Source: www.bleepingcomputer.com – Author: Lawrence Abrams Laptop and tablet accessories maker Targus disclosed that it suffered a cyberattack disrupting operations after a threat actor gained access...
Month: April 2024
William Wragg resigns from two Commons roles after divulging MPs’ phone numbers – Source: www.theguardian.com
Source: www.theguardian.com – Author: Nadeem Badshah The Conservative MP who divulged colleagues’ personal phone numbers to someone he met on a dating app as part of...
How Avast One Silver adapts to your unique online world – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog In the ever-evolving landscape of the digital world, safeguarding your online presence has become more a necessity than a choice....
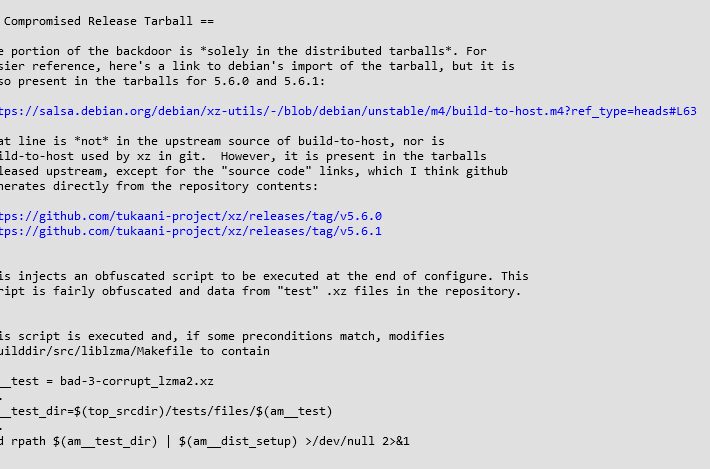
CVE-2024-3094: RCE Vulnerability Discovered in XZ Utils – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover CVE-2024-3094 is a critical Remote Code Execution (RCE) vulnerability found in the popular open-source XZ Utils library. This vulnerability affects...
10 Million Devices Were Infected by Data-Stealing Malware in 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy A surge in data-stealing malware incidents targeted nearly 10 million devices in 2023, with cybercriminals extracting an average of 50.9...
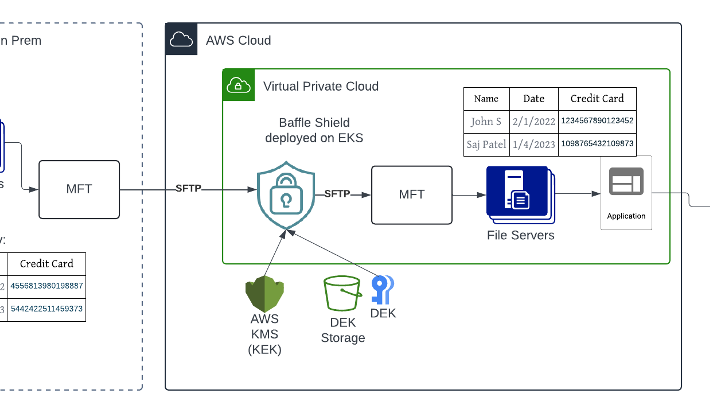
A Case Study for Protecting Files with Sensitive Data in the Cloud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sushant Rao, SVP of Marketing Financial institutions and healthcare providers deal with a vast amount of sensitive data like PII and PHI...
Google Adds Security Command Center Enterprise to Mandiant Portfolio – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Google added a Security Command Center Enterprise platform to unify the management of security operations (SecOps) to its Mandiant portfolio...
Hashicorp Versus OpenTofu Gets Ugly – Source: securityboulevard.com
Source: securityboulevard.com – Author: Steven J. Vaughan-Nichols When HashiCorp dumped its open-source Mozilla license for the Business Source License (BSL 1.1) for its flagship program, infrastructure...
USENIX Security ’23 – Lukas Seidel, Dominik Maier, Marius Muench – Forming Faster Firmware Fuzzers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2024/04/usenix-security-23-lukas-seidel-dominik-maier-marius-muench-forming-faster-firmware-fuzzers/ Category & Tags: Security Bloggers Network,Security Conference,Security...
Barracuda Report Provides Insight into Cybersecurity Threat Severity Levels – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard An analysis of high-severity threats in 2023 detected by Barracuda Networks found that 66,000 incidents needed to be escalated to...
HHS: Health Care IT Helpdesks Under Attack in Voice Scams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A beleaguered healthcare industry, already a top target of cybercriminals, is under attack again. Bad actors recently have been using...
