Source: www.cybertalk.org – Author: slandau With more than 15 years of experience in cyber security, Manuel Rodriguez is currently the Security Engineering Manager for the North...
Month: May 2024
What American Enterprises Can Learn From Europe's GDPR Mistakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Apu Pavithran 4 Min Read Source: Egor Kotenko via Alamy Stock Photo After almost a decade of “will they or won’t they,”...
Android Banking Trojan Antidot Disguised as Google Play Update – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: the lightwriter via Alamy Stock Photo A banking Trojan impacting Google Android devices, dubbed “Antidot” by the...
IBM Sells Cybersecurity Group – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier IBM is selling its QRadar product suite to Palo Alto Networks, for an undisclosed—but probably surprisingly small—sum. I have a...
Strata’s Maverics Platform Provides Zero Downtime for Cloud-based Identity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Heidi King Multi-cloud Identity Orchestration platform ensures continuous access to applications even when a primary identity provider (IDP) is unavailable BOULDER, Colo.,...
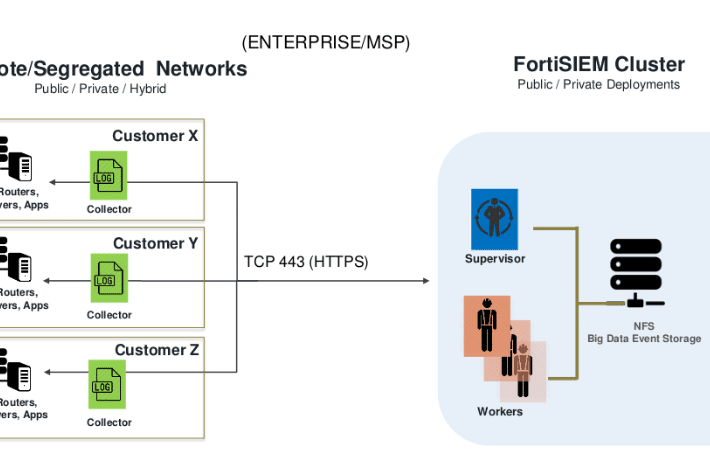
CVE-2023-34992: Fortinet FortiSIEM Command Injection Deep-Dive – Source: securityboulevard.com
Source: securityboulevard.com – Author: Zach Hanley In early 2023, given some early success in auditing Fortinet appliances, I continued the effort and landed upon the Fortinet...
How to Manage IAM Compliance and Audits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rebecca Kappel Did you know that 80% of breaches exploit legitimate identities and are difficult to detect? It’s hard to tell a...
AlmaLinux 9.4 Released: Security and Legacy Hardware Support – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina AlmaLinux 9.4, codenamed “Seafoam Ocelot,” arrived on May 6, 2024. This exciting new release from the AlmaLinux OS Foundation closely...
RSAC Fireside Chat: SquareX introduces security-infused browser extension to stop threats in real time – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido The open-source Chromium project seeded by Google more than a decade ago has triggered something of a...
Scytale to Support ISO 42001, Ensuring Companies Sail Smoothly into AI Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mor Avni, Product Manager, Scytale In an era marked by rapid advancements in artificial intelligence (AI), regulatory landscapes are evolving at a...
New Tracker Warning Features on iPhones & Androids, 2024 Verizon Data Breach Investigations Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Eston In episode 330 Tom, Scott, and Kevin discuss the new features for iPhones and Android phones designed to warn users...
USENIX Security ’23 – Guarding Serverless Applications with Kalium – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Guarding Serverless Applications with Kalium by Marc...
Antivirus Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Antivirus software is critical to ensure information security of organizational networks and resources. By establishing an antivirus policy, organizations can quickly identify...
AI’s Energy Appetite: Challenges for Our Future Electricity Supply – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity The dramatic growth in GenAI and AI adoption is bringing increased demand for energy to power data centers. Where...
USENIX Security ’23 – Controlled Data Races In Enclaves: Attacks And Detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Controlled Data Races In Enclaves: Attacks And...
London Drugs cyber attack: What businesses can learn from its week-long shutdown – Source: securityboulevard.com
Source: securityboulevard.com – Author: James Tobias The London Drugs cyber attack has been making headlines throughout the country. What makes this breach unique, is the impact...
There Is No Cyber Labor Shortage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rex Booth 5 Min Read Source: Bryan Sikora via Alamy Stock Photo COMMENTARY The unfortunate truth is, if you’re looking for an...
What is Secure Code Review and How to Conduct it? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra Secure code review is a combination of automated and manual processes assessing an application/software’s source code. The main motive of...
Why Bot Management Should Be a Crucial Element of Your Marketing Strategy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Erez Hasson Marketing teams need a comprehensive bot management solution to address the challenges posed by bot traffic and protect marketing analytics....
Cloud Monitor Identifies and Remediates Problematic VPN Use in K-12 Districts – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexa Sander Recently, we hosted Michael Tapia, Chief Technology Director at Clint ISD in Texas, and Kobe Brummet, Cybersecurity Technician at Hawkins...
Brothers Indicted for Stealing $25 Million of Ethereum in 12 Seconds – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt It took two brothers who went to MIT months to plan how they were going to steal, launder and hide...
Votiro Keeps Up the Momentum in 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro On the heels of our launch of a unified, Zero Trust Data Detection & Response (DDR) platform, we’re happy to report...
Novel Threat Tactics, Notable Vulnerabilities, and Current Trends for April 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pondurance Every month, the Pondurance team hosts a webinar to keep clients current on the state of cybersecurity. In April, the team...
USENIX Security ’23 – AEX-Notify: Thwarting Precise Single-Stepping Attacks Through Interrupt Awareness For Intel SGX Enclaves – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Scott Constable, Jo Van Bulck, Xiang Cheng, Yuan Xiao, Cedric Xing, Ilya Alexandrovich, Taesoo Kim, Frank Piessens, Mona Vij, Mark...
North Korea IT Worker Scam Brings Malware and Funds Nukes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Pictured: Several successful American IT professionals. The U.S. Justice Department says N. Korean hackers are getting remote IT jobs, posing as...
Response to CISA Advisory (AA24-131A): #StopRansomware: Black Basta – Source: securityboulevard.com
Source: securityboulevard.com – Author: Francis Guibernau On May 10, 2024, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), the Department of Health...
An Analysis of AI usage in Federal Agencies – Source: securityboulevard.com
Source: securityboulevard.com – Author: stackArmor From this we can see that all the agencies that we have inferred information about have a reasonable mix of initiatives...
CISO Corner: What Cyber Labor Shortage?; Trouble Meeting SEC Disclosure Deadlines – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Welcome to CISO Corner, Dark Reading’s weekly digest of articles tailored specifically to security operations...
Intel Discloses Max Severity Bug in Its AI Model Compression Software – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: flowgraph via Shutterstock Intel has disclosed a maximum severity vulnerability in some versions of its Intel Neural...
10 Ways a Digital Shield Protects Apps and APIs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joshua Goldfarb 5 Min Read Source: Sarayut Thaneerat via Alamy Stock Photo When network architectures were simpler, so was protecting apps and...