Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Robert K Chin Storefronts via Alamy Stock Photo Nation-state espionage operations are increasingly using native Microsoft services...
Month: May 2024
‘DuneQuixote’ Shows Stealth Cyberattack Methods Are Evolving. Can Defenders Keep Up? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: incamerastock via Alamy Stock Photo If a recent wily cyber-espionage campaign against Middle Eastern government entities is...
Private Internet Search Is Still Finding Its Way – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer Source: Mick House via Alamy Stock Photo A truly private Internet search — where databases can be queried...
UnitedHealth Congressional Testimony Reveals Rampant Security Fails – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: STANCA SANDA via Alamy Stock Photo UnitedHealth’s Change Healthcare subsidiary paid $22 million in...
Intel 471 Acquires Cyborg Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Intel 471, a global provider of cyber threat intelligence (CTI) solutions, today announced that the company acquired Cyborg Security, founded...
Cobalt’s 2024 State of Pentesting Report Reveals Cybersecurity Industry Needs – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, April 30, 2024 /PRNewswire-PRWeb/ — Cobalt, the pioneers of Pentest as a Service (PtaaS) and leading provider of offensive security solutions,...
Shadow APIs: An Overlooked Cyber-Risk for Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Wright Studio via Shutterstock Organizations shoring up their API security need to pay particular attention to unmanaged...
Intel Harnesses Hackathons to Tackle Hardware Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: kawin ounprasertsuk via Alamy Stock Photo Ever since the first Hack@DAC hacking competition in 2017, thousands of...
Key Areas Where Open-Source Security Needs to Evolve – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bill Doerrfeld Cybersecurity experts agree open-source software (OSS) needs to evolve in some key areas, both concerning how organizations govern the OSS...
News alert: LayerX Security raises $24M Series A funding for its ‘enterprise browser’ security platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Tel Aviv, Israel, May 2, 2024, CyberNewsWire — LayerX, pioneer of the LayerX Browser Security platform, today announced $24 million in...
LayerX Security Raises $24M for its Browser Security Platform, Enabling Employees to Work Securely from Any Browser, Anywhere – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Tel Aviv, Israel, May 2nd, 2024, CyberNewsWire Early adoption by Fortune 100 companies worldwide, LayerX already secures more users than any...
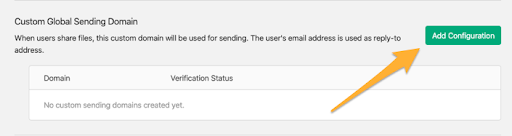
Survalyzer SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Survalyzer configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Vtiger SPF & DKIM Setup: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc Vtiger is a cloud-based CRM that enables businesses to deliver outstanding customer experiences by breaking barriers between their marketing, sales, and...
Spamhero SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Spamhero configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
How to Protect Against Phishing Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leah Hopper Introduction Phishing attacks are an increasingly frequent problem and a grave threat that can cripple businesses and ruin lives. These...
Simply SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Simply configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Showpad SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Showpad configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Rocketseed SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Rocketseed configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Hyperbole, Misinformation, and CyberMonsters Under the Bed – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Ken Westin, Field CISO, Panther Labs This week at the World Economic Forum, there was a panel titled “Are Banks...
Adobe Adds Firefly and Content Credentials to Bug Bounty Program – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Security researchers in Adobe’s bug bounty program can now pick up rewards for finding vulnerabilities in Adobe Firefly and Content...
Are VPNs Legal To Use? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
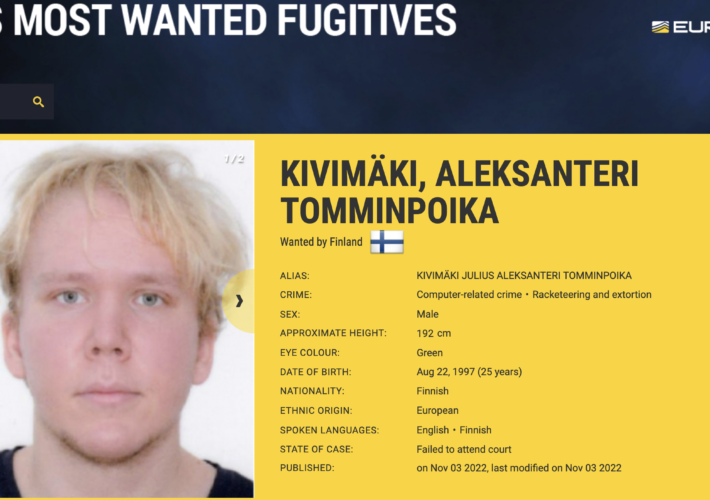
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an...
FCC Fines Major U.S. Wireless Carriers for Selling Customer Location Data – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. Federal Communications Commission (FCC) today levied fines totaling nearly $200 million against the four major carriers — including AT&T,...
Smashing Security podcast #370: The closed loop conundrum, default passwords, and Baby Reindeer – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The UK Government takes aim at IoT devices shipping with weak or default passwords, an identity thief spends two years...
Infosec biz boss accused of BS’ing the world about his career, anti-crime product, customers – Source: go.theregister.com
Source: go.theregister.com – Author: Team Register Jack Blount, the now-ex CEO of Intrusion, has settled with the SEC over allegations he made false and misleading statements...
US charges 16 over ‘depraved’ grandparent scams – Source: go.theregister.com
Source: go.theregister.com – Author: Team Register Sixteen people are facing charges from US prosecutors for allegedly preying on the elderly and scamming them out of millions...
Qantas app glitch sees boarding passes fly to other accounts – Source: go.theregister.com
Source: go.theregister.com – Author: Team Register Aussie airline Qantas says its app is now stable following a data breach that saw boarding passes take off from...
Ring dinged for $5.6M after, among other claims, rogue insider spied on ‘pretty girls’ – Source: go.theregister.com
Source: go.theregister.com – Author: Team Register The FTC today announced it would be sending refunds totaling $5.6 million to Ring customers, paid from the Amazon subsidiary’s...
Two cuffed in Samourai Wallet crypto dirty money sting – Source: go.theregister.com
Source: go.theregister.com – Author: Team Register Two men alleged to be co-founders of cryptocurrency biz Samourai Wallet face serious charges and potentially decades in US prison...
Russia, Iran pose most aggressive threat to 2024 elections, say infoseccers – Source: go.theregister.com
Source: go.theregister.com – Author: Team Register It may come as a surprise to absolutely nobody that experts say, in revealing the most prevalent and likely tactics...