Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Louisa Svensson via Alamy Stock Photo The Securities and Exchange Commission (SEC) announced it will...
Month: May 2024
400K Linux Servers Recruited by Resurrected Ebury Botnet – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: Skorzewiak via Alamy Stock Photo A Linux-based botnet is alive and well, powering cryptocurrency theft and financial...
CISOs and Their Companies Struggle to Comply With SEC Disclosure Rules – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Dany Kurniawan via Shutterstock About six months ago, CISO Steve Cobb noticed that the contract language proposed...
Whose Data Is It Anyway? Equitable Access in Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Barrett Lyon 4 Min Read Source: marcos alvarado via Alamy Stock Photo COMMENTARY In an era of enormous data volumes and proliferated...
Microsoft Has Yet to Patch 7 Pwn2Own Zero-Days – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer 2 Min Read Source: MAXSHOT.PL via Shutterstock Seven different Windows privilege escalation vulnerabilities have not yet been addressed...
Google's AI Watermarks Will Identify Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer 2 Min Read Google made a number of AI-related announcements at the Google I/O developer conference this week,...
Friday Squid Blogging: Emotional Support Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier When asked what makes this an “emotional support squid” and not just another stuffed animal, its creator says: They’re emotional...
FBI Seizes BreachForums Website – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The FBI has seized the BreachForums website, used by ransomware criminals to leak stolen corporate data. If law enforcement has...
ISMG Editors: Why Synthetic ID Fraud Is on the Rise – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Fraud Risk Management , Ransomware Also: More Support for Ransomware Victims, Key Takeaways From RSA 2024...
Healthcare Identity Security: What to Expect from Your Solution – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 What are the key elements of a successful healthcare identity security program? SailPoint healthcare experts Matthew Radcliffe and Rob Sebaugh detail...
US SEC Approves Wall Street Data Breach Reporting Regs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Industry Specific , Standards, Regulations & Compliance Covered Financial Institutions Have 30 Days to Notify Customers of...
Hackers Target US AI Experts With Customized RAT – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Hackers Sought Specific Generative AI...
Health Plan Services Firm Notifying 2.4 Million of PHI Theft – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime Data Stolen Over a Year Ago, But WebTPA Didn’t Discover Hack Until...
Nissan reveals ransomware attack exposed 53,000 workers’ social security numbers – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Nissan North America has revealed that extortionists who demanded a ransom after breaking into its external VPN and disrupted systems...
US AI Experts Targeted in SugarGh0st RAT Campaign – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Source: Thongden Studio via Shutterstock A likely Chinese threat actor is using a recent variant of the notorious Gh0st RAT malware...
A Human-Centric Security Approach, Supported by AI – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Protect People and Infrastructure Simultaneously: Proofpoint CEO Sumit...
Here’s What 20 Top Cybersecurity CEOs And CTOs Were Saying At RSA Conference 2024 – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 CRN spoke with the CEOs and CTOs of a number of cybersecurity companies, including Proofpoint, Palo Alto Networks, Rubrik and CrowdStrike,...
How AI turbocharges your threat hunting game – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Over 90 percent of organizations consider threat hunting a challenge. More specifically, seventy-one percent say that both prioritizing alerts...
SugarGh0st RAT variant, targeted AI attacks – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Cyber security experts have recently uncovered a sophisticated cyber attack campaign targeting U.S-based organizations that are involved in artificial...
Black Basta Ransomware Struck More Than 500 Organizations Worldwide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet A joint cybersecurity advisory from the Federal Bureau of Investigation, Cybersecurity and Infrastructure Security Agency, Department of Health and Human...
Get on Cybersecurity Certification Track With $145 Off These Courses – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published May 17, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Restore Damaged Files & Save Your Business for Only $50 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published May 17, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Lookback Analysis in ERP Audit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly Today, data is the key driver of success, and even small decisions can have a significant impact. Therefore, it is...
Ransomware Attacks Evolve as Average Ransom Demand Tops $1.26 Million – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Ransomware claims surged by 64% year-over-year, particularly among mid-market and emerging businesses. There was a sharp rise in “indirect” ransomware...
How to achieve ITGC automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly Step 3. Testing and Validation With the enhanced controls and continuous monitoring, the organization shifted its focus to testing and...
How to Get a VAPT Certificate? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover In today’s digital age, cybersecurity is more important than ever. Businesses that maintain the data of their clients are continually...
How to do Penetration Testing effectively – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh Do you want to enhance your organisation’s cybersecurity by identifying and addressing vulnerabilities before they can be exploited? Mastering the...
Hackers Use Fake DocuSign Templates to Scam Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A surge in phishing attacks that use emails appearing to be from DocuSign is being fueled by a Russian dark...
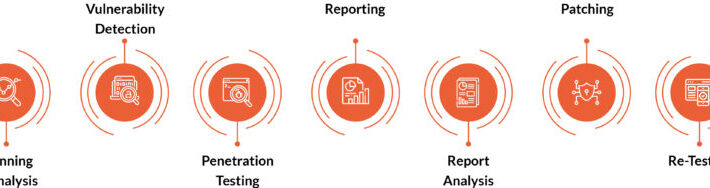
What is Web Application Penetration Testing? [+ Checklist] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh Secure code ensures the Internet runs smoothly, safely, and securely. This includes examples from our banks to online stores, all...
USENIX Security ’23 – Reusable Enclaves For Confidential Serverless Computing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Shixuan Zhao, Pinshen Xu, Guoxing Chen, Mengya Zhang, TYinqian Zhang, Zhiqiang Lin Many thanks to USENIX for publishing their outstanding...

























![what-is-web-application-penetration-testing?-[+-checklist]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2024/05/132602/what-is-web-application-penetration-testing-checklist-source-securityboulevard-com.png)
