The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Month: April 2024
Active Directory Security Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft warns Gmail blocks some Outlook email as spam, shares fix – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has confirmed that some Outlook.com users are experiencing issues with emails being blocked and marked as spam when trying...
Winnti’s new UNAPIMON tool hides malware from security software – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Chinese ‘Winnti’ hacking group was found using a previously undocumented malware called UNAPIMON to let malicous processes run without...
Omni Hotels experiencing nationwide IT outage since Friday – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Omni Hotels & Resorts has been experiencing a chain-wide outage that brought down its IT systems on Friday, impacting reservation,...
New Chrome feature aims to stop hackers from using stolen cookies – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google announced a new Chrome security feature called ‘Device Bound Session Credentials’ that ties cookies to a specific device, blocking...
Google agrees to delete Chrome browsing data of 136 million users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google has agreed to delete billions of data records collected from 136 million Chrome users in the United States, as...
Block Ads And Free Up The Internet For An Extra 20% Off – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published April 3, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
xz Utils Backdoor – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier xz Utils Backdoor The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source...
Declassified NSA Newsletters – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Through a 2010 FOIA request (yes, it took that long), we have copies of the NSA’s KRYPTOS Society Newsletter, “Tales...
Customer Story | Content Filter Protects Student Safety, Data Security, and CIPA Compliance At Azusa Unified School District – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Fritchen How Azusa’s technology team makes web filtering and online safety for students easy with Content Filter by ManagedMethods Like many...
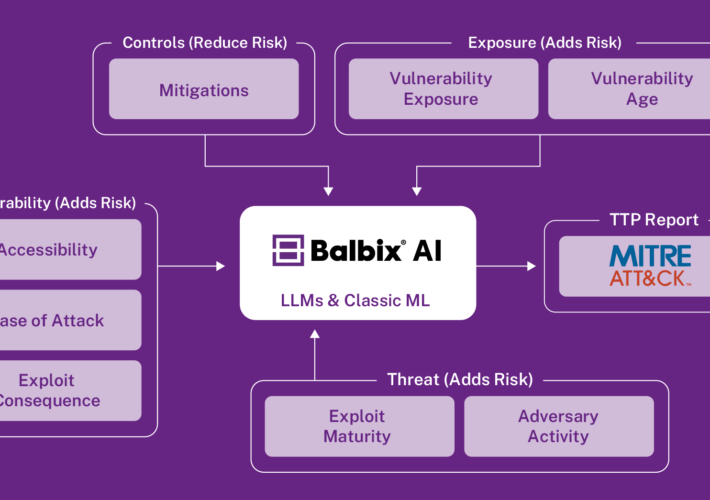
Prioritizing Cyber Risk: Get a leg up with AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aravind Iyengar In the previous blog post, we described how Balbix leverages AI to provide a unified and comprehensive visibility into your...
Guide to New CSRD Regulation for Data Center Operators – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi In the ever-evolving landscape of corporate sustainability, the European Union’s Corporate Sustainability Reporting Directive (CSRD) stands as a landmark regulation,...
How to Escape the 3 AM Page as a Kubernetes Site Reliability Engineer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stevie Caldwell It’s Saturday night. You’re out to dinner with friends. Suddenly, a familiar tune emits from your pocket. Dread fills you...
A Deep Dive on the xz Compromise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joao Correia xz is a widely distributed package that provides lossless compression for both users and developers, and is included by default...
xz Utils Backdoor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source compression utility, was...
Chrome’s Incognito Mode Isn’t as Private as You Think — but Google’s Not Sorry – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Class action attorney David Boies asked for $5,000 per user, but got nothing—except some assurances Google will delete data it...
Declassified NSA Newsletters – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Through a 2010 FOIA request (yes, it took that long), we have copies of the NSA’s KRYPTOS Society Newsletter, “Tales...
The Challenges of Zero Trust 800-207 and Advocating for Prescriptive Controls – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Allers In the rapidly evolving cybersecurity landscape, a Zero Trust (ZT) model has emerged as a beacon of hope, promising enhanced...
Report Slams Microsoft for Security Blunders in Chinese Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Email Threat Protection , Fraud Management & Cybercrime Hack Targeting Top Government Officials ‘Was Preventable,’ Scathing...
New Regulations Pose Compliance Challenges – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Standards, Regulations & Compliance , Training & Security Leadership How to Navigate New SEC Rules Information Security Media...
How to Hire, Retain and Inspire Exceptional Employees – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Professional Certifications & Continuous Training , Training & Security Leadership Leading Means Admitting What You Don’t Know – And Other Tips...
Sam Altman Out as OpenAI Startup Fund Owner – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Altman’s Role as Fund’s Sole Owner Was Meant to Be...
Live Webinar | The CISO’s Guide to a Strong Security Culture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Security Awareness Programs & Computer-Based Training , Training & Security Leadership Presented by KnowBe4 60 Minutes Let’s...
Rubrik IPO Filing Reveals Sales Acceleration, Growing Losses – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Next-Generation Technologies & Secure Development , Privacy In First Cybersecurity IPO Filing Since 2021, Rubrik Describes...
Hackers Update Vultur Banking Malware With Remote Controls – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Attackers Can Now Download, Alter and Delete Files – Plus...
Ransomware, Junk Bank Accounts: Cyber Threats Proliferate in Vietnam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Jose Vilchez via Alamy Stock Photo For one week last month, Vietnamese brokerage VNDirect Cyber Systems shut...
China-Linked Threat Actor Taps ‘Peculiar’ Malware to Evade Detection – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Panchenko Vladimir via Shutterstock Researchers have spotted Earth Freybug, a China-linked threat actor, using a new malware...
Fortanix Builds Private Search for AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer The inner-functioning of AI-powered search is more complex than plain-text search via Google when it comes to extracting...
NIST Wants Help Digging Out of Its NVD Backlog – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: GK Images via Alamy Stock Photo After warning it can’t keep up with the exploding...