Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: kawin ounprasertsuk via Alamy Stock Photo Ever since the first Hack@DAC hacking competition in 2017, thousands of...
Month: May 2024
Key Areas Where Open-Source Security Needs to Evolve – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bill Doerrfeld Cybersecurity experts agree open-source software (OSS) needs to evolve in some key areas, both concerning how organizations govern the OSS...
News alert: LayerX Security raises $24M Series A funding for its ‘enterprise browser’ security platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Tel Aviv, Israel, May 2, 2024, CyberNewsWire — LayerX, pioneer of the LayerX Browser Security platform, today announced $24 million in...
LayerX Security Raises $24M for its Browser Security Platform, Enabling Employees to Work Securely from Any Browser, Anywhere – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Tel Aviv, Israel, May 2nd, 2024, CyberNewsWire Early adoption by Fortune 100 companies worldwide, LayerX already secures more users than any...
Survalyzer SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Survalyzer configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Vtiger SPF & DKIM Setup: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc Vtiger is a cloud-based CRM that enables businesses to deliver outstanding customer experiences by breaking barriers between their marketing, sales, and...
Spamhero SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Spamhero configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
How to Protect Against Phishing Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leah Hopper Introduction Phishing attacks are an increasingly frequent problem and a grave threat that can cripple businesses and ruin lives. These...
Simply SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Simply configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Showpad SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Showpad configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Rocketseed SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Rocketseed configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Hyperbole, Misinformation, and CyberMonsters Under the Bed – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Ken Westin, Field CISO, Panther Labs This week at the World Economic Forum, there was a panel titled “Are Banks...
Adobe Adds Firefly and Content Credentials to Bug Bounty Program – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Security researchers in Adobe’s bug bounty program can now pick up rewards for finding vulnerabilities in Adobe Firefly and Content...
Are VPNs Legal To Use? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
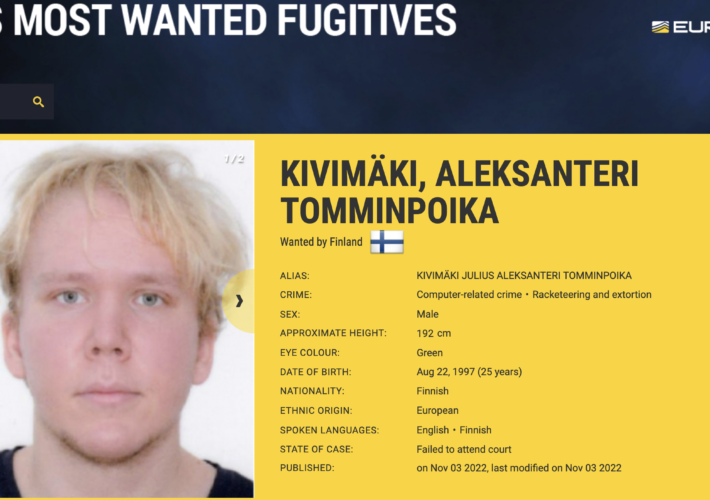
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an...
FCC Fines Major U.S. Wireless Carriers for Selling Customer Location Data – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. Federal Communications Commission (FCC) today levied fines totaling nearly $200 million against the four major carriers — including AT&T,...
Smashing Security podcast #370: The closed loop conundrum, default passwords, and Baby Reindeer – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The UK Government takes aim at IoT devices shipping with weak or default passwords, an identity thief spends two years...
Qantas Customers’ Boarding Passes Exposed in Flight App Mishap – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Stonemeadow Photography via Alamy Stock Photo Qantas, the flagship Australian airline, is investigating a privacy...
‘Cuttlefish’ Zero-Click Malware Steals Private Cloud Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: David Fleetham via Alamy Stock Photo A never-before-seen malware strain is targeting enterprise-grade and SOHO routers to...
The Cybersecurity Checklist That Could Save Your M&A Deal – Source: www.darkreading.com
Source: www.darkreading.com – Author: Craig Davies 4 Min Read Source: Cagkan Sayin via Alamy Stock Photo COMMENTARY Mergers and acquisitions (M&A) activity is making a much-anticipated...
Verizon DBIR: Basic Security Gaffes Underpin Bumper Crop of Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Security bugs are having a cybercrime moment: For 2023, 14% of all data breaches started...
Facebook at 20: Contemplating the Cost of Privacy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild, Contributing Writer SourceL Skorzewiak via Alamy Stock Photo In the 20 years since then-Harvard University student Mark Zuckerberg launched Facebook,...
MITRE’s Cyber Resiliency Engineering Framework Aligns With DoD Cyber Maturity Model Cert – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE McLean, Va. & Bedford, Mass., April 25, 2024 — MITRE’s Cyber Resiliency Engineering Framework (CREF) NavigatorTM now incorporates the US...
Philippines Pummeled by Assortment of Cyberattacks & Misinformation Tied to China – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: robertharding via Alamy Stock Photo A recent massive spike in cyber misinformation and hacking campaigns against the...
Jason Haddix Joins Flare As Field CISO – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Montreal, Quebec, Canada – April 25, 2024 – Flare, a global leader in Threat Exposure Management, is pleased to announce that renowned...
Intel Harnesses Hackathons to Tackle Hardware Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: kawin ounprasertsuk via Alamy Stock Photo Ever since the first Hack@DAC hacking competition in 2017, thousands of...
LockBit, Black Basta, Play Dominate Ransomware in Q1 2024 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 LockBit, Black Basta and Play have been observed to be the most active ransomware groups in Q1 2024, with Black Basta...
UnitedHealth CEO Confirms Breach Tied to Stolen Credentials, No MFA – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The ransomware attack that hit US health tech titan Change Healthcare earlier this year was orchestrated by hackers who leveraged stolen...
1 in 5 US Ransomware Attacks Triggers Lawsuit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Nearly one in five (18%) ransomware incidents in the US led to a lawsuit in 2023, with 123 filed so far,...
Lawsuits and Company Devaluations Await For Breached Firms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new report has laid bare the significant financial and reputational costs stemming from serious cyber-attacks, including what are often unplanned...