Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer Source: designer491 via Alamy Stock Photo As the CISO role matures in enterprise settings and security executives level...
Day: May 10, 2024
Is CISA’s Secure by Design Pledge Toothless? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer At 2024’s RSA Conference this week, brand names like Microsoft, Amazon Web Service (AWS), International Business Machines (IBM),...
Reality Defender Wins RSAC Innovation Sandbox Competition – Source: www.darkreading.com
Source: www.darkreading.com – Author: Karen Spiegelman, Features Editor Reality Defender co-founder and CEO Ben Colman (left) onstage with host Hugh ThompsonSource: RSA Conference For the second...
Ascension Healthcare Suffers Major Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: MBI via Alamy Stock Photo Healthcare provider Ascension, which operates 140 hospitals across 19 states, fell victim...
Dark Reading Confidential: The CISO and the SEC – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Transcript of Dark Reading Confidential, Episode 1: The CISO and the SEC Becky Bracken, Senior Editor, Dark Reading: Hello...
You’ve Been Breached: What Now? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jackson Shaw Jackson Shaw, Chief Security Officer, Clear Skye May 10, 2024 4 Min Read Source: Brain light via Alamy Stock Photo...
Dark Reading ‘Drops’ Its First Podcast – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kelly Jackson Higgins, Editor-in-Chief, Dark Reading Source: aleksandr Lychagin via Alamy Stock Photo At one of the first meetings Dark Reading held...
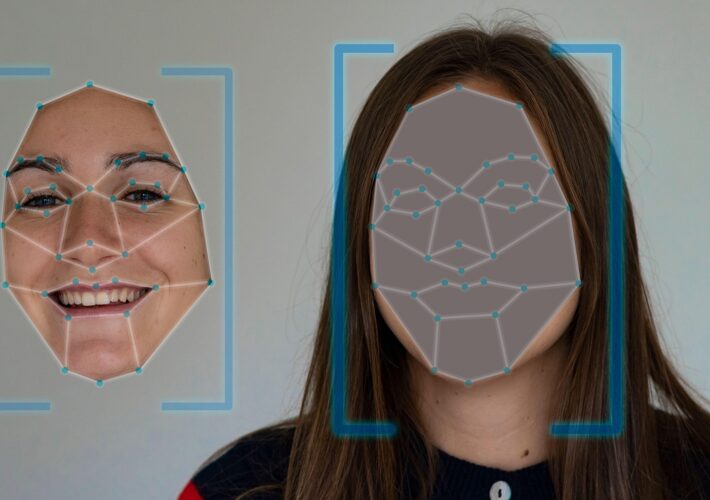
Cybersecurity in a Race to Unmask a New Wave of AI-Borne Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kelly Jackson Higgins, Editor-in-Chief, Dark Reading Source: Alfonso Fabiio Iozzino via Alamy Stock Photo RSA CONFERENCE 2024 – San Francisco – Everyone’s...
Token Security Launches Machine-Centric IAM Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Poptika via Shutterstock The shift to cloud technologies and microservices means organizations are now managing...
Boeing refused to pay $200 million LockBit ransomware demand – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Boeing has confirmed that it received a demand for a massive $200 million after a ransomware attack by the notorious...
$10 million reward offer for apprehension of unmasked LockBit ransomware leader – Source: www.exponential-e.com
Source: www.exponential-e.com – Author: Graham Cluley Do you know Dmitry Yuryevich Khoroshev? If you do, there’s a chance that you might well on the way to...
FBI warns US retailers that hackers are targeting their gift card systems – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley The FBI has issued a warning to US retailers about a financially-motivated malicious hacking ring that has been targeting employees...
BSidesSF 2024: A Community Event Anchored To Hope For The Future Of Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel You can’t see The Golden Gate Bridge from downtown San Francisco, but if you stand at the right intersections, you...
A Practical Approach to FAIR Cyber Risk Quantification – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maahnoor Siddiqui In the ever-evolving world of cybersecurity, managing risk is no longer about simply setting up firewalls and antivirus software. As...
NASA Must Improve Spacecraft Cybersecurity, GAO Report Finds – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Houston, we may have a problem. NASA’s cybersecurity framework for spacecraft development is inconsistent and must be improved, according to...
Getting Started with Software Dependency Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rhys Arkins Dependency management is a broad topic encompassing, among other things, keeping an inventory of dependencies, removing unused dependencies, and fixing...
Make WAAP Interesting Again by Quantifying Operational Efficiency and Secure by Design. – Source: securityboulevard.com
Source: securityboulevard.com – Author: SecureIQLab The adoption of the cloud is the biggest driver of the DevOps development process. Before cloud, waterfall (80’s to late 90’s)...
Recent Breaches in Israel and Iran: A Closer Look at Cybersecurity Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alberto Casares In recent times, Israel and Iran have been caught up in a series of conflicts and tensions, both on the...
USENIX Security ’23 – SMACK: Semantically Meaningful Adversarial Audio Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – SMACK: Semantically Meaningful Adversarial Audio Attack by...
Massive Online Shopping Scam Racks Up 850,000 Victims – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A group of bad actors — likely from China — is running a global cybercrime-as-a-service operation. It oversees a massive...
NSA: State-backed attackers are not after your data — they’re targeting CI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Roberts Companies in the crosshairs of advanced persistent threat (APT) actors look at data theft not as a primary objective of...
How Criminals Are Using Generative AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier There’s a new report on how criminals are using generative AI tools: Key Takeaways: Adoption rates of AI technologies among...
Beware of cyber scams: How hackers tried to scam me – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Lari Luoma has over 20 years of experience working in the fields of security and networking. For the last 13 years,...
Cloud Computing is Evolving – With a Little Help From AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , RSA Conference Sarbjeet Johal of StackPayne on How Generative AI is Improving Cloud...
ISMG Editors: Day 3 Highlights at RSA Conference 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Panel Discusses Way to Address the Job Shortage,...
Live Webinar | Digital Doppelgängers: The Dual Faces of Deepfake Technology – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Account Takeover Fraud , AI-Based Attacks , Artificial Intelligence & Machine Learning Presented by KnowBe4 60 mins ...
Live Webinar | The State of Cloud Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Dennen Monks Field Tech Strategist, CrowdStrike Dennen is passionate about helping companies achieve elegant operationalized states across people, process, and technology....
Cryptohack Roundup: BTC-e’s Alex Vinnik Pleads Guilty – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Arrests in a $43M Ponzi Scheme and Arrest in...
Tech Giants Cater to Government With AI Tools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Government , Industry Specific Mitre, Microsoft Announce Government-Focused AI Tools This Week Rashmi Ramesh (rashmiramesh_)...
Data Classification Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: In many ways, data has become the primary currency of modern organizations. It doesn’t matter whether you are a large business enterprise,...