Source: securityboulevard.com – Author: Scott Kannry One could argue that the World’s greatest conquests, competitions, and challenges are better off when in the hands of a...
Day: April 18, 2024
XZ Utils-Like Takeover Attempt Targets the OpenJS Foundation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The OpenJS Foundation, which oversees multiple JavaScript projects, thwarted a takeover attempt of at least one project that has echoes...
USENIX Security ’23 – The Maginot Line: Attacking The Boundary Of DNS Caching Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: *Xiang Li, Chaoyi Lu, Baojun Liu, Qifan Zhang, Zhou Li, Haixin Duan, Qi Li* Many thanks to USENIX for...
What it takes to do Cloud Detection & Response – Source: securityboulevard.com
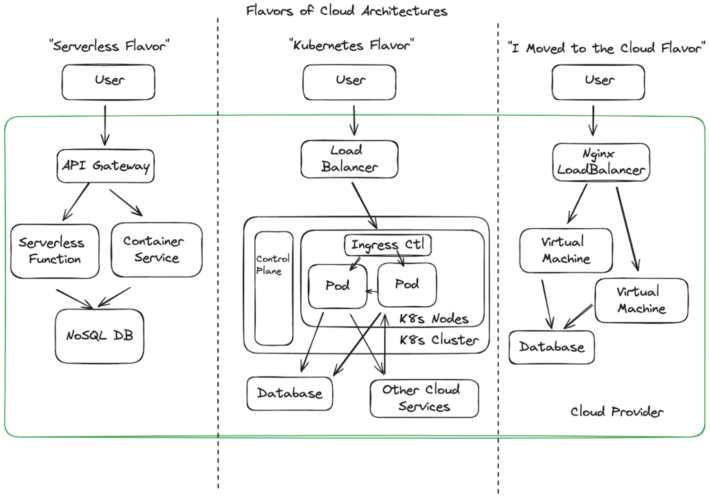
Source: securityboulevard.com – Author: James Berthoty A guest post by James Berthoty the founder of Latio Tech. The shift to cloud has meant an explosion in...
Understanding AWS End of Service Life Is a Key FinOps Responsibility – Source: securityboulevard.com
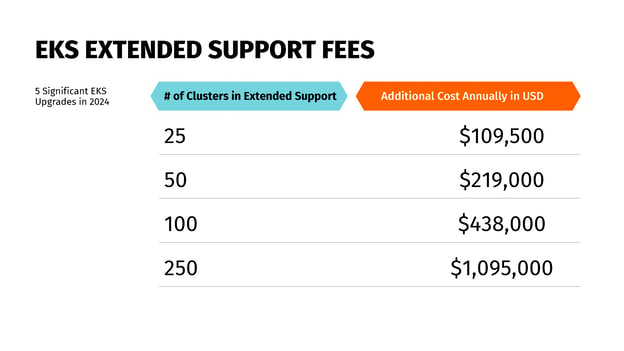
Source: securityboulevard.com – Author: Mary Henry Amazon Web Services (AWS) announced extended support prices for Amazon Elastic Kubernetes Service (EKS), prompting some businesses to reevaluate how...
Glitter and… Firewalls? How to stay safe this festival season – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog The air is electric, the skies are clear, and the lineups are out – festival season is upon us! From...
The Unseen Powerhouse: Demystifying Authentication Infrastructure for Tech Leaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author In today’s hyper-connected world, authentication is the digital gatekeeper that protects our identities, data, and...
EU Data Regulator Threatens Meta’s ‘Pay or Okay’ Model – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy The European Data Protection Board Says the Company Inhibits...
How to Start a Career in Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Training & Security Leadership A Guide to Seizing Opportunities and Pursuing Growth Steve King • April 17, 2024 Image:...
Possible Chinese Hackers Use OpenMetadata to Cryptomine – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Cryptocurrency Fraud , Fraud Management & Cybercrime Hackers Target OpenMetadata Platforms Running on Cloud Kubernetes Environments Prajeet Nair...
