injection Ain’t Watermelon – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, October 29, 2024 Home » Cybersecurity » Application Security » DEF CON 32 – AppSec Village – Got 99...
Daniel Stori’s Turnoff.US: ‘Security Engineer Interview’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
Lessons from the Cisco Data Breach—The Importance of Comprehensive API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Schwake In the wake of Cisco’s recent data breach involving exposed API tokens – amongst other sensitive information – the cybersecurity...
SWE Diverse Podcast Ep 285: Thriving in Engineering While Living With Disabilities
Members of the SWE DisAbility Inclusion Affinity Group share their stories of self-advocacy, thoughts on disclosing disabilities at work, and recommended disability inclusion resources for engineers....
Recurring Windows Flaw Could Expose User Credentials – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: tdhster via Shutterstock All versions of Windows clients, from Windows 7 through current Windows 11 versions, contain...