Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – SMACK: Semantically Meaningful Adversarial Audio Attack by...
Month: May 2024
Massive Online Shopping Scam Racks Up 850,000 Victims – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A group of bad actors — likely from China — is running a global cybercrime-as-a-service operation. It oversees a massive...
NSA: State-backed attackers are not after your data — they’re targeting CI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Roberts Companies in the crosshairs of advanced persistent threat (APT) actors look at data theft not as a primary objective of...
How Criminals Are Using Generative AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier There’s a new report on how criminals are using generative AI tools: Key Takeaways: Adoption rates of AI technologies among...
Beware of cyber scams: How hackers tried to scam me – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Lari Luoma has over 20 years of experience working in the fields of security and networking. For the last 13 years,...
Cloud Computing is Evolving – With a Little Help From AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , RSA Conference Sarbjeet Johal of StackPayne on How Generative AI is Improving Cloud...
ISMG Editors: Day 3 Highlights at RSA Conference 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Panel Discusses Way to Address the Job Shortage,...
Live Webinar | Digital Doppelgängers: The Dual Faces of Deepfake Technology – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Account Takeover Fraud , AI-Based Attacks , Artificial Intelligence & Machine Learning Presented by KnowBe4 60 mins ...
Live Webinar | The State of Cloud Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Dennen Monks Field Tech Strategist, CrowdStrike Dennen is passionate about helping companies achieve elegant operationalized states across people, process, and technology....
Cryptohack Roundup: BTC-e’s Alex Vinnik Pleads Guilty – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Arrests in a $43M Ponzi Scheme and Arrest in...
Tech Giants Cater to Government With AI Tools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Government , Industry Specific Mitre, Microsoft Announce Government-Focused AI Tools This Week Rashmi Ramesh (rashmiramesh_)...
Data Classification Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: In many ways, data has become the primary currency of modern organizations. It doesn’t matter whether you are a large business enterprise,...
CISA Courts Private Sector to Get Behind CIRCIA Reporting Rules – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: GK Images via Alamy Stock Photos RSA CONFERENCE 2024 – San Francisco – The Cybersecurity...
‘The Mask’ Espionage Group Resurfaces After 10-Year Hiatus – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: rawf8 via Shutterstock An advanced persistent threat (APT) group that has been missing in action for more...
2 (or 5) Bugs in F5 Asset Manager Allow Full Takeover, Hidden Accounts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: SOPA Images Limited via Alamy Stock Photo Newly discovered vulnerabilities in F5 Networks’ BIG-IP Next Central Manager...
87% of DDoS Attacks Targeted Windows OS Devices in 2023 – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Singapore, 8th May, 2024 – New data from Nexusguard’s DDoS Statistical Trends Report 2024 reveals bad actors are shifting DDoS tactics. Computers and servers...
CyberProof Announces Strategic Partnership With Google Cloud – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE ALISO VIEJO, Calif. and BENGALURU, India, May 6, 2024 /PRNewswire/ — CyberProof, a UST company, has announced an extended partnership with Google Cloud focused on leveraging Google Chronicle Security...
LockBit Claims Wichita as Its Victim 2 Days After Ransomware Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: vchal via Alamy Stock Photo LockBit ransomware group says it is responsible for a ransomware...
Vast Network of Fake Web Shops Defrauds 850,000 & Counting – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Nako Photography via Alamy Stock Photo A vast criminal network has stolen the payment credentials of more...
How Government Agencies Can Leverage Grants to Shore Up Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeff Strane, Linda Heiss Source: Igor Stevanovic via Alamy Stock Photo COMMENTARY Since the pandemic forced unprecedented adoption of remote access and...
Tech Companies Promise ‘Secure by Design’ Products – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading Source: Digital Pegasus via Shutterstock RSA CONFERENCE 2023 – San Francisco – More than...
Cancer patients’ sensitive information accessed by “unidentified parties” after being left exposed by screening lab for years – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A medical lab that specialises in cancer screenings has admitted to an alarming data breach that left sensitive patient information...
Smashing Security podcast #371: Unmasking LockBitsupp, company extortion, and a Tinder fraudster – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The kingpin of the LockBit ransomware is named and sanctioned, a cybersecurity consultant is charged with a $1.5 million extortion,...
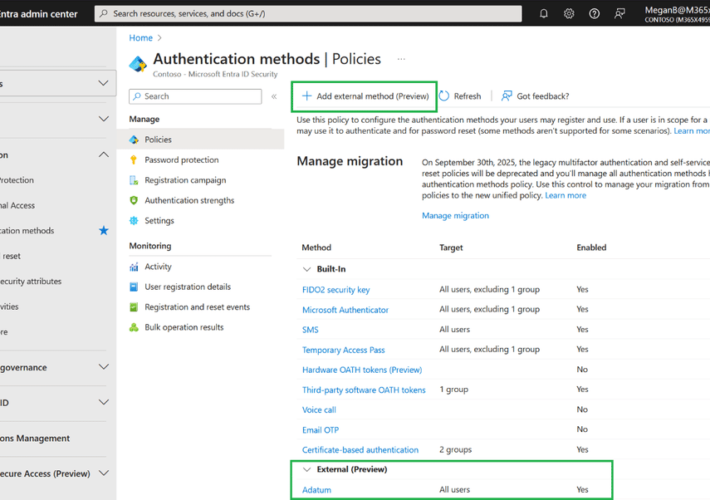
Silverfort Announces New Integration with Microsoft Entra ID EAM – Source: securityboulevard.com
Source: securityboulevard.com – Author: Zev Brodsky Silverfort is excited to announce our integration with external authentication methods (EAM) in Microsoft Entra ID, which is now in...
Crypto Mixer Money Laundering: Samourai Founders Arrested – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja The recent crackdown on the crypto mixer money laundering, Samourai, has unveiled a sophisticated operation allegedly involved in facilitating illegal...
AI Regulation in Finance: Steering the Future with Consumer Protection at the Helm – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rebecca Kappel The financial industry is experiencing a gold rush of sorts with the integration of Artificial Intelligence (AI) technologies. With huge...
How Nudge Security is useful in a merger or acquisition – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nudge Security Blog For anyone who has been through a corporate merger or acquisition, you know that things can get…messy. Just like...
Build Strong Information Security Policy: Template & Examples – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Kelly Every organization needs to have security measures and policies in place to safeguard its data. One of the best and...
Ransomware Attacks are Up, but Profits are Down: Chainalysis – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt In the ever-evolving world of ransomware, it’s getting easier for threat groups to launch attacks – as evidence by the...
USENIX Security ’23 – “Security Is Not My Field, I’m A Stats Guy”: A Qualitative Root Cause Analysis of Barriers to Adversarial Machine Learning Defenses in Industry – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Jaron Mink, Harjot Kaur, Juliane Schmüser, Sascha Fahl, Yasemin Acar Many thanks to USENIX for publishing their outstanding USENIX...