Source: krebsonsecurity.com – Author: BrianKrebs Thread hijacking attacks. They happen when someone you know has their email account compromised, and you are suddenly dropped into an...
Day: March 28, 2024
Recent ‘MFA Bombing’ Attacks Targeting Apple Users – Source: krebsonsecurity.com
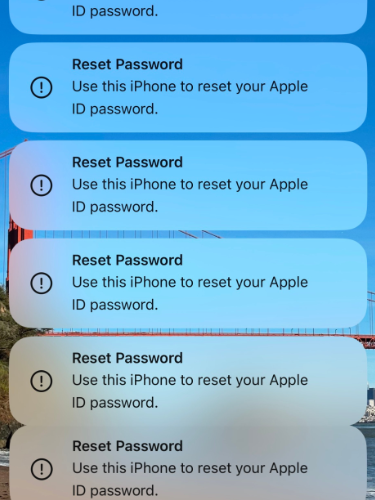
Source: krebsonsecurity.com – Author: BrianKrebs Several Apple customers recently reported being targeted in elaborate phishing attacks that involve what appears to be a bug in Apple’s...
Mozilla Drops Onerep After CEO Admits to Running People-Search Networks – Source: krebsonsecurity.com
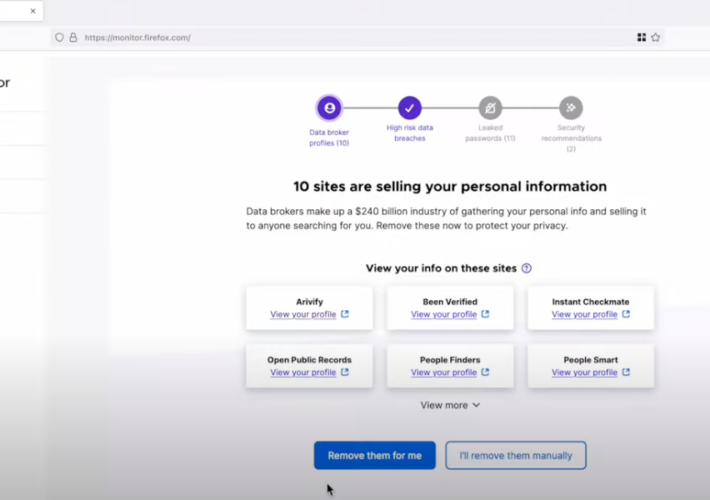
Source: krebsonsecurity.com – Author: BrianKrebs The nonprofit organization that supports the Firefox web browser said today it is winding down its new partnership with Onerep, an...
The Not-so-True People-Search Network from China – Source: krebsonsecurity.com
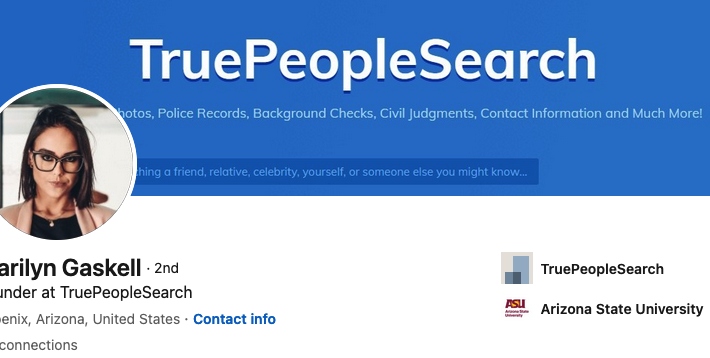
Source: krebsonsecurity.com – Author: BrianKrebs It’s not unusual for the data brokers behind people-search websites to use pseudonyms in their day-to-day lives (you would, too). Some...
DinodasRAT Linux implant targeting entities worldwide – Source: securelist.com
Source: securelist.com – Author: Anderson Leite, Lisandro Ubiedo DinodasRAT, also known as XDealer, is a multi-platform backdoor written in C++ that offers a range of capabilities....
Android malware, Android malware and more Android malware – Source: securelist.com
Source: securelist.com – Author: GReAT Introduction Malware for mobile devices is something we come across very often. In 2023, our technologies blocked 33.8 million malware, adware,...
Threat landscape for industrial automation systems. H2 2023 – Source: securelist.com
Source: securelist.com – Author: Kaspersky ICS CERT Industrial threats Industrial threats 19 Mar 2024 minute read Global statistics across all threats In the second half of...
