Source: www.techrepublic.com – Author: Megan Crouse Security researchers in Adobe’s bug bounty program can now pick up rewards for finding vulnerabilities in Adobe Firefly and Content...
Day: May 1, 2024
Are VPNs Legal To Use? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
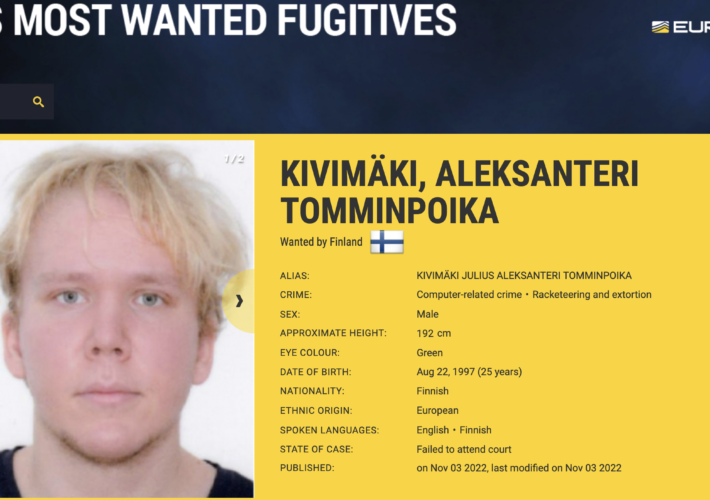
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an...
FCC Fines Major U.S. Wireless Carriers for Selling Customer Location Data – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. Federal Communications Commission (FCC) today levied fines totaling nearly $200 million against the four major carriers — including AT&T,...
Smashing Security podcast #370: The closed loop conundrum, default passwords, and Baby Reindeer – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The UK Government takes aim at IoT devices shipping with weak or default passwords, an identity thief spends two years...
Qantas Customers’ Boarding Passes Exposed in Flight App Mishap – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Stonemeadow Photography via Alamy Stock Photo Qantas, the flagship Australian airline, is investigating a privacy...
‘Cuttlefish’ Zero-Click Malware Steals Private Cloud Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: David Fleetham via Alamy Stock Photo A never-before-seen malware strain is targeting enterprise-grade and SOHO routers to...
The Cybersecurity Checklist That Could Save Your M&A Deal – Source: www.darkreading.com
Source: www.darkreading.com – Author: Craig Davies 4 Min Read Source: Cagkan Sayin via Alamy Stock Photo COMMENTARY Mergers and acquisitions (M&A) activity is making a much-anticipated...
Verizon DBIR: Basic Security Gaffes Underpin Bumper Crop of Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Security bugs are having a cybercrime moment: For 2023, 14% of all data breaches started...
Facebook at 20: Contemplating the Cost of Privacy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild, Contributing Writer SourceL Skorzewiak via Alamy Stock Photo In the 20 years since then-Harvard University student Mark Zuckerberg launched Facebook,...
MITRE’s Cyber Resiliency Engineering Framework Aligns With DoD Cyber Maturity Model Cert – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE McLean, Va. & Bedford, Mass., April 25, 2024 — MITRE’s Cyber Resiliency Engineering Framework (CREF) NavigatorTM now incorporates the US...
Philippines Pummeled by Assortment of Cyberattacks & Misinformation Tied to China – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: robertharding via Alamy Stock Photo A recent massive spike in cyber misinformation and hacking campaigns against the...
Jason Haddix Joins Flare As Field CISO – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Montreal, Quebec, Canada – April 25, 2024 – Flare, a global leader in Threat Exposure Management, is pleased to announce that renowned...
Intel Harnesses Hackathons to Tackle Hardware Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: kawin ounprasertsuk via Alamy Stock Photo Ever since the first Hack@DAC hacking competition in 2017, thousands of...
LockBit, Black Basta, Play Dominate Ransomware in Q1 2024 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 LockBit, Black Basta and Play have been observed to be the most active ransomware groups in Q1 2024, with Black Basta...
