Source: www.theguardian.com – Author: Jack Snape A fear of illicit drug test results and psychologist session notes being leaked onto the dark web is helping drive...
Month: May 2024
DNS Tunneling Abuse Expands to Tracking & Scanning Victims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Aleksey Funtap via Alamy Stock Photo Attackers are taking malicious manipulation of DNS traffic to the next...
There Is No Cyber Labor Shortage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rex Booth Rex Booth, Chief Information Security Officer, SailPoint May 14, 2024 5 Min Read Source: Bryan Sikora via Alamy Stock Photo...
Heartbleed: When Is It Good to Name a Vulnerability? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andrada Fiscutean Back in April 2014, researchers uncovered a serious vulnerability in OpenSSL. There are many serious vulnerabilities, but this one was...
AI is changing the shape of leadership – how can business leaders prepare? – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Ana Paula Assis, Chairman, Europe, Middle East and Africa, IBM. EXECUTIVE SUMMARY: From the shop floor to the boardroom, artificial...
New alert: Logicalis enhances global security services with the launch of Intelligent Security – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire London, United Kingdom, May 13, 2024, CyberNewsWire — Logicalis, the global technology service provider delivering next-generation digital managed services, has today...
News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Torrance, Calif., May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA,...
ReversingLabs Search Extension for Splunk Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: ReversingLabs ReversingLabs has released a new application for Splunk users to enhance their data using ReversingLabs APIs. This application is titled “ReversingLabs...
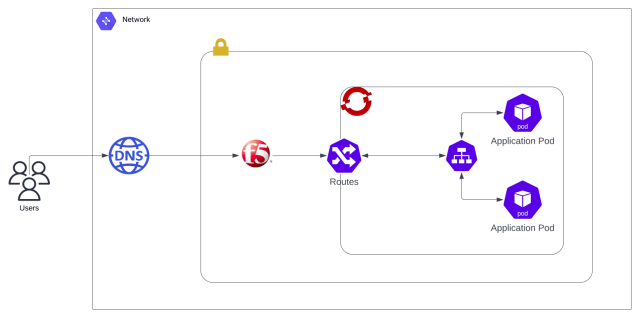
Simplify Certificate Lifecycle Management And Build Security Into OpenShift Kubernetes Engine With AppViewX KUBE+ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Karthik Kannan Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications. Building on top...
What you missed at RSA Conference 2024: Key trends and takeaways – Source: securityboulevard.com
Source: securityboulevard.com – Author: Carolynn van Arsdale The 32nd annual RSA Conference (RSAC) – one of the biggest cybersecurity shows in North America — was held...
Sectrio and DigiGlass inaugurate State-of-the-Art OT/ICS SOC with Device Testing Lab in the UAE – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sectrio Sectrio and DigiGlass by Redington’s leadership at the new OT/ICS and IoT SOC in Dubai, UAE Dubai, United Arab Emirates, May...
What are Machine Credentials, And Why Are They Important to Secure in Your Organization? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Guetta WHAT are Machine Credentials? Machine Credentials are a collective noun for Non-human Identities that operate as digital access keys used...
What are Service Accounts, and why are they Important to Secure? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Guetta What are Service Accounts? Service Accounts are Non-Human Identity accounts used by machines or apps to communicate with one another...
Several Vulnerabilities Addressed in Ubuntu 24.04 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina Ubuntu 24.04 LTS was released on April 25, 2024, with some new exciting features. Like every other release, it is...
What are OAuth Tokens, and why are they important to Secure? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Guetta What are OAuth Tokens? OAuth (Open Authorization) Tokens are Non-Human Identities that work as a secure authentication mechanism. They delegate...
Protect your Hardware Security Module | Blog | Code Intelligence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalia Kazankova As vehicles become increasingly reliant on software, secure and functional Hardware Security Modules (HSMs) are paramount. Unknown vulnerabilities in your...
Dropbox Sign Breach: Threat Actors Access User Information – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja In a recent disclosure, cloud storage giant Dropbox revealed a breach affecting its digital signature service, Dropbox Sign (formerly HelloSign)....
Incident response analyst report 2023 – Source: securelist.com
Source: securelist.com – Author: Kaspersky GERT, Kaspersky Security Services SOC, TI and IR posts SOC, TI and IR posts 14 May 2024 minute read Incident response...
FCC Names and Shames First Robocall Threat Actor – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US telecoms regulator has named a malicious robocall group for the first time, in a bid to help international partners...
How ‘Radical Transparency’ Can Bolster Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Events , RSA Conference , RSA Conference Videos Ex-DHS Official Suzanne Spaulding and Jim Richberg of Fortinet on Critical Concepts Mathew...
Experts Warn the NVD Backlog Is Reaching a Breaking Point – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific Federal Database Nears 10,000 Unanalyzed Vulnerabilities Amid Halt in Operations Chris Riotta...
Defenders’ Dilemma: Can AI Bolster Cyber Resilience? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Visa’s Subra Kumaraswamy on Threat Detection, AI and...
Feds, Groups Warn Health Sector of Black Basta Threats – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Advisories Come As Black Basta Appears Responsible for Ascension Ransomware Attack Marianne...
Report: Organisations Have Endpoint Security Tools But Are Still Falling Short on the Basics – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Most IT and security teams would agree that ensuring endpoint security and network access security applications are running in compliance...
Prison for cybersecurity expert selling private videos from inside 400,000 homes – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A Korean cybersecurity expert has been sentenced to prison for illegally accessing and distributing private videos from vulnerable “wallpad” cameras...
The Next Generation of Endpoint Security Is Being Reimagined Today – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Vivek Ramachandran, CEO & Founder, SquareX Gone are the days when traditional antivirus solutions were the bulwark of endpoint...
500 Victims In, Black Basta Reinvents With Novel Vishing Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: ciaobucarest via Alamy Stock Photo A new Black Basta campaign is annoying victims into submission with onslaughts...
Ukrainian, Latvian TV Hijacked to Broadcast Russian Celebrations – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Trambler58 via Shutterstock A Ukrainian agency in charge of television and radio broadcasting reported that...
IntelBroker Nabs Europol Info; Agency Investigating – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Deco via Alamy Stock Photo A well-known hacking outfit called “IntelBroker” has put up...
Why Tokens Are Like Gold for Opportunistic Threat Actors – Source: www.darkreading.com
Source: www.darkreading.com – Author: John A. Smith John A. Smith, Founder & Chief Security Officer, Conversant Group May 13, 2024 4 Min Read Source: Leigh Prather...