Source: www.schneier.com – Author: B. Schneier Back in the 1960s, if you played a 2,600Hz tone into an AT&T pay phone, you could make calls without...
Month: May 2024
How Did Authorities Identify the Alleged Lockbit Boss? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Last week, the United States joined the U.K. and Australia in sanctioning and charging a Russian man named Dmitry Yuryevich Khoroshev...
Criminal IP and Quad9 Collaborate to Exchange Domain and IP Threat Intelligence – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Torrance, California, May 13th, 2024, CyberNewsWire Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has...
CISOs Reconsider Their Roles in Response to GenAI Integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Chief information security officers (CISOs) face mounting pressure as cyberattacks surge and complexities surrounding the implementation of GenAI and AI...
Votiro Named Market Leader in Data Security by the 2024 CDM Awards – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro It’s been less than three months since the launch of our unified content and data security platform and we’re already being...
Veriti Extends Exposure Assessment & Remediation to the Cloud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Veriti As enterprises continue to shift towards cloud-based infrastructures, the complexity of managing and securing these environments grows. Recognizing this, Veriti is...
Authorised Economic Operator: Cyber Security Requirements – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leah Hopper Introduction Authorised Economic Operator (AEO) is a status that a lot of UK companies want to obtain for the sake...
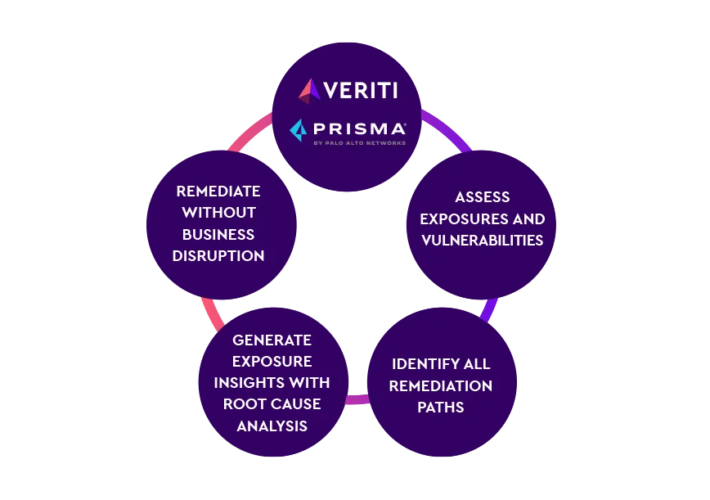
PRISMA CLOUD – Source: securityboulevard.com
Source: securityboulevard.com – Author: Veriti Veriti proactively monitors and safely remediates risk across the security infrastructure to elevate CNAPP by remediating compensating controls, without disrupting the...
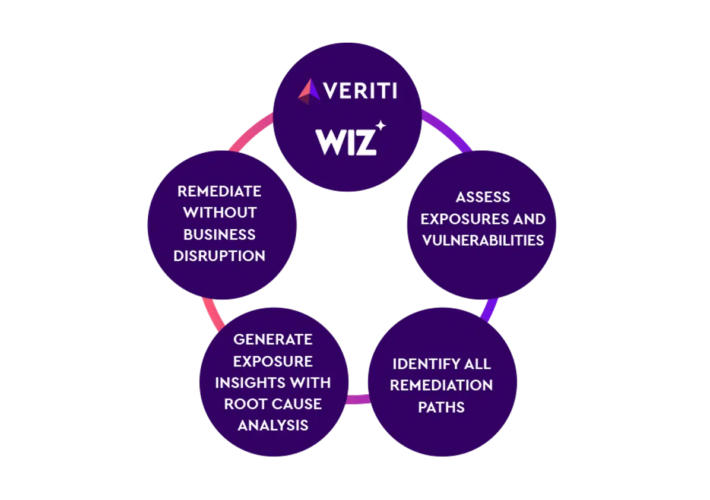
Wiz – Source: securityboulevard.com
Source: securityboulevard.com – Author: Veriti Veriti proactively monitors and safely remediates risk across the security infrastructure to elevate CNAPP by remediating compensating controls, without disrupting the...
CISA and FBI Issue Alert on Path Traversal Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina The joint alert from CISA and FBI highlights the continued exploitation of path traversal vulnerabilities in critical infrastructure attacks, impacting...
