Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Bakhtiar Zein via Alamy Stock Vector A rise in prompt injection engineering into large language models (LLMs)...
Month: May 2024
AttackIQ Partners With Cyber Poverty Line Institute to Provide Academy Courses to Underserved Communities – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SANTA CLARA, Calif. – May 6, 2024 – AttackIQ®, the leading independent vendor of breach and attack simulation (BAS) solutions and founding...
BigID Launches Industry-First Hybrid Scanning for Cloud Native Workloads – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, May 6, 2024 /PRNewswire/ — BigID, the pioneer in AI-augmented data security, compliance, and privacy for modern cloud-first enterprises, today announced...
Introducing the NetBeacon Institute: Empowering a Safer Web – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE RESTON, Va., May 6, 2024 /PRNewswire/ — The DNS Abuse Institute, dedicated to combating online technical abuse and fostering a safer digital environment,...
AXA XL Introduces Endorsement to Help Public Companies Address SEC Cyber Reporting Costs – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK, May 6, 2024 /PRNewswire/ — AXA XL unveiled a new cyber insurance endorsement providing public companies with dedicated coverage to...
Microsoft Previews Feature to Block Malicious OAuth Apps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Richard Levine via Alamy Stock Photo Threat actors are increasingly including malicious OAuth apps in their campaigns...
AT&T Splits Cybersecurity Services Business, Launches LevelBlue – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Mikko Lemola via Shutterstock AT&T has completed the divestiture of its cybersecurity services group and formed a...
The Psychological Underpinnings of Modern Hacking Techniques – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Lemieux 4 Min Read Source: Brain light via Alamy Stock Photo COMMENTARY The landscape of cybersecurity is not just a battleground...
RSAC: Securing Foundational Tech Critical to Upholding Democratic Values, Says Blinken – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by US Secretary of State Antony Blinken explained the US government’s vision to secure foundational technologies for the benefit of...
RSAC: Threat Actors Weaponize Hacktivism for Financial Gain – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Hacktivism has become increasingly blurred with financial cybercrime and nation-state activities, with threat actors deliberately aligning with causes to facilitate their...
RSAC: Law Enforcement Takedowns Force Ransomware Affiliates to Diversify – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The recent wave of law enforcement operations against ransomware gangs led to short-term decreased ransomware payments and activities, forcing ransomware affiliates...
RSAC: 70% of Businesses Prioritize Innovation Over Security in Generative AI Projects – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Businesses are being left vulnerable to a range of cybersecurity and privacy risks as 70% of business executives prioritize innovation over...
What Palo Alto Networks and CrowdStrike Teach us About Using a Mobile Defense Platform – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Tom Tovar, Co-creator and CEO of Appdome There’s a major battle brewing between platform vs. platformization companies in cybersecurity....
Organizational Cybersecurity Hinges on End-User Satisfaction – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The critical role end-user experience plays in organizational security By Amitabh Sinha, CEO and Co-Founder of Workspot In an era...
Why Your VPN May Not Be As Secure As It Claims – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Virtual private networking (VPN) companies market their services as a way to prevent anyone from snooping on your Internet usage. But...
Identity, Credential Misconfigurations Open Worrying Security Gaps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Identity and credential misconfigurations pose a major security risk to organizations, with companies in energy, manufacturing and financial services particularly...
Tracking CVE-2024-2876: Why does the latest WordPress exploit compromise over 90,000 websites? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nikhil Menon A highly concerning security loophole was recently discovered in a WordPress plugin called “Email Subscribers by Icegram Express,” a popular...
Got Your Eyes on Cyber Essentials Plus? We’ve Got You Covered! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mor Avni, Product Manager, Scytale With data breaches and hacking attacks in the headlines way too often, strengthening digital defenses has become...
Understanding GitGuardian’s Self-Hosted Solution – Source: securityboulevard.com
Source: securityboulevard.com – Author: Greg Bulmash At GitGuardian, as cybersecurity experts, we understand there are a variety of reasons our customers might not want a cloud-based...
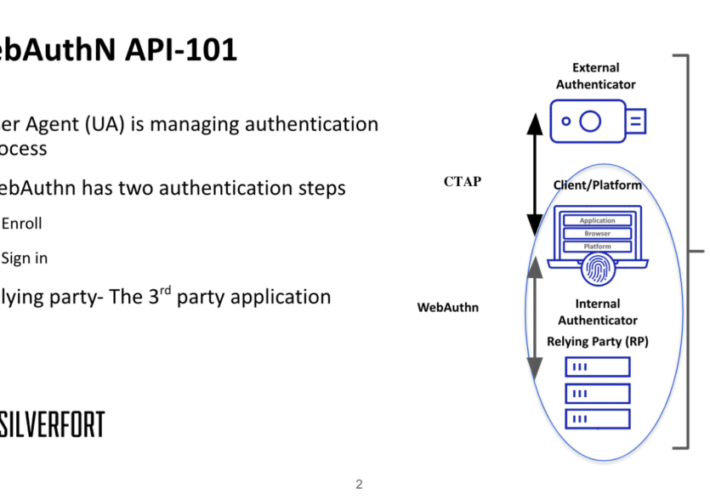
Using MITM to bypass FIDO2 phishing-resistant protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dor Segal FIDO2 is a modern authentication group term for passwordless authentication. The Fast Identity Online (FIDO) Alliance developed it to replace the...
USENIX Security ’23 – A Bug’s Life: Analyzing the Lifecycle and Mitigation Process of Content Security Policy Bugs – Distinguished Paper Award Winner – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » USENIX Security ’23 – A Bug’s Life: Analyzing the Lifecycle and Mitigation Process of...
Financial cyberthreats in 2023 – Source: securelist.com
Source: securelist.com – Author: Kaspersky Money is what always attracts cybercriminals. A significant share of scam, phishing and malware attacks is about money. With trillions of...
Amnesty International Cites Indonesia as a Spyware Hub – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Rawf8 via Alamy Stock Photo New research from Amnesty International’s Security Lab identifies Indonesia as...
Celebrating our 12th Anniversary at RSA conference 2024 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary It’s been an amazing journey and we are so thankful to the team at the RSA Conference for working with us...
Offensive Awakening: The 2024 Shift from Defensive to Proactive Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Adversarial Cyber Exercises Are The New Mandate By Stephen Gates, Principal SME, Horizon3.ai After observing the cyber threat landscape in...
Navigating the Digital Age: AI’s Crucial Role in Cybersecurity Reinforcement – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Harnessing the Power of AI for Advanced Cyber Threat Intelligence and Prevention By Bryan Kissinger, Senior Vice President of Security...
GenAI Continues to Dominate CIO and CISO Conversations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity The NASCIO Midyear Conference this past week highlighted the good, the bad and the scary of generative AI, as...
RSAC 2024 Innovation Sandbox | Reality Defender: Deepfake Detection Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has...
USENIX Security ’23 – Silent Bugs Matter: A Study of Compiler-Introduced Security Bugs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Jianhao Xu, Kangjie Lu, Zhengjie Du, Zhu Ding, Linke Li Qiushi Wu, Mathias Payer, Bing Mao Many thanks to...
RSAC 2024 Innovation Sandbox | Dropzone AI: Automated Investigation and Security Operations – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has...