Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Data loss is a difficult business reality. Depending on the circumstances, data loss can even force businesses to shut...
Day: March 30, 2024
Activision: Enable 2FA to secure accounts recently stolen by malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An infostealer malware campaign has collected millions of logins from users of various gaming websites, including players that use cheats,...
Are You Affected by the Backdoor in XZ Utils? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: MSRF via Alamy Stock Photo Red Hat is warning that a vulnerability in XZ Utils,...
CISO Corner: Cyber-Pro Swindle; New Faces of Risk; Cyber Boosts Valuation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Universal Images Group North America LLC via Alamy Stock Photo Welcome to CISO Corner,...
UN Peace Operations Under Fire From State-Sponsored Hackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading 1 Min Read Source: Photonic via Alamy Stock Photo United Nations peacekeeping missions, especially in Africa,...
Lessons From the LockBit Takedown – Source: www.darkreading.com
Source: www.darkreading.com – Author: Aaron Walton 4 Min Read Source: Aleksei Gorodenkov via Alamy Stock Photo Like most operators out there, we really enjoyed last month’s...
Cloud Email Filtering Bypass Attack Works 80% of the Time – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Strom 5 Min Read Source: Cultura Creative RF via Alamy Stock Photo Computer scientists have uncovered a shockingly prevalent misconfiguration in...
TheMoon Malware Rises Again with Malicious Botnet for Hire – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Design Pics Inc via Alamy Stock Photo After disappearing for several years, TheMoon has returned...
Checkmarx Announces Partnership With Wiz – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE PARAMUS, N.J.–(BUSINESS WIRE)– Checkmarx, the leader in cloud-native application security, has integrated its enterprise application security platform, Checkmarx One, with...
WiCyS and ISC2 Launch Spring Camp for Cybersecurity Certification – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE COOKEVILLE, Tenn., March 26, 2024/PRNewswire-PRWeb/ — In partnership with ISC2, the world’s leading nonprofit member organization for cybersecurity professionals, Women...
New Cyber Threats to Challenge Financial Services Sector in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE RESTON, Va., March 27, 2024 /PRNewswire/ — FS-ISAC, the member-driven, not-for-profit organization that advances cybersecurity and resilience in the global...
Getting rid of a 20+ year old known vulnerability: It’s like a PSA for Runtime Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lisa Vaas, Senior Content Marketing Manager, Contrast Security On Wednesday, March 27, CISA and the FBI issued a cry for help: We...
‘Darcula’ PhaaS Campaign Sinks Fangs into Victims – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A sprawling phishing-as-a-service (PhaaS) campaign that has been running since at least last summer is using more than 20,000 fake...
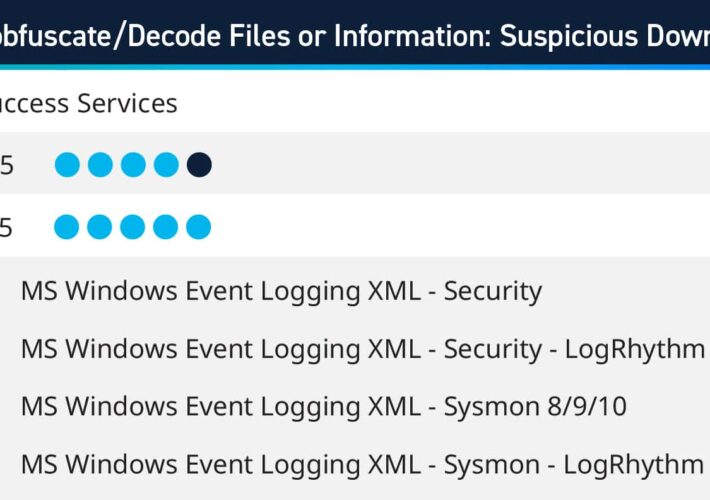
Q1 2024 Success Services Use Cases – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast As part of the Subscription Services team, LogRhythm consultants work with customers to help bolster their defenses against cyberthreats and...
Strengthening Security in Distributed Payment Systems: Exploring Innovative Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nak Koh Building on our previous discussion about the pivotal role of Trusted Platform Modules (TPMs) in securing distributed ID and payment...
Market Forces vs. Regulation: How to Drive IT Product Safety – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Over the past 50 years, traveling in automobiles has become much safer. Part of this is due to government regulations...
Implications of AI for Corporate Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ontic Contributor Article By: Ontic Contributor | March 29, 2024 On February 29, I was honored to serve as the moderator for...
Guarding Education: The Impact of Compromised Credentials – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic In recent years, the education sector has increasingly become a target for cybercriminals seeking to exploit vulnerabilities and gain unauthorized access...
PyPI Goes Quiet After Huge Malware Attack: 500+ Typosquat Fakes Found – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings The Python Package Index was drowning in malicious code again, so they had to shut down registration for cleanup. More software supply-chain...
A(nother) Ransomware Saga with a Twist – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joao Correia The healthcare sector has once again found itself at the center of a storm. On February 21, Change Healthcare, a...
10 Must-Have Elements for an Air-Tight IT Security Policy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rom Carmel In 2023, data security faced an uphill battle against cyberattacks, and the risks of becoming a victim grew stronger. There...
DHS Calls Political Campaigns ‘Ripe Target’ for Cyberattacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Government Foreign Adversaries Increasingly See Campaigns as Prime for Hacking, Official...
Is It Generative AI’s Fault, or Do We Blame Human Beings? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 AI is on the way to embedding itself in our daily lives. If you feel threatened by artificial intelligence, Sam Curry...
ShadowRay Attack Strikes AI Workloads – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Thousands of AI Workloads Compromised Amid CVE Vulnerability Dispute Prajeet...
Feds Warn of Credential Harvesting Threats in Healthcare – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Anti-Phishing, DMARC , Fraud Management & Cybercrime , Social Engineering HHS Says Tried-and-True Hacker Methods Can Compromise Patient Data, Safety Marianne...
Malware Flood Causes PyPI to Temporarily Halt New Accounts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Security Operations Hackers Are Now Using Code Repositories as Malware Vectors Mihir Bagwe (MihirBagwe) • March 29, 2024 Python...
On Point: The New Impersonation-Social Engineering Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development How AI and Deepfakes Make...
Manufacturing on the Cyber Frontlines: Enhancing Cybersecurity on the Factory Floor – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Berardino Baratta, CEO, MxD Manufacturing in the United States is changing. Today’s factory floors are a far cry from...
Making Our Infrastructure Resilient: 5 Priorities for Security R&D – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Saurabh Amin, Professor of Civil and Environmental Engineering PI, Laboratory for Information and Decision Systems Massachusetts Institute of Technology...
Key Differences in Securing OT & IT Environments – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Critical cybersecurity components every security leader must know amid the convergence of IT & OT By Joe O’Donnell, EVP of...