Source: www.bitdefender.com – Author: Graham Cluley A medical lab that specialises in cancer screenings has admitted to an alarming data breach that left sensitive patient information...
Day: May 9, 2024
Smashing Security podcast #371: Unmasking LockBitsupp, company extortion, and a Tinder fraudster – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The kingpin of the LockBit ransomware is named and sanctioned, a cybersecurity consultant is charged with a $1.5 million extortion,...
Silverfort Announces New Integration with Microsoft Entra ID EAM – Source: securityboulevard.com
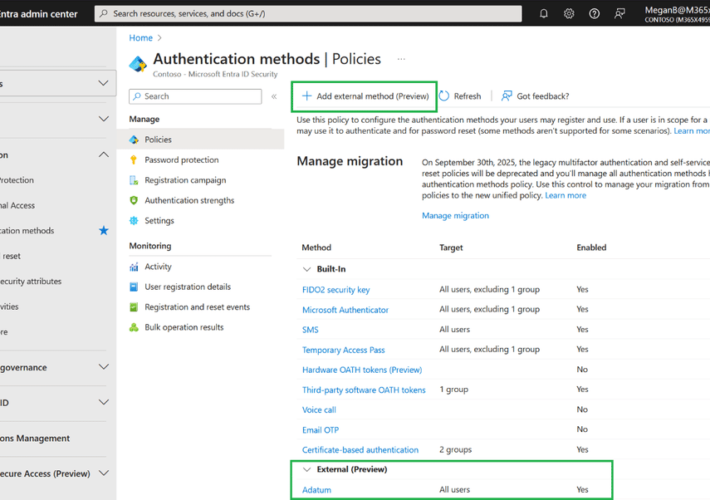
Source: securityboulevard.com – Author: Zev Brodsky Silverfort is excited to announce our integration with external authentication methods (EAM) in Microsoft Entra ID, which is now in...
Crypto Mixer Money Laundering: Samourai Founders Arrested – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja The recent crackdown on the crypto mixer money laundering, Samourai, has unveiled a sophisticated operation allegedly involved in facilitating illegal...
AI Regulation in Finance: Steering the Future with Consumer Protection at the Helm – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rebecca Kappel The financial industry is experiencing a gold rush of sorts with the integration of Artificial Intelligence (AI) technologies. With huge...
How Nudge Security is useful in a merger or acquisition – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nudge Security Blog For anyone who has been through a corporate merger or acquisition, you know that things can get…messy. Just like...
Build Strong Information Security Policy: Template & Examples – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Kelly Every organization needs to have security measures and policies in place to safeguard its data. One of the best and...
Ransomware Attacks are Up, but Profits are Down: Chainalysis – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt In the ever-evolving world of ransomware, it’s getting easier for threat groups to launch attacks – as evidence by the...
USENIX Security ’23 – “Security Is Not My Field, I’m A Stats Guy”: A Qualitative Root Cause Analysis of Barriers to Adversarial Machine Learning Defenses in Industry – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Jaron Mink, Harjot Kaur, Juliane Schmüser, Sascha Fahl, Yasemin Acar Many thanks to USENIX for publishing their outstanding USENIX...
RSAC 2024 Day 2: IoT Security Questions (and Answers) – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Gallagher RSA Conference delivers in terms of interesting dialogues with other cybersecurity professionals, and this year while there is not much...
Harnessing Cyber Risk Quantification to Safeguard Healthcare Providers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Brendan J. Fitzpatrick Welcome to Axio’s series on cybersecurity for healthcare providers, where we share expert insights and practical advice tailored to...
10 Ways K12 School Districts Can Boost Cybersecurity for the 2024-2025 School Year – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith When the school year is winding down, vacations are very front of mind. And yet, the end of one academic...
Quishing Campaign Exploits Microsoft Open Redirect Vulnerability – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Diving into a new sophisticated campaign, exploiting Microsoft’s Open Redirect vulnerability through quishing By Elad Damari, Incident Response Group Manager, Perception...
Detect and Destroy Cyber Threats with Red Piranha – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Adam Bennett, CEO, Red Piranha Red Piranha is Australia’s leading cybersecurity technology and solutions developer, manufacturer, and official member of...
Revolutionizing Cybersecurity Recruitment and Networking: The Cyberr.ai Approach – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Laurent Halimi, Founder, Cyberr In the wake of 4 million unfilled cybersecurity positions globally in 2023, conventional hiring practices...
APT trends report Q1 2024 – Source: securelist.com
Source: securelist.com – Author: GReAT For more than six years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced...
Two-thirds of organizations are not prepared for AI risks – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Artificial intelligence is the new epicenter of value creation. Employees across industries are ecstatic about deploying easily accessible generative...
News alert: Security Risk Advisors offers free workshop to help select optimal OT security tools – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Philadelphia, Pa., May 8, 2024, CyberNewsWire — Security Risk Advisors (SRA) announces the launch of their OT/XIoT Detection Selection Workshop, a...
News alert: Hunters announces full adoption of OCSF, introduces OCSF-native search – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire SAN FRANCISCO, May 7, 2024, CyberNewsWire –– Hunters, the pioneer in modern SOC platforms, today announced its full adoption of the...
UK Military Data Breach a Reminder of Third-Party Risk in Defense Sector – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Bumble Dee via Shutterstock The disclosure of a breach exposing data on over 225,000 UK military personnel...
3-Year Iranian Influence Op Preys on Divides in Israeli Society – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Ruma Aktar via Alamy Stock Photo A yearslong influence operation by Iran has been stoking the flames...
Cyolo Partners With Dragos to Unveil Holistic Secure Remote Access Solution for Critical Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Mountain View, Calif. – May 8th, 2024 – Cyolo, the secure remote access company for operational technology (OT) and industrial control systems...
Netcraft Announces New AI-Powered Innovations to Disrupt and Expose Criminal Financial Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE LONDON and SALT LAKE CITY, May 8, 2024 /PRNewswire/ — Netcraft, the global leader in digital risk protection and threat intelligence, announced its new Conversational Scam Intelligence...
ISMG Editors: Day 2 Highlights at RSA Conference 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Examining the CISO’s Role and Emerging Security Solutions...
UK Regulator Tells Platforms to ‘Tame Toxic Algorithms’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Geo Focus: The United Kingdom , Geo-Specific Ofcom Prepares to Enforce the Online Safety Act...
Live Webinar | Seamless Security: The Path to Integrated IAM Systems – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Nick Hunt Director of IAM Delivery, IDMWORKS A leader in the areas of Security, Compliance, GRC, and Identity Management over a...
CISA Directors Talk Geopolitical Threats, Election Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Government Explosion in Threat Actors, Poorly Configured Technology Compound the Risk...
Report: Undetectable Threats Found in F5’s Central Manager – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Network Firewalls, Network Access Control , Security Operations Researchers Discover Major Vulnerabilities in Popular Central Management Platform Chris Riotta (@chrisriotta) •...