The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: June 19, 2024
INCIDENT REPORTING TEMPLATE
The Incident Response Form captures essential details related to incident management within an organization. It includes sections such as Incident Response Details, Incident Report Information, Incident...
UK Pathology Lab Ransomware Attackers Demanded $50 Million – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Russian-Speaking Gang Follows Typical Playbook; Critical Services Still Disrupted Mathew J. Schwartz (euroinfosec) • June...
Researchers Uncover Chinese Hacking Cyberespionage Campaign – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Chinese Threat Actor ‘Velvet Ant’ Evaded Detection...
Chemical Firms Boost Cybersecurity Ahead of New Regulations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Leadership & Executive Communication , Training & Security Leadership New Report Finds Chemical Firms Are Investing in...
IMF Touts Fiscal Policy Change, Taxes to Soften AI Impact – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Governance & Risk Management , Next-Generation Technologies & Secure Development Agency Suggests Taxing AI-Related Carbon...
Incident Response Recommendations and Considerations for Cybersecurity Risk Management
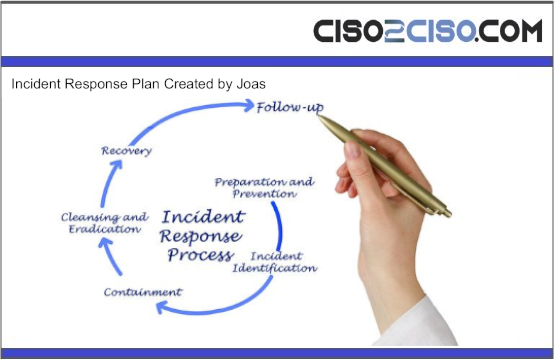
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
From plan to deployment: Implementing a cloud-native application protection platform(CNAPP) strategy
The document emphasizes the importance of Cloud Security Posture Management (CSPM) and the utilization of Defender for Cloud to enhance security measures. It highlights the need...
Identity and Access Management Policy
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...