Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Tada Images via Shutterstock Docker has removed nearly 3 million public repositories from Docker Hub after researchers...
Month: April 2024
Canadian Drug Chain in Temporary Lockdown Mode After Cyber Incident – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: ton koene via Alamy Stock Photo London Drugs, a Canadian pharmacy chain, has closed its...
To Damage OT Systems, Hackers Tap USBs, Old Bugs & Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Mohammad Aaref Barahouei via Alamy Stock Photo Industrial cyberattackers are increasingly using removable media to penetrate operational...
Wireless Carriers Face $200M FCC Fine As Data Privacy Waters Roil – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Wavebreak Media ltd via Alamy Stock Photo The Federal Communications Commission (FCC) has fined the top US...
The 6 Data Security Sessions You Shouldn’t Miss at RSAC 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Liat Hayun Liat Hayun, Co-Founder & CEO, Eureka Security April 30, 2024 3 Min Read Source: Aleksandr Matveev via Alamy Stock Photo...
New Research Suggests Africa Is Being Used As a ‘Testing Ground’ for Nation State Cyber Warfare – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE London, UK. 24th April 2024: Performanta, the multinational cybersecurity firm specialising in helping companies move beyond security to achieve cyber safety, has...
MITRE’s Cyber Resiliency Engineering Framework Aligns With DoD Cyber Maturity Model Cert – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE McLean, Va. & Bedford, Mass., April 25, 2024 — MITRE’s Cyber Resiliency Engineering Framework (CREF) NavigatorTM now incorporates the US...
How AI can benefit zero trust – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The zero trust framework is a cornerstone of modern cyber security threat prevention and defense architectures. At its core,...
Say goodbye to standard security for smartphones (you need this instead) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Zahier Madhar, Lead Security Engineer and Office of the CTO, Check Point. Smartphones play a pivotal role in all of...
Ransomware attack causes city street lights to “misbehave” – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In England, Leicester City is experiencing persistent problems with its street light system due to a recent cyber attack....
The evolution from BEC to BCC – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau David Meister is a valued technology expert with over 15 years of experience in technical and consultancy roles across a range...
Top 10 things CISOs should know about AI security tools – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: As reported by executives, the top tangible benefit of AI is cyber security and risk management optimization. Right now,...
Secure out-of-band console and power management for Check Point security gateways – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Contributed by WTI as part of Check Point’s CPX silver-level partner sponsorship opportunity. WTI is an industry leader in out-of-band network...
The MSSP perspective: CISO insights into stronger security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Gary Landau has been leading IT and information security teams for over 25 years as part of startups as well as...
News alert: Cybersixgill unveils ‘Third-Party Intelligence’ to deliver vendor-specific threat intel – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel – April 30, 2024 – Cybersixgill, the global cyber threat intelligence data provider, broke new ground today by introducing its Third-Party Intelligence module....
GUEST ESSAY: Recalibrating critical infrastructure security in the wake of evolving threats – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Joseph Bell For all the discussion around the sophisticated technology, strategies, and tactics hackers use to infiltrate networks, sometimes the...
RSAC Fireside Chat: Secure, flexible web browsers finally available, thanks to open-source code – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido At the end of 2000, I was hired by USA Today to cover Microsoft, which at the...
“Junk gun” ransomware: the cheap new threat to small businesses – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley What’s going on? A wave of cheap, crude, amateurish ransomware has been spotted on the dark web – and although...
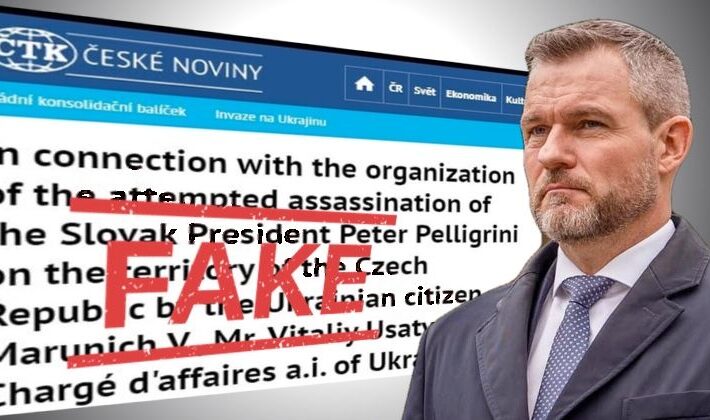
Hacker posts fake news story about Ukrainians trying to kill Slovak President – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Czech news agency ČTK announced on Tuesday that a hacker had managed to break into its systems and published fake...
Smashing Security podcast #369: Keeping the lights on after a ransomware attack – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Leicester City Council suffers a crippling ransomware attack, and a massive data breach, but is it out of the dark...
City street lights “misbehave” after ransomware attack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The UK’s Leicester City Council was thrown into chaos last month when a crippling cyber attack forced it to shut...
Ransomware Rising Despite Takedowns, Says Corvus Report – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 New ransomware gangs have already filled the void left by LockBit and ALPHV/BlackCat in the first quarter of 2024, according to...
YMCA Fined for Data Breach, ICO Raises Concerns About Privacy for People with HIV – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Information Commissioner’s Office (ICO) has called for stronger protections for people living with HIV who are being denied “basic dignity...
Millions of Malicious Containers Found on Docker Hub – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Three large-scale malware campaigns have infiltrated Docker Hub, deploying millions of malicious “imageless” containers. The data comes from JFrog’s security research team,...
Disinformation: EU Opens Probe Against Facebook and Instagram Ahead of Election – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Meta is under scrutiny for failing to tackle disinformation on its social media platforms. The EU Commission opened a probe on...
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an...
Managed Detection and Response in 2023 – Source: securelist.com
Source: securelist.com – Author: Kaspersky Security Services Managed Detection and Response in 2023 (PDF) Alongside other security solutions, we provide Kaspersky Managed Detection and Response (MDR)...
3 Ways File Integrity Monitoring Identifies Zero-Day Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lauren Yacono A zero-day attack leaves your software vulnerable to being exploited by hackers. It is a serious security risk. Cybercriminals are...
SSH vs. SSL/TLS: What’s The Difference? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Krupa Patil SSH and SSL/TLS are two widely used cryptographic protocols for establishing secure connections and ensuring secure communication between two parties...
LockBit, RAGroup Drive Ransomware Attacks in March – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Global ransomware attacks rose slightly in March compared to the previous month, as ransomware cabal RAGroup ramped up activity by...