Source: www.proofpoint.com – Author: 1 Source: Thongden Studio via Shutterstock A likely Chinese threat actor is using a recent variant of the notorious Gh0st RAT malware...
Day: May 17, 2024
A Human-Centric Security Approach, Supported by AI – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Protect People and Infrastructure Simultaneously: Proofpoint CEO Sumit...
Here’s What 20 Top Cybersecurity CEOs And CTOs Were Saying At RSA Conference 2024 – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 CRN spoke with the CEOs and CTOs of a number of cybersecurity companies, including Proofpoint, Palo Alto Networks, Rubrik and CrowdStrike,...
How AI turbocharges your threat hunting game – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Over 90 percent of organizations consider threat hunting a challenge. More specifically, seventy-one percent say that both prioritizing alerts...
SugarGh0st RAT variant, targeted AI attacks – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Cyber security experts have recently uncovered a sophisticated cyber attack campaign targeting U.S-based organizations that are involved in artificial...
Black Basta Ransomware Struck More Than 500 Organizations Worldwide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet A joint cybersecurity advisory from the Federal Bureau of Investigation, Cybersecurity and Infrastructure Security Agency, Department of Health and Human...
Get on Cybersecurity Certification Track With $145 Off These Courses – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published May 17, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Restore Damaged Files & Save Your Business for Only $50 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published May 17, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Lookback Analysis in ERP Audit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly Today, data is the key driver of success, and even small decisions can have a significant impact. Therefore, it is...
Ransomware Attacks Evolve as Average Ransom Demand Tops $1.26 Million – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Ransomware claims surged by 64% year-over-year, particularly among mid-market and emerging businesses. There was a sharp rise in “indirect” ransomware...
How to achieve ITGC automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly Step 3. Testing and Validation With the enhanced controls and continuous monitoring, the organization shifted its focus to testing and...
How to Get a VAPT Certificate? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover In today’s digital age, cybersecurity is more important than ever. Businesses that maintain the data of their clients are continually...
How to do Penetration Testing effectively – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh Do you want to enhance your organisation’s cybersecurity by identifying and addressing vulnerabilities before they can be exploited? Mastering the...
Hackers Use Fake DocuSign Templates to Scam Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A surge in phishing attacks that use emails appearing to be from DocuSign is being fueled by a Russian dark...
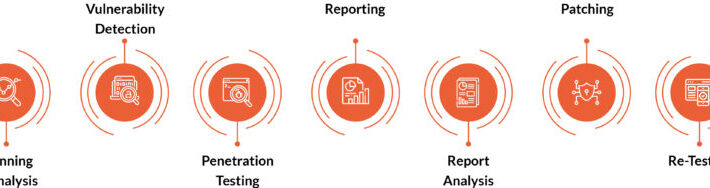
What is Web Application Penetration Testing? [+ Checklist] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh Secure code ensures the Internet runs smoothly, safely, and securely. This includes examples from our banks to online stores, all...
USENIX Security ’23 – Reusable Enclaves For Confidential Serverless Computing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Shixuan Zhao, Pinshen Xu, Guoxing Chen, Mengya Zhang, TYinqian Zhang, Zhiqiang Lin Many thanks to USENIX for publishing their outstanding...
Risks of GenAI Rising as Employees Remain Divided About its Use in the Workplace – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sonya Duffin If you use generative artificial intelligence (GenAI) tools at work, be warned: Half (53%) of your colleagues think you’re cheating,...
Questions You Need to Ask When Evaluating a Security Automation Vendor – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Doetch In the rapidly evolving landscape of cybersecurity, organizations are increasingly turning to automation to enhance their security posture. However, the...
Patient Data at Risk in MediSecure Ransomware Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Australian healthcare company MediSecure has suffered a “large scale” ransomware attack, putting individuals’ personal and health information at risk. The electronic...
UK Government Publishes AI Cybersecurity Guidance – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Geo Focus: The United Kingdom , Geo-Specific Guidance Is First Step to Global Standard, Says...
Cryptohack Roundup: Thieves Steal $45M; Hacker Returns $71M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Crypto King Indicted in Canada Rashmi Ramesh (rashmiramesh_) •...
Australia Investigating Large-Scale Medical Billing Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Geo Focus: Asia e-Prescription Provider Brings in Government on Ransomware Response Jayant Chakravarti...
Zero-Trust DNS – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Zero-Trust DNS Microsoft is working on a promising-looking protocol to lock down DNS. ZTDNS aims to solve this decades-old problem...
BreachForums seized! One of the world’s largest hacking forums is taken down by the FBI… again – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Law enforcement agencies worldwide have coordinated to take down one of the world’s largest hacker forums, scoring a victory against...













![what-is-web-application-penetration-testing?-[+-checklist]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2024/05/132602/what-is-web-application-penetration-testing-checklist-source-securityboulevard-com.png)