Source: www.techrepublic.com – Author: Ben Abbott Raj Samani, Chief Scientist. Image: Rapid7 New research from cyber security firm Rapid7 has shown the ransomware attacks that IT...
Month: April 2024
Get a Lifetime of VPN Protection for Just $16 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published April 4, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
5 Best Password Managers for Android in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Best overall password manager for Android: Bitwarden Best for smaller teams: NordPass Best for remote workers: 1Password Best for large...
Google Cloud/Cloud Security Alliance Report: IT and Security Pros Are ‘Cautiously Optimistic’ About AI – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The C-suite is more familiar with AI technologies than their IT and security staff, according to a report from the...
9 Must-Do Tips to Secure Ubuntu Server – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: In today’s world, if you’re not constantly working to secure your servers, you’re already 10 steps behind every hacker on the planet....
Authy vs Google Authenticator: Two-Factor Authenticator Comparison – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares The number of businesses affected by data breaches has risen over the years, showcasing that passwords alone fail to provide...
This IT Career Kickstarter Bundle is An Extra 20% Off Through April 7th – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published April 3, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
New Latrodectus malware replaces IcedID in network breaches – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A relatively new malware called Latrodectus is believed to be an evolution of the IcedID loader, seen in malicious email...
Visa warns of new JSOutProx malware variant targeting financial orgs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Visa is warning about a spike in detections for a new version of the JsOutProx malware targeting financial institutions and...
Microsoft fixes Outlook security alerts bug caused by December updates – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has fixed an issue that triggers erroneous Outlook security alerts when opening .ICS calendar files after installing the December...
Hoya’s optics production and orders disrupted by cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Hoya Corporation, one of the largest global manufacturers of optical products, says a “system failure” caused servers at some of...
US cancer center data breach exposes info of 827,000 patients – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cancer treatment and research center City of Hope is warning that a data breach exposed the sensitive information of over...
New HTTP/2 DoS attack can crash web servers with a single connection – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Newly discovered HTTP/2 protocol vulnerabilities called “CONTINUATION Flood” can lead to denial of service (DoS) attacks, crashing web servers with...
The Biggest Takeaways from Recent Malware Attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Blink Ops Among the never-ending list of malicious software that threat actors use in cyber attacks are viruses, worms, trojans,...
Fake Lawsuit Threat Exposes Privnote Phishing Sites – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A cybercrook who has been setting up websites that mimic the self-destructing message service privnote.com accidentally exposed the breadth of their...
7 strategic ransomware remediation tactics for enterprise resilience – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: For businesses of all sizes, ransomware is a growing threat. Ransomware typically encrypts critical data, rendering it completely or...
Google patches Pixel phone zero-days after exploitation by “forensic companies” – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Google has issued a security advisory to owners of its Android Pixel smartphones, warning that it has discovered someone has...
What makes a ransomware attack eight times as costly? Compromised backups – Source: www.exponential-e.com
Source: www.exponential-e.com – Author: Graham Cluley Any organisation that has tried to recover from a ransomware attack knows that it can be time-consuming and costly. Companies...
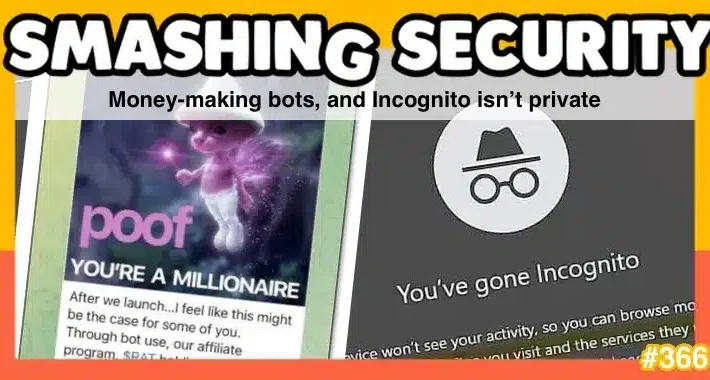
Smashing Security podcast #366: Money-making bots, and Incognito isn’t private – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Google says it is deleting your Google Chrome Incognito private-browsing data that it should never have collected anyway. Can a...
R I S K A P P E T I T E –C R I T I C A L TOSUCCESS U S I N G R I S K A P P E T I T E T O T H R I V E I N A C H A N G I N G W O R L D
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Reporting Cybersecurity Risk to the Board of Directors
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Reporting Cyber Risk to Boards
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
LockBit Scrambles After Takedown, Repopulates Leak Site with Old Breaches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The impact of Operation Cronos continues to hinder the LockBit ransomware group’s operations and the gang begun posting fake victim claims...
Jackson County IT Systems Hit By Ransomware Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Jackson County in Missouri, United States, reported significant disruptions within its IT systems on Tuesday, caused by a ransomware attack. The...
New JSOutProx Malware Targets Financial Firms in APAC, MENA – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity researchers have uncovered a new iteration of the JSOutProx malware, a sophisticated attack tool designed to target financial organizations across...
Red Team Operations Concepts
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Critical Security Flaw Exposes 1 Million WordPress Sites to SQL Injection – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Primakov via Shutterstock Attackers can exploit a critical SQL injection vulnerability found in a widely used WordPress...
Cyberattack Shutters Some Operations at Japanese Lens Manufacturer – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: ronstik via Alamy Stock Photo Japanese lens manufacturer Hoya is investigating a cyber incident that...
How CISOs Can Make Cybersecurity a Long-Term Priority for Boards – Source: www.darkreading.com
Source: www.darkreading.com – Author: Shaun McAlmont 5 Min Read Source: Lev Dolgachov via Alamy Stock Photo COMMENTARY Cybersecurity has never been more critical for responsible corporate...
AI’s Dual Role in SMB Brand Spoofing – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Bulat Silvia via Alamy Stock Photo Artificial intelligence (AI) is simultaneously making it easier for adversaries to...