UnitedHealth CEO Confirms Breach Tied to Stolen Credentials, No MFA – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The ransomware attack that hit US health tech titan Change Healthcare earlier this year was orchestrated by hackers who leveraged stolen...
1 in 5 US Ransomware Attacks Triggers Lawsuit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Nearly one in five (18%) ransomware incidents in the US led to a lawsuit in 2023, with 123 filed so far,...
Lawsuits and Company Devaluations Await For Breached Firms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new report has laid bare the significant financial and reputational costs stemming from serious cyber-attacks, including what are often unplanned...
How SaaS-Based Identity Governance Can Help Future-Proof Your Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Evaluate your needs and prioritize solutions that offer open integration and independence from the single-vendor trend, ensuring robust IGA that aligns...
Hacking and Cybersecurity – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Trends to Look Out for in 2024 By Yashin Manraj, CEO, Pvotal Technologies For cybersecurity professionals, remaining effective requires staying on...
Stop Managing Identities, Segment them Instead – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Sagie Dulce, VP Research, Zero Networks A Brief History of Identity Management For as long as there have been identities,...
Good Security Is About Iteration, Not Perfection. – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Craig Burland, CISO, Inversion6 In the dynamic and unpredictable realm of cybersecurity, striving for perfect solutions can be a...
GitGuardian Researchers Find Thousands of Leaked Secrets in PyPI (Python Package Index) Packages – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Dwayne McDaniel, GitGuardian Developer and Security Advocate, GitGuardian The modern world of DevOps means relying on our code connecting...
Enhancing Cybersecurity Defenses: The role of Voice Cloning in Penetration Testing – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Alex Serdiuk, CEO, Respeecher Newer and more impactful technological advancements are making the quest for foolproof cybersecurity measures more critical...
Data Breach Search Engines – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Navigating Access and Security in the Stolen Credentials Landscape By Tom Caliendo, Cybersecurity Reporter, Co-Founder at Brocket Consulting LLC In the...
UnitedHealth Group Pays Ransom After Cyberattack: What You Need to Know – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary In an alarming revelation, officials from the Minnesota-based UnitedHealth Group disclosed on Monday that the health insurance and services giant fell...
Cybersecurity Trends and Predictions for 2024 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Nick France, CTO at Cybersecurity Leader Sectigo Given the fact that bad actors are always on the prowl, 2024 is...
AI is Revolutionizing Phishing for Both Sides. What will make the Difference? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Thanks to AI, phishing attacks are better than ever. So is our ability to stop them. By Antonio Sanchez, Principal Cybersecurity...
Venafi Launches 90-Day TLS Certificate Renewal Initiative – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Venafi today launched an initiative to help organizations prepare to implement and manage certificates based on the Transport Layer Security...
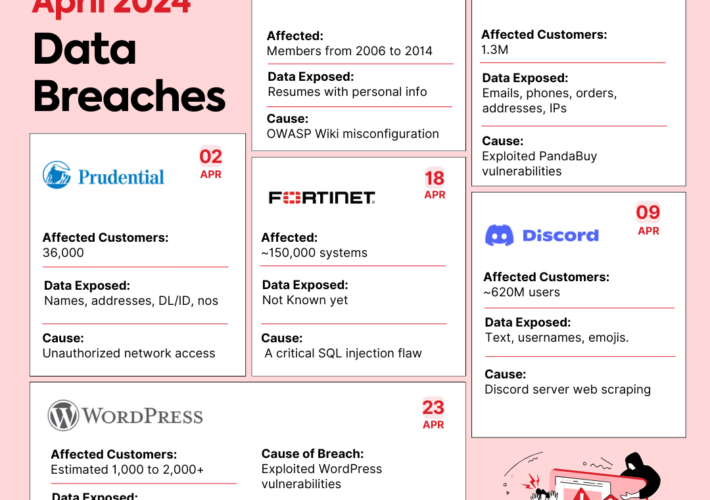
Data Breaches in April 2024 – Infographic – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shubham Jha Data breaches are like uninvited guests at a party – they show up unexpectedly, take what they want, and leave...