Source: www.schneier.com – Author: Bruce Schneier Paleontologists have discovered a 183-million-year-old species of vampire squid. Prior research suggests that the vampyromorph lived in the shallows off...
Day: March 2, 2024
NIST Cybersecurity Framework 2.0 – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier NIST has released version 2.0 of the Cybersecurity Framework: The CSF 2.0, which supports implementation of the National Cybersecurity Strategy,...
How the “Frontier” Became the Slogan of Uncontrolled AI – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier Artificial intelligence (AI) has been billed as the next frontier of humanity: the newly available expanse whose exploration will drive...
News farm impersonates 60+ major outlets: BBC, CNN, CNBC, Guardian… – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma BleepingComputer has discovered a content farm operating some 60+ domains named after popular media outlets, including the BBC, CNBC, CNN,...
Hackers target FCC, crypto firms in advanced Okta phishing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new phishing kit named CryptoChameleon is being used to target Federal Communications Commission (FCC) employees, using specially crafted single sign-on...
Windows Kernel bug fixed last month exploited as zero-day since August – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft patched a high-severity Windows Kernel privilege escalation vulnerability in February, six months after being informed that the flaw was...
CISA warns of Microsoft Streaming bug exploited in malware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA ordered U.S. Federal Civilian Executive Branch (FCEB) agencies to secure their Windows systems against a high-severity vulnerability in the...
Germany takes down cybercrime market with over 180,000 users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Düsseldorf Police in Germany have seized Crimemarket, a massive German-speaking illicit trading platform with over 180,000 users, arresting six...
Microsoft fixes Outlook clients not syncing over Exchange ActiveSync – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has fixed an issue causing some Microsoft 365 users’ Outlook desktop clients to stop connecting to email servers via...
Microsoft pulls Edge update causing ‘Out of Memory’ crashes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has pulled the Microsoft Edge 122.0.2365.63 update after users reported receiving “Out of memory” errors when browsing the web...
U.S. charges Iranian for hacks on defense orgs, offers $10M for info – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The U.S. Department of Justice (DoJ) has unveiled an indictment against Alireza Shafie Nasab, a 39-year-old Iranian national, for his...
CISO Corner: Operationalizing NIST CSF 2.0; AI Models Run Amok – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Welcome to CISO Corner, Dark Reading’s weekly digest of articles tailored specifically to security operations...
It’s 10 p.m. Do You Know Where Your AI Models Are Tonight? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer Source: Kirsty Pargeter via Alamy Stock Photo If you thought the software supply chain security problem was difficult...
A Deep Dive into the 2024 Prudential and LoanDepot Breaches – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Financial Giants Under Siege It’s only the first quarter of 2024 and major breaches are already starting to be announced, with...
SafeBreach Coverage for AA24-060A (Phobos Ransomware) and AA24-060B (Ivanti Connect Secure) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On February 29th, the Cybersecurity and Infrastructure Security Agency (CISA) issued two separate...
Response to CISA Advisory (AA24-060A): #StopRansomware: Phobos Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Francis Guibernau On February 29, 2024, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State...
USENIX Security ’23 – Vivek Nair, Dawn Song – Multi-Factor Key Derivation Function (MFKDF) for Fast, Flexible, Secure, & Practical Key Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Vivek Nair, Dawn Song – Multi-Factor Key...
CISA, Mandiant Warn of a Worsening Situation for Ivanti Users – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The federal government and cybersecurity teams are warning organizations that threat groups are exploiting multiple flaws in Ivanti’s VPN appliances...
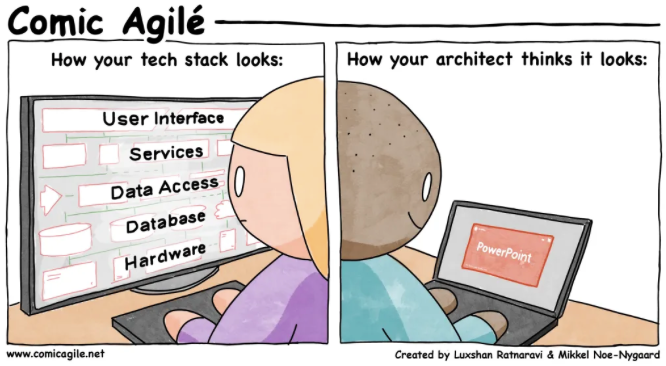
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #280 – The Tech Stack and the Architect – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics USENIX Security ’23 – Vivek Nair, Dawn Song – Multi-Factor Key Derivation Function (MFKDF) for Fast, Flexible, Secure,...
How to secure your API secret keys from being exposed? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova The uncontrolled sprawl of exposed, insecure APIs puts sensitive personal and corporate data at high risk, as shown by the...
Cheap Video Doorbell Cams: Tools of Stalkers and Thieves – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Amazon, Sears and Shein still sell security swerving stuff. Cheap Chinese doorbell cameras aren’t always super-secure, say researchers. I know, I...
What is a Shadow API? Understanding the risks and strategies to prevent their sprawl – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova API Sprawl is a serious challenge in 2024, and shadow APIs are part of the problem. But do you actually...
USENIX Security ’23 – Conor Gilsenan, Fuzail Shakir, Noura Alomar, Serge Egelman – Security and Privacy Failures in Popular 2FA Apps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Conor Gilsenan, Fuzail Shakir, Noura Alomar, Serge...
ISMG Editors: OpenAI’s Response to The New York Times Case – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Video Also: Addressing Scotland’s Cybercrime Surge; NOC and SOC...
Turning Defense Into Offense – Combating Phishing Attacks With Modern Authentication – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Stages of LockBit Grief: Anger, Denial, Faking Resurrection? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Is LockBit a Kremlin Sock Puppet? Mathew J. Schwartz (euroinfosec) • February 29, 2024 ...
Your Supply Chain Is Your New Attack Surface – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Organizations and their employees are using hundreds of SaaS applications every day, and these applications are decentralized and mostly ungoverned. They...
The Widespread Effect of the Change Healthcare Mega Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The Change Healthcare mega hack has taken nearly 120 of the company’s IT products and services offline since Feb. 21, and...
Ivanti Disputes CISA Findings of Post-Factory Reset Hacking – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Patch Management Gateway Maker Says Technique Won’t Succeed in Live Customer Environment Mihir...
Live Webinar | Proactive Protection: Mitigating Cyber Exposure with Actionable Insights – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Chris Poulin Director of Technology and Strategy and Deputy CTO, Bitsight Chris Poulin has over 35 years of experience in information...