Hardware Level Vulnerabilities, Revisited – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joao Correia In August of last year, I examined several CPU bugs that posed serious security threats. The mitigations for these vulnerabilities...
HPE Aruba Vulnerabilities: Prevent Systems From RCE Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja Recently, HPE Aruba Networking, formerly known as Aruba Networks, has encountered significant security challenges. Vulnerabilities in their ArubaOS, the proprietary...
MY TAKE: RSAC 2024’s big takeaway: rules-based security is out; contextual security is taking over – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido KINGSTON, Wash. — U.S. Secretary of State Antony Blinken opened RSA Conference 2024 last week issuing a clarion call for the...
The Importance of Data Categorization In A Threat-Filled Landscape – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Dr. Pragyansmita Nayak, Chief Data Scientist, Hitachi Vantara Federal National security is amid a transformative journey driven by technological...
USENIX Security ’23 – Don’t be Dense: Efficient Keyword PIR for Sparse Databases – Distinguished Paper Award Winner – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Don’t be Dense: Efficient Keyword PIR for...
15 Best Network Pentesting Tools [Free + Paid] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh This guide provides an overview of the top 15 network penetration testing tools. Aimed at IT and security professionals, it...
What is Internal Penetration Testing: Methods, Tools, & Checklist – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh Internal penetration testing is a proactive approach that identifies vulnerabilities from within your network, allowing you to prioritize weaknesses and...
Spike in Layoffs Pose Serious Cybersecurity Concerns – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Different Types of Risk Exposure and Best Practices for Protecting Your Data By Adam Gavish, CEO & Cofounder, DoControl There...
Millions of IoT Devices at Risk from Flaws in Integrated Cellular Modem – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: jamesteohart via Shutterstock Millions of IoT devices in sectors such as financial services, telecommunications, healthcare, and automotive...
CISOs Are Worried About Their Jobs & Dissatisfied With Their Incomes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Lev Dolgachov via Alamy Stock Photo Roughly a third of CISOs are dissatisfied with their...
Critical Bug Could Open 50K+ Tinyproxy Servers to DoS, RCE – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Anthony Spratt via Alamy Stock Photo Around 50,000 instances of an open source proxy server used for...
Friday Squid Blogging: Squid Mating Strategies – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Squid Mating Strategies Some squids are “consorts,” others are “sneakers.” The species is healthiest when individuals...
New Attack Against Self-Driving Car AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier This is another attack that convinces the AI to ignore road signs: Due to the way CMOS cameras operate, rapidly...
How to Get PCI Compliance Certification? Steps to Obtain it – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra Do you recall the incidents involving Equifax, Target, and British Airways? Experiencing a data breach can significantly harm your business...
What is Wireless Network Penetration Testing? [Explained] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh Are your wireless networks truly safe from cyber threats? Wireless network penetration testing is critical to answer that question with...
Cloud Monitor Scans For Risky Video Files in Google Drive/OneDrive – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexa Sander Recently, we hosted Michael Tapia, Chief Technology Director at Clint ISD in Texas, and Kobe Brummet, Cybersecurity Technician at Hawkins...
Dell Hell: 49 Million Customers’ Information Leaked – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Dark web sale of leaked data exposes Dell users to phishing phraud. Dell customer data from the past six or...
Emerald Divide Uses GenAI to Exploit Social, Political Divisions in Israel Using Disinformation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy An advanced persistent threat (APT) group backed by Iran has been stoking divisions within Israeli society for the past three...
Healthcare Software Company Gains Comprehensive Visibility with LogRhythm Axon – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast A healthcare identity access provider was looking for a security information and event management (SIEM) platform that could maximize visibility...
USENIX Security ’23 – Authenticated Private Information Retrieval – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Simone Colombo, Kirill Nikitin, Henry Corrigan-Gibbs, David J. Wu, Bryan Ford Many thanks to USENIX for publishing their outstanding...














![15-best-network-pentesting-tools-[free-+-paid]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2024/05/132031/15-best-network-pentesting-tools-free-paid-source-securityboulevard-com-710x500.jpg)








![what-is-wireless-network-penetration-testing?-[explained]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2024/05/131983/what-is-wireless-network-penetration-testing-explained-source-securityboulevard-com.png)




