Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: sezer ozger via Alamy Stock Photo India’s embassy in Cambodia is working with officials there...
Month: April 2024
Collaboration Needed to Fight Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Brian Neuhaus 4 Min Read Source: Wavebreakmedia Ltd IFE-210813 via Alamy Stock Photo COMMENTARY The dramatic imagery of law enforcement “kicking down...
Africa Tackles Online Disinformation Campaigns During Major Election Year – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: CG Alex via Shutterstock A dramatic increase in online disinformation attacks against African nations and international agencies...
UN Adopts Resolution for ‘Secure, Trustworthy’ AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo The United Nations on Thursday adopted a resolution...
Chinese State-Sponsored Hackers Charged, Sanctions Levied by US – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Rokas Tenys via Alamy Stock Photo The Department of Justice this week charged seven Chinese...
It’s Time to Stop Measuring Security in Absolutes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Huber Robert Huber, Chief Security Officer at Tenable March 25, 2024 3 Min Read Source: Dzmitry Skazau via Alamy Stock Photo...
A Database-Oriented Operating System Wants to Shake Up Cloud Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: James Thew via Alamy Stock Photo Is it possible to replace Linux as the heart of serverless...
ISO/IEC 27001:2022 Self-assessment questionnaire
The document focuses on assessing readiness for ISO/IEC 27001:2022 Information Security Management System (ISMS) certification. It outlines key aspects such as determining external and internal issues...
IoT Security Architecture and Policy for the Home – a Hub Based Approach
Home IoT devices and systems need to manage security with minimal – and potentially no – consumer intervention, and without the consumer having any specialist knowledge...
INTELIGENCIA ARTIFICIAL Y CIBERSEGURIDAD
The guide on “AI and Cybersecurity” provides comprehensive insights into the factors influencing the effectiveness of AI components, defining the requirements for human operators supervising and...
Cybersecurity and resiliency of Europe’s communications infrastructures and networks
The document provides a comprehensive analysis of threats, vulnerabilities, and risk scenarios in the telecommunications sector, focusing on public electronic communications networks and core Internet infrastructure....
INFORMATION SECURITY TRAINING AWARENESS DECK
The document covers various aspects of information security, starting with the agenda which includes topics like Incident Response, Safe Practices, Data Classification, Information Security, Pillars of...
XZ Utils Backdoor Vulnerability (CVE-2024-3094) Advisory – Source: securityboulevard.com
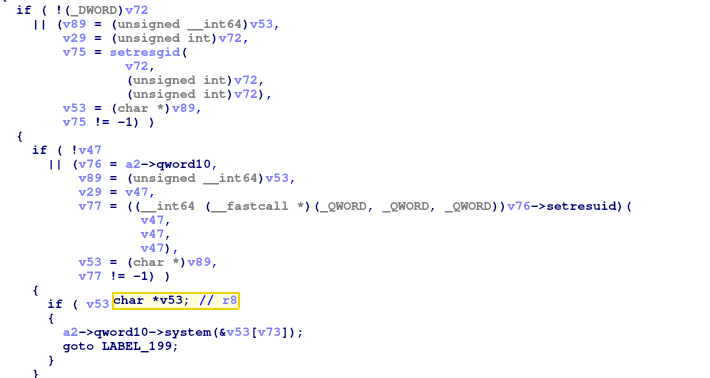
Source: securityboulevard.com – Author: NSFOCUS Overview NSFOCUS CERT recently detected that a backdoor vulnerability in XZ Utils (CVE-2024-3094) was disclosed from the security community, with a...
Bombshell in SSH servers! What CVE-2024-3094 means for Kubernetes users – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amit Schendel On March 29, 2024, Red Hat disclosed CVE-2024-3094, scoring a critical CVSS rating of 10. Stemming from a supply chain...
Critical Backdoor Found in XZ Utils (CVE-2024-3094) Enables SSH Compromise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Abai A critical vulnerability (CVE-2024-3094) was discovered in the XZ Utils library on March 29th, 2024. This severe flaw allows attackers...
Cybersecurity Tabletop Exercises: How Far Should You Go? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity With global cyber threats and other international tensions growing, what scenarios should state and local governments consider when conducting...
Poland launches inquiry into previous government’s spyware use – Source: www.theguardian.com
Source: www.theguardian.com – Author: Shaun Walker in Warsaw Poland has launched an investigation into its previous government’s use of the controversial spyware Pegasus, with a parliamentary...
Ross Anderson – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Ross Anderson Ross Anderson unexpectedly passed away Thursday night in, I believe, his home in Cambridge. I can’t remember when...