Source: www.bitdefender.com – Author: Graham Cluley The UK’s Leicester City Council was thrown into chaos last month when a crippling cyber attack forced it to shut...
Day: April 30, 2024
Ransomware Rising Despite Takedowns, Says Corvus Report – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 New ransomware gangs have already filled the void left by LockBit and ALPHV/BlackCat in the first quarter of 2024, according to...
YMCA Fined for Data Breach, ICO Raises Concerns About Privacy for People with HIV – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Information Commissioner’s Office (ICO) has called for stronger protections for people living with HIV who are being denied “basic dignity...
Millions of Malicious Containers Found on Docker Hub – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Three large-scale malware campaigns have infiltrated Docker Hub, deploying millions of malicious “imageless” containers. The data comes from JFrog’s security research team,...
Disinformation: EU Opens Probe Against Facebook and Instagram Ahead of Election – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Meta is under scrutiny for failing to tackle disinformation on its social media platforms. The EU Commission opened a probe on...
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an...
Managed Detection and Response in 2023 – Source: securelist.com
Source: securelist.com – Author: Kaspersky Security Services Managed Detection and Response in 2023 (PDF) Alongside other security solutions, we provide Kaspersky Managed Detection and Response (MDR)...
3 Ways File Integrity Monitoring Identifies Zero-Day Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lauren Yacono A zero-day attack leaves your software vulnerable to being exploited by hackers. It is a serious security risk. Cybercriminals are...
SSH vs. SSL/TLS: What’s The Difference? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Krupa Patil SSH and SSL/TLS are two widely used cryptographic protocols for establishing secure connections and ensuring secure communication between two parties...
LockBit, RAGroup Drive Ransomware Attacks in March – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Global ransomware attacks rose slightly in March compared to the previous month, as ransomware cabal RAGroup ramped up activity by...
Multiple Apache HTTP Server Vulnerabilities Fixed in Ubuntu – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina The Ubuntu security team recently addressed several Apache HTTP Server vulnerabilities in Ubuntu 23.10, Ubuntu 23.04, Ubuntu 22.04 LTS, Ubuntu...
Preparing for Holiday Cyberattacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nik Hewitt How can security teams be ready for holiday cyberattacks and a seasonal peak in cybercrime? Holiday cyberattacks are on the...
Debian 12: Redefining Stability and Innovation in Open-Source Operating Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anca Trusca Debian holds a distinguished position. Recognized as one of the oldest and most trusted distributions within the Linux ecosystem, Debian...
KapeKa Backdoor: Russian Threat Actor Group’s Recent Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja In the realm of cybersecurity, vigilance is paramount. Recent discoveries have shed light on a previously undisclosed threat known as...
Ensuring RBI Compliance: Crucial Cybersecurity Measures to Protect Financial Standing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover The rise of digital technology has provided great convenience to the banking sector, but it has also opened up the...
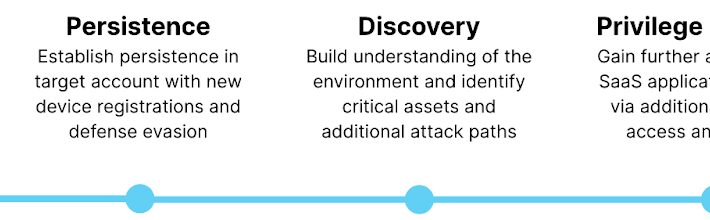
MITRE ATT&CK v15: A Deeper Dive into SaaS Identity Compromise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Farah Iyer The MITRE ATT&CK framework is a continually evolving resource, tracking the tactics, techniques, and procedures (TTPs) employed by adversaries across...
No more 12345: devices with weak passwords to be banned in UK – Source: www.theguardian.com
Source: www.theguardian.com – Author: Guardian staff and agency Tech that comes with weak passwords such as “admin” or “12345” will be banned in the UK under...
Change the law on computer evidence with an amendment to data protection bill | Letter – Source: www.theguardian.com
Source: www.theguardian.com – Author: Guardian Staff It is now clear that the Post Office was advised by its lawyers to delay disclosing some evidence that would...
Whale Song Code – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Whale Song Code During the Cold War, the US Navy tried to make a secret code out of whale song....
Friday Squid Blogging: Searching for the Colossal Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Searching for the Colossal Squid A cruise ship is searching for the colossal squid. As usual,...
Long Article on GM Spying on Its Cars’ Drivers – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments L-A-R-A • April 26, 2024 11:49 AM noname, be sure to read GM’s statements carefully. They said they’d...
The Rise of Large-Language-Model Optimization – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The web has become so interwoven with everyday life that it is easy to forget what an extraordinary accomplishment and...
Dan Solove on Privacy Regulation – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Law professor Dan Solove has a new article on privacy regulation. In his email to me, he writes: “I’ve been...
Microsoft and Security Incentives – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Former senior White House cyber policy director A. J. Grotto talks about the economic incentives for companies to improve their...
Using Legitimate GitHub URLs for Malware – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting social-engineering attack vector: McAfee released a report on a new LUA malware loader distributed through what appeared to be...
FCC Fines US Cell Carriers $200M for Selling Location Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance Commission Approves Long-Anticipated Fines for Verizon, T-Mobile, AT&T and Sprint...
Live Webinar | Protecting Your AI: Strategies for Securing AI Systems – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Shan Rao Group Product Manager, Google Cloud Shan Rao leads Google’s AI Security and Privacy initiatives as the Group Product Manager....
Harnessing AI: A Step-by-Step Guide for Job Seekers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Recruitment & Reskilling Strategy How ChatGPT Can Help You...
Career Spotlight: Growing Need for Technology Legal Analysts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Legislation & Litigation , Professional Certifications & Continuous Training High Demand for Experts Who Know Law Plus AI,...
Benefits of a Unified CNAPP and XDR Platform – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 More companies and their CISOs are embracing hybrid and cloud-native infrastructure. There are two drivers for this, according to Ganesh Pai,...