Hack on Clinic Serving Homeless Is Latest Hit to Underserved – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Centers for Underserved Patients, Resource-Poor Communities Fight for Cyber Funds Marianne Kolbasuk...
Armis Buys Cyber Remediation Startup Silk Security for $150M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Combination of Armis and Silk Will Create Leader in Asset...
Redgate Launches Enterprise Edition of Redgate Monitor – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE CAMBRIDGE, April 17, 2024 – Redgate, the end-to-end Database DevOps provider, has launched an enterprise version of its popular database...
Dangerous ICS Malware Targets Orgs in Russia and Ukraine – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Andrew Angelov via Shutterstock Two dangerous malware tools targeted at industrial control systems (ICS) and operating technology...
Active Kubernetes RCE Attack Relies on Known OpenMetadata Vulns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading 1 Min Read Source: Sergey Novikov via Alamy Stock Photo Known vulnerabilities in OpenMetadata’s open source...
Ivanti Releases Fixes for More Than 2 Dozen Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Alexander Tolstykh via Shutterstock Ivanti has released 27 fixes for various reported vulnerabilities in its...
Various Botnets Pummel Year-Old TP-Link Flaw in IoT Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Stuart Miles via Alamy Stock Photo A number of botnets are pummeling a nearly year-old command-injection vulnerability...
Preparing for Cyber Warfare: 6 Key Lessons From Ukraine – Source: www.darkreading.com
Source: www.darkreading.com – Author: Hadi Shavarini 3 Min Read Source: Aleksei Gorodenkov via Alamy Stock Photo COMMENTARY As the conflict in Ukraine enters its third year,...
Enterprise Endpoints Aren’t Ready for AI – Source: www.darkreading.com
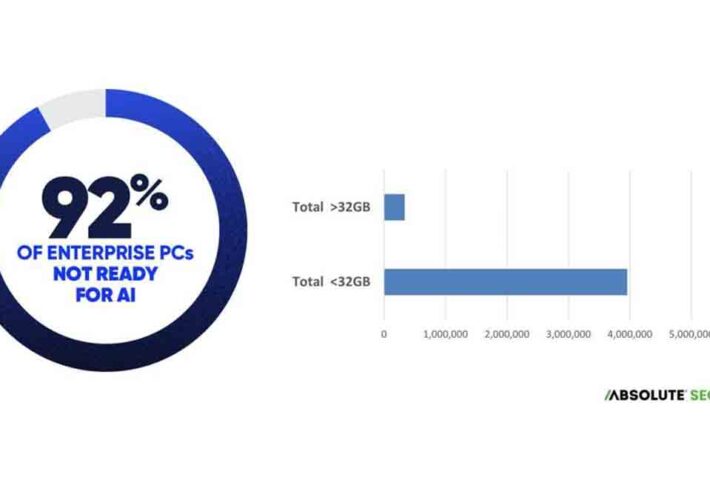
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: Absolute Security Cyber Resilience Risk Index 2024 Enterprises assessing their readiness for artificial intelligence (AI)...
3 Steps Executives and Boards Should Take to Ensure Cyber Readiness – Source: www.darkreading.com
Source: www.darkreading.com – Author: Chris Crummey Chris Crummey, Director, Executive & Board Cyber Services, Sygnia April 16, 2024 5 Min Read Source: Yee Xin Tan via...
LockBit 3.0 Variant Generates Custom, Self-Propagating Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Zoonar Gmbh via Alamy Stock Photo The LockBit ransomware-as-a-service (RaaS) group has struck another victim, this time...
FBI: Smishing Campaign Lures Victims With Unpaid-Toll Notices – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Mira via Alamy Stock Photo The FBI is warning people about widespread SMS phishing (smishing) campaign spreading...
Is a VPN Really Worth It in 2024? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Yes, virtual private networks are worth it. In today’s digital age, it’s become increasingly important to protect online data. In...
Conversational Server Access Security
The document titled “Conversational Server Access Security” by Derek A. Smith addresses the evolving landscape of cybersecurity threats, particularly focusing on protecting server access in on-premises...