A patched Windows attack surface is still exploitable – Source: securelist.com
Source: securelist.com – Author: Elsayed Elrefaei, Ashraf Refaat, Kaspersky GERT On August 8, 2023, Microsoft finally released a kernel patch for a class of vulnerabilities affecting Microsoft...
What’s in your notepad? Infected text editors target Chinese users – Source: securelist.com
Source: securelist.com – Author: Sergey Puzan “Malvertising” is a popular way of attracting victims to malicious sites: an advertisement block is placed at the top of...
The State of Stalkerware in 2023–2024 – Source: securelist.com
Source: securelist.com – Author: Kaspersky The State of Stalkerware in 2023 (PDF) The annual Kaspersky State of Stalkerware report aims to contribute to awareness and a...
Top 10 web application vulnerabilities in 2021–2023 – Source: securelist.com
Source: securelist.com – Author: Oxana Andreeva, Kaspersky Security Services To help companies with navigating the world of web application vulnerabilities and securing their own web applications,...
Spam and phishing in 2023 – Source: securelist.com
Source: securelist.com – Author: Tatyana Kulikova, Olga Svistunova, Andrey Kovtun, Irina Shimko, Roman Dedenok The year in figures 45.60% of all email sent worldwide and 46.59%...
Network tunneling with… QEMU? – Source: securelist.com
Source: securelist.com – Author: Grigory Sablin, Alexander Rodchenko, Kirill Magaskin Cyberattackers tend to give preference to legitimate tools when taking various attack steps, as these help...
An educational robot security research – Source: securelist.com
Source: securelist.com – Author: Nikolay Frolov In the modern world, we are surrounded by a multitude of smart devices that simplify our daily lives: smart speakers,...
Decade-old Linux ‘wall’ bug helps make fake SUDO prompts, steal passwords – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A vulnerability in the wall command of the util-linux package that is part of the Linux operating system could allow an unprivileged...
Retail chain Hot Topic hit by new credential stuffing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan American retailer Hot Topic disclosed that two waves of credential stuffing attacks in November exposed affected customers’ personal information and...
PyPI suspends new user registration to block malware campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Python Package Index (PyPI) has temporarily suspended user registration and the creation of new projects to deal with an...
Cisco warns of password-spraying attacks targeting VPN services – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cisco has shared a set of recommendations for customers to mitigate password-spraying attacks that have been targeting Remote Access VPN...
How Pentesting-as-a-Service can Reduce Overall Security Costs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 If your job involves keeping applications or data secure, you know how important penetration testing can be in identifying...
Windows 11 22H2 Home and Pro get preview updates until June 26 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft reminded customers today that the Windows 11 22H2 Home and Pro editions will continue to receive non-security preview updates...
Google fixes Chrome zero-days exploited at Pwn2Own 2024 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google fixed seven security vulnerabilities in the Chrome web browser on Tuesday, including two zero-days exploited during the Pwn2Own Vancouver...
INC Ransom threatens to leak 3TB of NHS Scotland stolen data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The INC Ransom extortion gang is threatening to publish three terabytes of data allegedly stolen after breaching the National Health Service...
CISA tags Microsoft SharePoint RCE bug as actively exploited – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA warns that attackers are now exploiting a Microsoft SharePoint code injection vulnerability that can be chained with a critical privilege...
KuCoin charged with AML violations that let cybercriminals launder billions – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The U.S. Department of Justice (DoJ) has charged global cryptocurrency exchange KuCoin and two of its founders for failing to...
Cisco IOS Bugs Allow Unauthenticated, Remote DoS Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading 1 Min Read Source: MTP via Alamy Stock Photo Cisco has released security updates for its...
Pervasive LLM Hallucinations Expand Code Developer Attack Surface – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Deemerwha studio via Shutterstock Software developers’ use of large language models (LLMs) among software developers presents a...
Indian Government, Oil Companies Breached by ‘HackBrowserData’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: ADragan via Shutterstock India’s government agencies and energy companies are facing a new threat in...
Suspected MFA Bombing Attacks Target Apple iPhone Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Elizabeth Montalbano, Contributing Writer Source: Arcansel via Shutterstock Attackers are targeting Apple iPhone users with a rash of...
US Puts Up $10M Bounty on BlackCat Ransomware Gang Members – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: B Christopher via Alamy Stock Photo The US Department of State has announced it’s putting...
Protect Your Business With This Seamless Firewall — Now $150 Off – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published March 27, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...