Source: securityboulevard.com – Author: Rohan Timalsina The Ubuntu security team recently addressed several Apache HTTP Server vulnerabilities in Ubuntu 23.10, Ubuntu 23.04, Ubuntu 22.04 LTS, Ubuntu...
Month: April 2024
Preparing for Holiday Cyberattacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nik Hewitt How can security teams be ready for holiday cyberattacks and a seasonal peak in cybercrime? Holiday cyberattacks are on the...
Debian 12: Redefining Stability and Innovation in Open-Source Operating Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anca Trusca Debian holds a distinguished position. Recognized as one of the oldest and most trusted distributions within the Linux ecosystem, Debian...
KapeKa Backdoor: Russian Threat Actor Group’s Recent Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja In the realm of cybersecurity, vigilance is paramount. Recent discoveries have shed light on a previously undisclosed threat known as...
Ensuring RBI Compliance: Crucial Cybersecurity Measures to Protect Financial Standing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover The rise of digital technology has provided great convenience to the banking sector, but it has also opened up the...
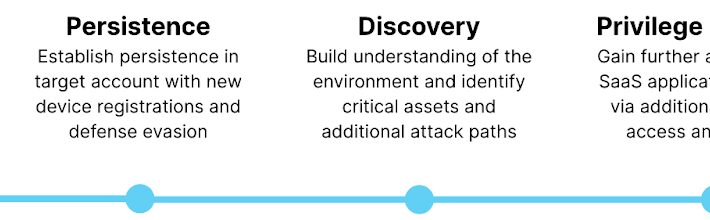
MITRE ATT&CK v15: A Deeper Dive into SaaS Identity Compromise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Farah Iyer The MITRE ATT&CK framework is a continually evolving resource, tracking the tactics, techniques, and procedures (TTPs) employed by adversaries across...
No more 12345: devices with weak passwords to be banned in UK – Source: www.theguardian.com
Source: www.theguardian.com – Author: Guardian staff and agency Tech that comes with weak passwords such as “admin” or “12345” will be banned in the UK under...
Change the law on computer evidence with an amendment to data protection bill | Letter – Source: www.theguardian.com
Source: www.theguardian.com – Author: Guardian Staff It is now clear that the Post Office was advised by its lawyers to delay disclosing some evidence that would...
Whale Song Code – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Whale Song Code During the Cold War, the US Navy tried to make a secret code out of whale song....
Friday Squid Blogging: Searching for the Colossal Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Searching for the Colossal Squid A cruise ship is searching for the colossal squid. As usual,...
Long Article on GM Spying on Its Cars’ Drivers – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments L-A-R-A • April 26, 2024 11:49 AM noname, be sure to read GM’s statements carefully. They said they’d...
The Rise of Large-Language-Model Optimization – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The web has become so interwoven with everyday life that it is easy to forget what an extraordinary accomplishment and...
Dan Solove on Privacy Regulation – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Law professor Dan Solove has a new article on privacy regulation. In his email to me, he writes: “I’ve been...
Microsoft and Security Incentives – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Former senior White House cyber policy director A. J. Grotto talks about the economic incentives for companies to improve their...
Using Legitimate GitHub URLs for Malware – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting social-engineering attack vector: McAfee released a report on a new LUA malware loader distributed through what appeared to be...
FCC Fines US Cell Carriers $200M for Selling Location Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance Commission Approves Long-Anticipated Fines for Verizon, T-Mobile, AT&T and Sprint...
Live Webinar | Protecting Your AI: Strategies for Securing AI Systems – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Shan Rao Group Product Manager, Google Cloud Shan Rao leads Google’s AI Security and Privacy initiatives as the Group Product Manager....
Harnessing AI: A Step-by-Step Guide for Job Seekers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Recruitment & Reskilling Strategy How ChatGPT Can Help You...
Career Spotlight: Growing Need for Technology Legal Analysts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Legislation & Litigation , Professional Certifications & Continuous Training High Demand for Experts Who Know Law Plus AI,...
Benefits of a Unified CNAPP and XDR Platform – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 More companies and their CISOs are embracing hybrid and cloud-native infrastructure. There are two drivers for this, according to Ganesh Pai,...
Major Areas of Cybersecurity Focus for Medical Device Makers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Nastassia Tamari of the FDA on Top Challenges During Premarket Device Submissions Marianne Kolbasuk McGee (HealthInfoSec) • April 24, 2024 ...
Why Many Healthcare Sector Entities End Up Paying Ransoms – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 While most healthcare sector organizations hit with ransomware attacks never imagine giving in to extortion demands, the pressures they face in...
Live Webinar | Building Security from Within: Empowering Software Teams for Cyber Resilience – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Ed Adams CEO, Security Innovation Mr. Adams is a software quality and security expert with 20+ years of industry experience. He...
ESET PROTECT Portfolio Now Includes New MDR Tiers and Features – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN DIEGO, April 29, 2024/PRNewswire/ — ESET, a global leader in cybersecurity solutions, today announced the launch of two new Managed...
R Programming Bug Exposes Orgs to Vast Supply Chain Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Billion Photos via Shutterstock A high-severity vulnerability in an R programming language process could expose organizations using...
Okta: Credential-Stuffing Attacks Spike via Proxy Networks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: Ahmed Zaggoudi via Alamy Stock Photo Credential-stuffing attacks targeting online services are spiking due to...
Cybersecurity Is Becoming More Diverse … Except by Gender – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Valeriy Kachaev via Alamy Stock Photo Right now, in 2024, at least three of every four cybersecurity...
13.4M Kaiser Insurance Members Affected by Data Leak to Online Advertisers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Wirestock, Inc. via Alamy Stock Photo Hard on the heels of a significant data theft...
‘Muddling Meerkat’ Poses Nation-State DNS Mystery – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Mrinal Pal via Shutterstock During an investigation into the activities of a threat group providing domain name...
Addressing Risk Caused by Innovation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Steve Soukup 4 Min Read Source: NicoElNino via Alamy Stock Photo COMMENTARY In today’s fast-paced world, most businesses are racing to incorporate...