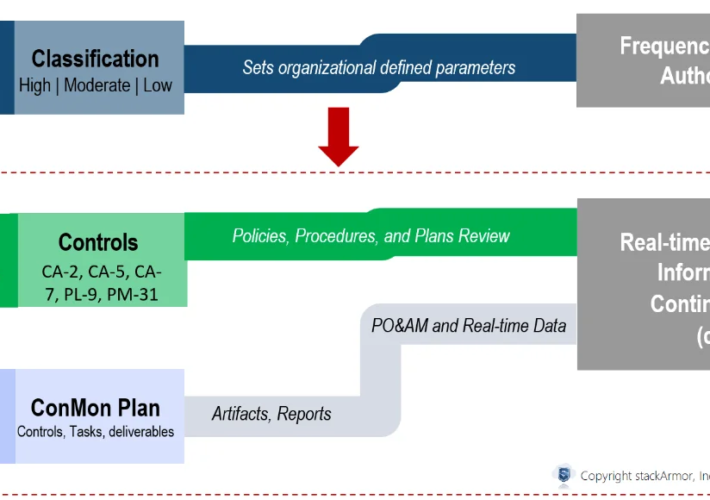
Continuous ATO: Going from Authority to Operate (ATO) to Ability to Respond – Source: securityboulevard.com
Source: securityboulevard.com – Author: stackArmor As agencies modernize and increasingly move critical business processes and data online especially using cloud computing services, Federal agencies and their...
Meta Will Label AI-Generated Content Starting In May – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Tech Giant Asks Creators to Declare Content with ‘Made with...
Hugging Face Vulnerabilities Highlight AI-as-a-Service Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Researchers Say Illegal Access to Private AI models Can Enable...
Live Webinar | The CISO’s Handbook: Blueprint for Navigating Identity Security & SAP Transformations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Jody Paterson Senior Director of Product, SailPoint The co-founder, CEO and Chairman of ERP Maestro, inc (The first cloud based SAP...
Open-Source Foundations Join Forces on Digital Supply Chain – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management Europe’s Cyber Resilience Act Pressures Open-Source Foundations and Manufacturers Akshaya Asokan (asokan_akshaya) , David...
US EPA Investigates Alleged Data Breach by Government Hacker – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Government , Incident & Breach Response , Industry Specific Hacker Claims to Leak Trove of Records Belonging to Environmental Protection Agency...
Vietnamese Cybercrime Group CoralRaider Nets Financial Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: incamerastock via Alamy Stock Photo A newcomer cybercrime group linked to Vietnam has targeted individuals and organizations...
Home Depot Hammered by Supply Chain Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading 1 Min Read Source: Ian Dagnall via Alamy Stock Photo A hacking forum leak has led...
Round 2: Change Healthcare Targeted in Second Ransomware Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: Lenetstan via Shutterstock Change Healthcare reportedly is facing another attack, this time by ransomware gang...
Wyden Releases Draft Legislation to End Federal Dependence on Insecure, Proprietary Software – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Washington, D.C. – Following a new report about how shambolic cybersecurity practices by a federal technology contractor enabled a massive hack of the...
Software-Defined Vehicle Fleets Face a Twisty Road on Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Open Studio via Shutterstock When Israel-based REE Automotive designed its P7 electric vehicle chassis, it worked from...
The Fight for Cybersecurity Awareness – Source: www.darkreading.com
Source: www.darkreading.com – Author: Erik Gross 3 Min Read Source: Mopic via Alamy Stock Photo COMMENTARY The recent movie The Beekeeper begins with a cyberattack against a victim...
Scams exposed! The most deceptive tax season traps (2024) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Cyber scammers love tax season. Emotions run high and it’s easy for scammers to prey on FUD (fear, uncertainty...
Best Practices Q&A: Guidance about what directors need to hear from CISOs — from a board member – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido CISOs can sometimes be their own worst enemy, especially when it comes to communicating with the board...
Critical RCE bug in 92,000 D-Link NAS devices now exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney Attackers are now actively targeting over 92,000 end-of-life D-Link Network Attached Storage (NAS) devices exposed online and unpatched...
Google rolls out new Find My Device network to Android devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney Google is rolling out an upgraded Find My Device network to Android devices in the United States and...
Hackers deploy crypto drainers on thousands of WordPress sites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Almost 2,000 hacked WordPress sites now display fake NFT and discount pop-ups to trick visitors into connecting their wallets to...
Cyberattack on UK’s CVS Group disrupts veterinary operations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas UK veterinary services provider CVS Group has announced that it suffered a cyberattack that disrupted IT services at its practices...
Notepad++ wants your help in “parasite website” shutdown – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma The Notepad++ project is seeking the public’s help in taking down a copycat website that closely impersonates Notepad++ but is not...