Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Day: April 13, 2024
UK Markets Authority Warns of AI Market Capture by Big Tech – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development CMA Says Market Is Becoming more Verticially Integrated Akshaya Asokan...
PE Firm Accuses Synopsys of Breaching Exclusivity Agreement – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Governance & Risk Management , Next-Generation Technologies & Secure Development Sunstone Partners: We Had a Letter of Intent...
Cloned Voice Tech Is Coming for Bank Accounts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Fraud Management & Cybercrime , ID Fraud Experts Warn AI Tools Can Now Compromise Voice...
US Cyber Command Expanded ‘Hunt Forward’ Operations in 2023 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Government US Cyber Mission Force Led 22 Defensive Cyber Operations in...
Safeguarding America’s Future: Mitigating the Implications of Chinese Control Over U.S. Critical Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary by Lena Allen Introduction In this era of unprecedented technological interconnectedness, the safeguarding of critical infrastructure against cyber threats has ascended...
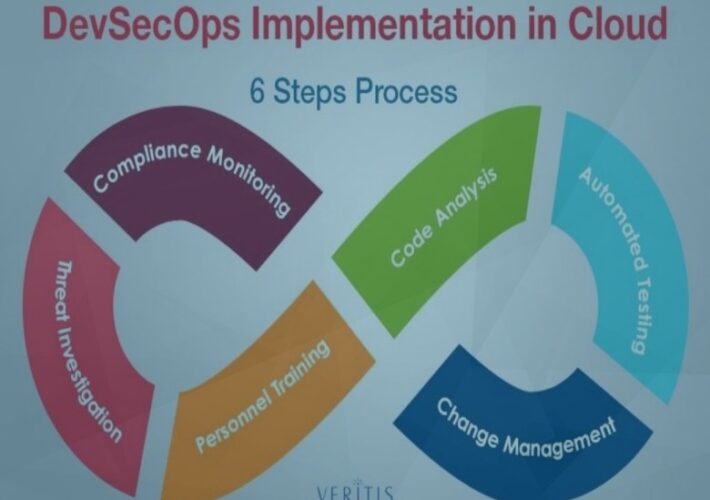
DevSecOps Practices for a Secure Cloud – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin How to start ahead of the curve? By Vishakha Sadhwani, Customer Engineer, Google Cloud In today’s rapidly evolving technological landscape, a...
Vendors Beware of the Cybersecurity Audit – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Caroline McCaffery, Co-Founder and CEO of ClearOPS Introduction to Vendor Management Why does every license agreement and data protection addendum,...
How to protect company data in the gig economy – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Zac Amos, Features Editor, Rehack.com. Hiring gig workers and freelancers has a lot of business benefits, allowing companies to utilize the contractors’...
How artificial intelligence is revolutionizing cyber security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: gmack By Shira Landau, Editor-in-Chief, CyberTalk.org. In recent years, artificial intelligence (AI) has become one of the most sure-fire and strategic tools...
Nmap for Pentester – PORT STATE
The document discusses the different states of ports that Nmap recognizes during network scanning, including Open, Closed, Filtered, Unfiltered, Open|Filtered, and Closed|Filtered ports. It provides details...