Source: www.techrepublic.com – Author: Fiona Jackson Apple sent a threat notification to iPhone users in 92 countries on April 10 informing them that their device was...
Month: April 2024
Sophos Study: 94% of Ransomware Victims Have Their Backups Targeted By Attackers – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Organisations that have backed up their sensitive data may believe they are relatively safe from ransomware attacks; however, this is...
Friday Squid Blogging: The Awfulness of Squid Fishing Boats – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments vas pup • April 12, 2024 5:15 PM Fourteen Israeli professors awarded top EU research grants h ttps://www.timesofisrael.com/three-hebrew-university-professors-awarded-top-eu-research-grants/...
Smuggling Gold by Disguising it as Machine Parts – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier HomeBlog Smuggling Gold by Disguising it as Machine Parts Someone got caught trying to smuggle 322 pounds of gold (that’s...
Layer 7 Visibility What are the Benefits?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Introduction to Kubernetes Networking and Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Defense Industrial Base Cybersecurity Strategy 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISA Warns of Compromised Microsoft Accounts – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic CISA issued a fresh CISA emergency directive in early April instructing U.S. federal agencies to mitigate risks stemming from the breach...
Balbix Guide to XZ Utils Backdoor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dragos Josanu XZ Utils is a collection of open-source command-line tools for lossless data compression, including XZ and LZMA. It is an...
USENIX Security ’23 – Fast IDentity Online with Anonymous Credentials (FIDO-AC) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
NVD’s Backlog Triggers Public Response from Cybersec Leaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeff Martin Just a few weeks ago, we wrote about how the National Vulnerability Database (NVD) is seriously behind in enriching CVEs....
How to Reduce the Risk of Using External AI Models in Your SDLC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Roy Blit Understand how AI models add risk and how to address it. In the rapidly evolving landscape of artificial intelligence (AI),...
The XZ backdoor: What security managers can learn – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden In the case of the XZ breach, this backdoor could give the attacker access to anything from login information to...
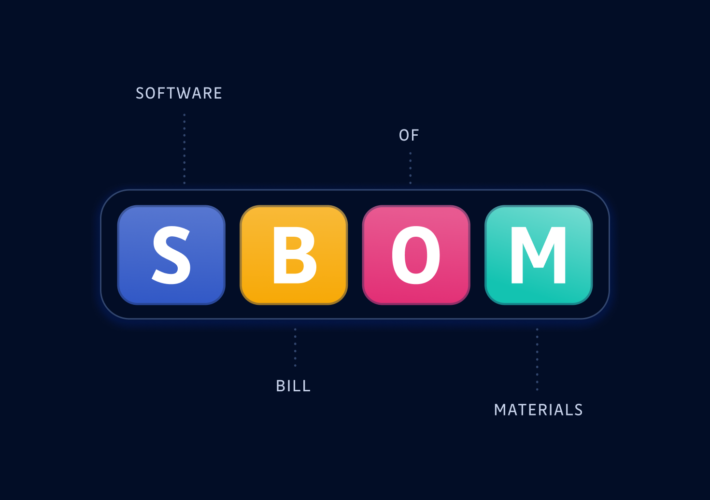
Why you need an SBOM (Software Bill Of Materials) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Greg Bulmash There’s been a lot of talk about SBOMs in tech media. This blog post will help answer three crucial questions...
Shadow AI: The Murky Threat to Enterprise Adoption of Generative AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Fulkerson Generative AI (GenAI) technologies, especially large language models like OpenAI’s GPT-4, continue to generate interest among enterprises eager to gain...
Sisense Hacked: CISA Warns Customers at Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings The analytics firm kept big organizations’ secrets in an insecure AWS bucket. The government says victims include the “critical infrastructure...
Randall Munroe’s XKCD ‘Tick Marks’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
UK Markets Authority Warns of AI Market Capture by Big Tech – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development CMA Says Market Is Becoming more Verticially Integrated Akshaya Asokan...
PE Firm Accuses Synopsys of Breaching Exclusivity Agreement – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Governance & Risk Management , Next-Generation Technologies & Secure Development Sunstone Partners: We Had a Letter of Intent...
Cloned Voice Tech Is Coming for Bank Accounts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Fraud Management & Cybercrime , ID Fraud Experts Warn AI Tools Can Now Compromise Voice...
US Cyber Command Expanded ‘Hunt Forward’ Operations in 2023 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Government US Cyber Mission Force Led 22 Defensive Cyber Operations in...
Safeguarding America’s Future: Mitigating the Implications of Chinese Control Over U.S. Critical Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary by Lena Allen Introduction In this era of unprecedented technological interconnectedness, the safeguarding of critical infrastructure against cyber threats has ascended...
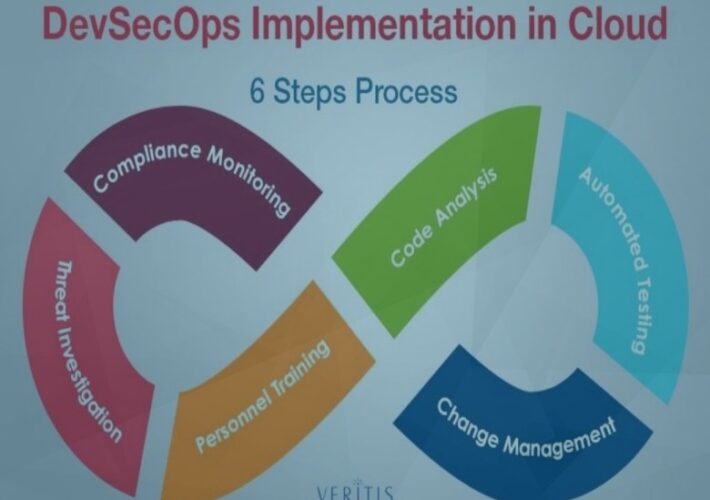
DevSecOps Practices for a Secure Cloud – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin How to start ahead of the curve? By Vishakha Sadhwani, Customer Engineer, Google Cloud In today’s rapidly evolving technological landscape, a...
Vendors Beware of the Cybersecurity Audit – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Caroline McCaffery, Co-Founder and CEO of ClearOPS Introduction to Vendor Management Why does every license agreement and data protection addendum,...
How to protect company data in the gig economy – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Zac Amos, Features Editor, Rehack.com. Hiring gig workers and freelancers has a lot of business benefits, allowing companies to utilize the contractors’...
How artificial intelligence is revolutionizing cyber security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: gmack By Shira Landau, Editor-in-Chief, CyberTalk.org. In recent years, artificial intelligence (AI) has become one of the most sure-fire and strategic tools...
Nmap for Pentester – PORT STATE
The document discusses the different states of ports that Nmap recognizes during network scanning, including Open, Closed, Filtered, Unfiltered, Open|Filtered, and Closed|Filtered ports. It provides details...
CISA Urges Immediate Credential Reset After Sisense Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Cybersecurity and Infrastructure Security Agency (CISA) has disclosed a breach affecting business analytics provider Sisense and urged its customers...
Palo Alto Networks Warns About Critical Zero-Day in PAN-OS – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A critical zero-day vulnerability in Palo Alto Networks’ PAN-OS software, used in its GlobalProtect gateways, is being exploited in the wild,...
CISA’s Malware Analysis Platform Could Foster Better Threat Intel – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Bits And Splits via Shutterstock The US Cybersecurity and Infrastructure Security Agency (CISA) has given organizations a...