Source: www.bleepingcomputer.com – Author: Lawrence Abrams Ransomware attacks on healthcare over the last few months have been relentless, with numerous ransomware operations targeting hospitals and medical...
Day: March 1, 2024
Taiwan’s Biggest Telco Breached by Suspected Chinese Hackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: BSTAR IMAGES via Alamy Stock Photo Taiwan’s Defense Ministry is urging Chunghwa Telecom, the the island’s largest telecom...
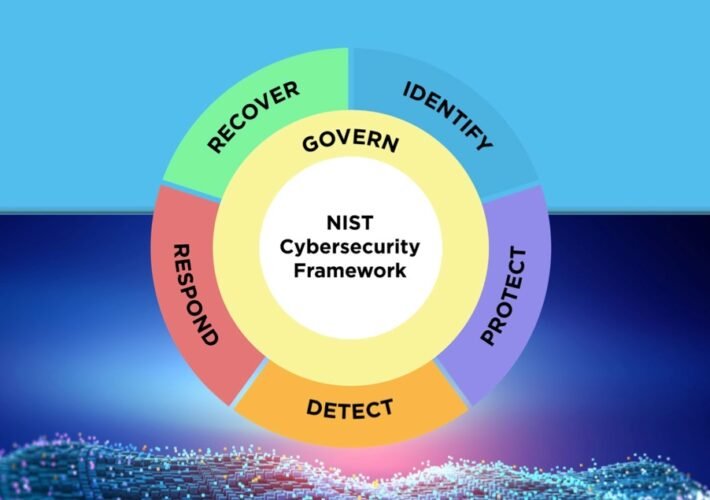
NIST Cybersecurity Framework 2.0: 4 Steps to Get Started – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: National Institute of Standards and Technology The US National Institute of Standards and Technology (NIST) has released...
CryptoChameleon Attackers Target Apple, Okta Users With Tech Support Gambit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo A phishing kit dubbed CryptoChameleon has been discovered...
Biometrics Regulation Heats Up, Portending Compliance Headaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Strom Source: Skorzewiak via Alamy Stock Photo This year might be a boon for biometric privacy legislation. The topic is heating...
Tips on Managing Diverse Security Teams – Source: www.darkreading.com
Source: www.darkreading.com – Author: Gourav Nagar Source: Sergey Pykhonin via Alamy Stock Vector COMMENTARY Long before I was a cybersecurity manager, I was an individual contributor....
Infrastructure Cyberattacks, AI-Powered Threats Pummel Africa – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: CG Alex via Shutterstock Most major economies in Africa experienced fewer overall cyber threats in 2023, but...
Hugging Face AI Platform Riddled With 100 Malicious Code-Execution Models – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: WrightStudio via Alamy Stock Photo Researchers have discovered about 100 machine learning (ML) models that have been...
MTTR: The Most Important Security Metric – Source: www.darkreading.com
Source: www.darkreading.com – Author: Harshil Parikh Source: Borka Kiss via Alamy Stock Photo COMMENTARY Reducing risk has long been the guiding principle for security teams. However,...
Ransomware-as-a-Service Spawns Wave of Cyberattacks in Middle East & Africa – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: Audrey Popov via Shutterstock Ransomware-as-a-service (RaaS) affiliates are fueling a huge surge in ransomware attacks in the...
Echoes of SolarWinds in New ‘Silver SAML’ Attack Technique – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: shaneinsweden via Shutterstock After the threat actor behind the SolarWinds attack compromised the company’s Orion network management...
Cyber Threat Assessment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh In the digital landscape, what you don’t know can hurt you. The unseen threats lurking in the shadows of your...
Zscaler CEO: Palo Alto Playing Defense as Firewall Sales Ebb – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Network Firewalls, Network Access Control , SASE Jay Chaudhry Says Palo Alto Offering Free Products to...
Dashlane Free vs. Premium: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
NordPass Free vs. Premium: Is It Worth the Upgrade? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Proton VPN Free vs. Premium: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
RoboForm Free vs. Paid: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Free VPN vs Paid VPN: Which One Is Right for You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Nicole Rennolds We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
TunnelBear VPN Free vs. Paid: Which Plan Is Right for You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
10 Must-Read Books on Cybersecurity – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: In a world fraught with cyberattacks and privacy violations in both business and individual spaces, cybersecurity remains a veritable tool for curtailing...
Privacy as an Enabler of Customer Trust
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Prepare for Zero Trust
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OT SECURITY
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Golden Corral restaurant chain data breach impacts 183,000 people – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Golden Corral American restaurant chain disclosed a data breach after attackers behind an August cyberattack stole the personal information...
New Bifrost malware for Linux mimics VMware domain for evasion – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new Linux variant of the Bifrost remote access trojan (RAT) employs several novel evasion techniques, including the use of...
Brave browser launches privacy-focused AI assistant on Android – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Brave Software is the next company to jump into AI, announcing a new privacy-preserving AI assistant called “Leo” is rolling...
CISA cautions against using hacked Ivanti VPN gateways even after factory resets – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed today that attackers who hack Ivanti VPN appliances using one of...
Windows 10 KB5034843 update released with 9 new changes, fixes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has released the optional KB5034843 Preview cumulative update for Windows 10 22H2 with an updated sharing experience and eight...
Windows 11 KB5034848 preview update adds USB 80Gbps support – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has released the optional KB5034848 Preview cumulative update for Windows 11 23H2 and 22H2, which brings new features, including...