Source: www.proofpoint.com – Author: 1 To mitigate this area of vulnerability, 86% of CISOs in Canada are turning to AI-powered technology to protect against human error...
Month: May 2024
Proofpoint’s 2024 Voice of the CISO Report Reveals that Three-Quarters of CISOs Identify Human Error as Leading Cybersecurity Risk – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 To mitigate this area of vulnerability, 87% of CISOs are turning to AI-powered technology to protect against human error and block...
Report Reveals 341% Rise in Advanced Phishing Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security experts have reported a 341% increase in malicious phishing links, business email compromise (BEC), QR code and attachment-based threats in...
UserPro Plugin Vulnerability Allows Account Takeover – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UserPro plugin, a popular community and user profile tool for WordPress developed by DeluxeThemes, has been found to have a...
Fortifying Digital Health Against Cyber Attacks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Nissim Ben-Saadon, Director of Innovation, CYREBRO In today’s digital era, the healthcare industry stands at the forefront of technological...
A Consolidated Approach to Fraud: Bringing Together Risk Insights, Organizations and Technology – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Kimberly Sutherland, vice president, fraud and identity strategy, LexisNexis® Risk Solutions Digital fraud has seen a substantial increase in...
Cybersecurity or Cyber Resilience: Which Matters More? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Planning Beyond an Enterprise Security Posture and Toward Reliable Business Continuity By Amanda Satterwhite, Managing Director of Cyber Growth &...
23-year-old alleged founder of dark web Incognito Market arrested after FBI tracks cryptocurrency payments – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The United States Department of Justice has dealt a blow to dark web drug traffickers by arresting a man alleged...
Arrests made after North Koreans hired for remote tech jobs at US companies – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley US businesses are believed to have recruited thousands of North Korean IT workers, sending earnings (and potentially data) to North...
Criminal IP: Enhancing Security Solutions through AWS Marketplace Integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Torrance, United States / California, May 22nd, 2024, CyberNewsWire AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced today...
Lasso Security Data Protection Tool Aimed at GenAI Applications – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Lasso Security has released a custom policy wizard designed to help companies prevent data and knowledge leaks when they use...
Exploring the Role of ISO/IEC 42001 in Ethical AI Frameworks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ronan Grobler, Compliance Success Manager, Scytale Understanding ISO/IEC 42001 ISO/IEC 42001 provides guidance on building trust in AI systems. It offers a...
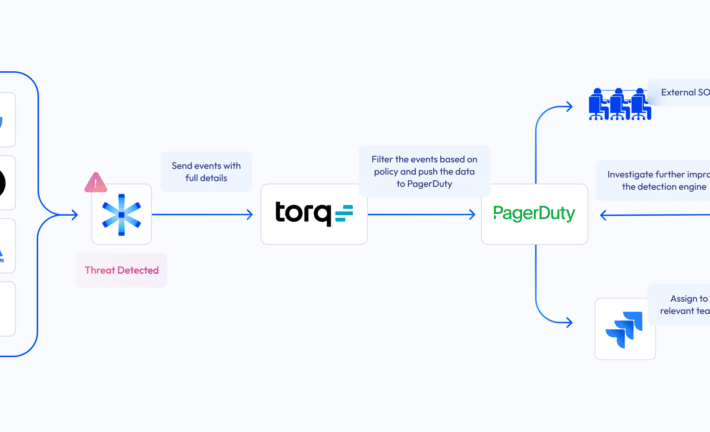
Bridging the NHI security gap: Astrix and Torq partner up – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Guetta While zero-trust policies and identity-centric programs excel at protecting user identities and login credentials with IAM policies and security tools...
Hackers Leverage AI as Application Security Threats Mount – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Threat actors increasingly are targeting monitored applications with active protection as they leverage low-code techniques and AI-powered tools to target...
Securing the Gateway: Why Protecting Build Systems Is Crucial in Modern Software Development – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joe Nicastro Understand why securing build systems is as important as securing production systems. Most organizations want to innovate quickly and efficiently....
FUD: How Fear, Uncertainty, and Doubt can ruin your security program – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden The role of fear Fear drives irrational and panicked decision-making, often leading individuals to prioritize short-term solutions over long-term security...
USENIX Security ’23 – Rods with Laser Beams: Understanding Browser Fingerprinting on Phishing Pages – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Iskander Sanchez-Rola, Leyla Bilge, Davide Balzarotti, Armin Buescher, Petros Efstathopoulos Many thanks to USENIX for publishing their outstanding USENIX...
SaaS BOM: The Advantage for Securing SaaS Ecosystems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Melissa Goldberger Introduction It’s not a secret that organizations are increasingly investing in software-as-a-service (SaaS) solutions. It’s not just about keeping pace...
Stealers, stealers and more stealers – Source: securelist.com
Source: securelist.com – Author: GReAT Introduction Stealers are a prominent threat in the malware landscape. Over the past year we published our research into several stealers...
Snapchat Revises AI Privacy Policy Following UK ICO Probe – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Geo Focus: The United Kingdom , Geo-Specific ICO Urges Companies to Assess Data Protection Before...
Training LLMs: Questions Rise Over AI Auto Opt-In by Vendors – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Few Restrictions Appear to Exist, Provided Companies Behave Transparently Mathew J. Schwartz (euroinfosec) • May 21, 2024 Image: Shutterstock...
Did OpenAI Illegally Mimic Scarlett Johansson’s Voice? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Actor Said She Firmly Declined Offer From AI Firm to...
How to Land Your Dream Job in Tech – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Professional Certifications & Continuous Training , Recruitment & Reskilling Strategy , Training & Security Leadership Tips to Get You to the...
Healthcare Identity Security: What to Expect From a Solution – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 What are the key elements of a successful healthcare identity security program? SailPoint healthcare experts Matthew Radcliffe and Rob Sebaugh detail...
Live Webinar Today | Practical Strategies for Accelerating AI Adoption in Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Wade Ellery Field Chief Technology Officer, Radiant Logic Wade Ellery, Field Chief Technology Officer and Senior Technical Evangelist with Radiant Logic....
CISA: NextGen Healthcare Flaw Still Exploited After 7 Months – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Cybercrime , Fraud Management & Cybercrime Attackers Are Targeting the Widely Used Mirth Connect Data Integration...
100 Groups Urge Feds to Put UHG on Hook for Breach Notices – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , HIPAA/HITECH , Security Operations Medical Associations Ask HHS to Clarify HIPAA Duties in Change Healthcare Hack Marianne Kolbasuk...
Google Urges Feds to Ditch Microsoft Over Security Concerns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific Technology Giants Vie for Public Sector Customers Amid Microsoft’s Recent Breaches Chris...
How to Install a VPN on Your Router – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke Most virtual private networks can connect to multiple or unlimited individual devices, like your phones, PCs and tablets. However, using...
Why Your Wi-Fi Router Doubles as an Apple AirTag – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Image: Shutterstock. Apple and the satellite-based broadband service Starlink each recently took steps to address new research into the potential security...