Source: www.cyberdefensemagazine.com – Author: Stevin Evaluate your needs and prioritize solutions that offer open integration and independence from the single-vendor trend, ensuring robust IGA that aligns...
Month: May 2024
Hacking and Cybersecurity – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Trends to Look Out for in 2024 By Yashin Manraj, CEO, Pvotal Technologies For cybersecurity professionals, remaining effective requires staying on...
Stop Managing Identities, Segment them Instead – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Sagie Dulce, VP Research, Zero Networks A Brief History of Identity Management For as long as there have been identities,...
Good Security Is About Iteration, Not Perfection. – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Craig Burland, CISO, Inversion6 In the dynamic and unpredictable realm of cybersecurity, striving for perfect solutions can be a...
GitGuardian Researchers Find Thousands of Leaked Secrets in PyPI (Python Package Index) Packages – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Dwayne McDaniel, GitGuardian Developer and Security Advocate, GitGuardian The modern world of DevOps means relying on our code connecting...
Enhancing Cybersecurity Defenses: The role of Voice Cloning in Penetration Testing – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Alex Serdiuk, CEO, Respeecher Newer and more impactful technological advancements are making the quest for foolproof cybersecurity measures more critical...
Data Breach Search Engines – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Navigating Access and Security in the Stolen Credentials Landscape By Tom Caliendo, Cybersecurity Reporter, Co-Founder at Brocket Consulting LLC In the...
UnitedHealth Group Pays Ransom After Cyberattack: What You Need to Know – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary In an alarming revelation, officials from the Minnesota-based UnitedHealth Group disclosed on Monday that the health insurance and services giant fell...
Cybersecurity Trends and Predictions for 2024 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Nick France, CTO at Cybersecurity Leader Sectigo Given the fact that bad actors are always on the prowl, 2024 is...
AI is Revolutionizing Phishing for Both Sides. What will make the Difference? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Thanks to AI, phishing attacks are better than ever. So is our ability to stop them. By Antonio Sanchez, Principal Cybersecurity...
Venafi Launches 90-Day TLS Certificate Renewal Initiative – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Venafi today launched an initiative to help organizations prepare to implement and manage certificates based on the Transport Layer Security...
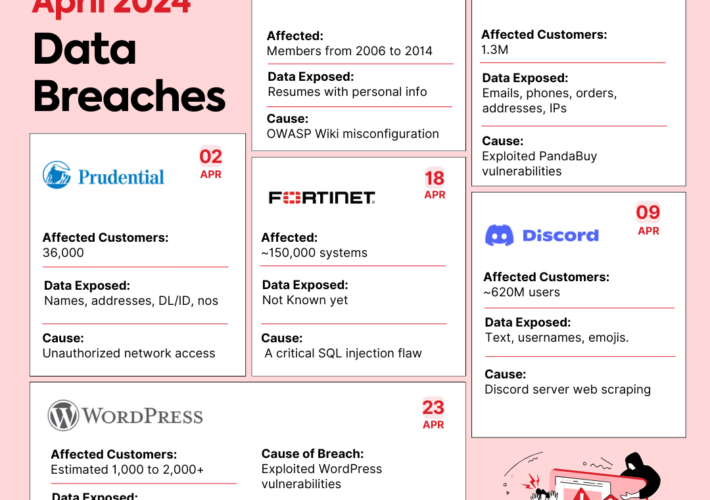
Data Breaches in April 2024 – Infographic – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shubham Jha Data breaches are like uninvited guests at a party – they show up unexpectedly, take what they want, and leave...
Intel 471 Acquires Cyborg Security to Expand Its Cyber Threat Intelligence Portfolio with Innovative Threat Hunting Capabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security The fusion of Cyborg Security with Intel 471 delivers advanced behavioral detections and unprecedented insight into the threat actor landscape....
RSAC 2024 Innovation Sandbox | VulnCheck: A Solution to the Challenge of Vulnerability Prioritization – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has...
Navigating the Future: Insights From the M&A Symposium at Kaseya Connect Global – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaseya The technology industry continually evolves, and managed service providers (MSPs) are often at the forefront of this transformation. We brought MSPs,...
Introducing ISO 42001 and NIST RMF Frameworks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tejas Ranade While AI has created exciting new opportunities for business, it has created urgent questions around ethics, responsible use, development, and...
PIPEDA Compliance with Accutive Data Discovery and Masking: Understanding and protecting your Canadian sensitive data – Source: securityboulevard.com
Source: securityboulevard.com – Author: Accutive Security What is PIPEDA, Canada’s Personal Information Protection and Electronic Documents Act? PIPEDA, or the Personal Information Protection and Electronic Documents...
TrustCloud Product Updates: April 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tejas Ranade You know us: Every month we’re cooking up something new! Here are the updates that hit TrustCloud this month. TrustShare...
News alert: Cybersixgill unveils ‘Third-Party Intelligence’ to deliver vendor-specific threat intel – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido Tel Aviv, Israel – April 30, 2024 – Cybersixgill, the global cyber threat intelligence data provider, broke new ground today by introducing its Third-Party Intelligence module....
April Recap: New AWS Services and Sensitive Permissions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tally Shea Amazon Web Services (AWS) has over 200 cloud services available to help organizations innovate, build business, and secure their data....
AI Voice Scam – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • May 1, 2024 8:28 AM @ Bruce, ALL, In a world that is moving rapidly...
WhatsApp in India – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments numberri • April 30, 2024 7:42 AM I know another case earlier this year is when India threatened...
Island Gets $175M Series D Funding, Doubles Valuation to $3B – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security Investments in Island Led by Coatue and Sequoia Support Global Expansion, R&D, M&A Michael Novinson (MichaelNovinson) • April 30,...
How Personal Branding Can Elevate Your Tech Career – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Training & Security Leadership Your Personal Brand Is as Crucial as Any Skill in Your Tech Toolkit Brandy Harris • April...
DHS: AI-Enhanced Nuclear and Chemical Threats Are Risk to US – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development New Report Says Global Threat Actors May Use AI to...
Defining a Detection & Response Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Verizon Breach Report: Vulnerability Hacks Tripled in 2023 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Video , Vulnerability Assessment & Penetration Testing (VA/PT) Data Breach Report Lead Author Alex Pinto Discusses...
Patched Deserialization Flaw in Siemens Product Allows RCE – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security The Siemens Simatic Energy Manager Used an Unsafe BinaryFormatter Method Prajeet Nair (@prajeetspeaks) • April 30, 2024 ...