The document provides essential information and guidance on identifying and handling phishing and sextortion scams, commonly used by cybercriminals to exploit individuals through deceptive emails. It...
Day: February 20, 2024
Introduction to Cybersecurity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
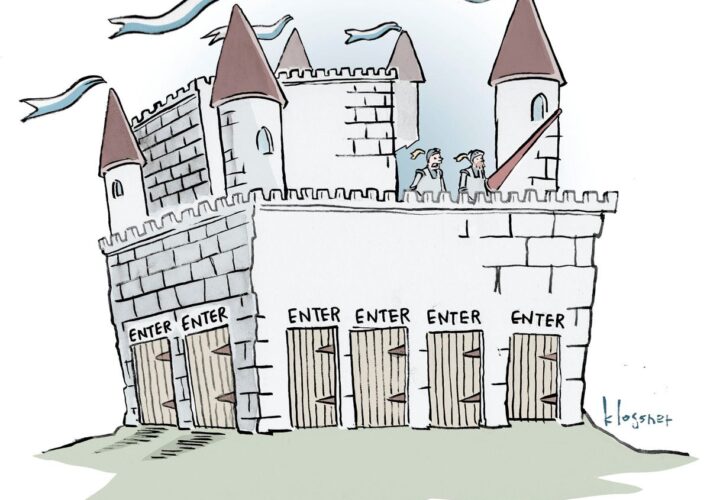
Name That Toon: Keys to the Kingdom – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist 1 Min Read Feeling a bit vulnerable lately? Come up with a clever cybersecurity-related caption to describe the scene...
NSO Group Adds ‘MMS Fingerprinting’ Zero-Click Attack to Spyware Arsenal – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: mundissima via Shutterstock A researcher at Swedish telecom and cybersecurity firm Enea has unearthed a previously unknown...
MoqHao Evolution Poses Immense Threat to Android Users – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja Cybersecurity threat experts have recently discovered a new variant of the malware named XLoader, commonly known as MoqHao, that has...
The Digital Services Act is Here. Nisos Can Help! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nisos Nisos The Digital Services Act is Here. Nisos Can Help! As of February 17, 2024, the European Union’s Digital Services Act...
Titanium and LogRhythm: Elevating Visibility into Cybersecurity Risks in Pakistan – Source: securityboulevard.com
Source: securityboulevard.com – Author: LogRhythm Titanium stands as the information security division of Pakistan’s leading ISP Cybernet. Established in 1996, Cybernet is a part of the...
NSO Group and Its ‘MMS Fingerprint’ Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Buried among the piles of legal documents that form WhatsApp’s five-year-old lawsuit against NSO Group is a line in a...
EU Court of Human Rights Rejects Encryption Backdoors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier The European Court of Human Rights has ruled that breaking end-to-end encryption by adding backdoors violates human rights: Seemingly most...
Automated remediation of exposed secrets: Pros and cons – Source: securityboulevard.com
Source: securityboulevard.com – Author: Itzik Alvas. Co-founder & CEO, Entro In the face of a cyberattack, every second can be the thin line between maintaining your...
Google Initiative Aims to Boost AI for Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Google is pushing AI as the technology that will shift the balance of power from cyberattackers to security professionals and...
Join our new Escape community on Slack! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova We’re migrating Escape Community from Discord to Slack! After feedback from our community members and a long thought, we’ve decided...
LockBit Infrastructure Seized By US, UK Police – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware LockBit Ransomware Operations Is Latest to Fall in Series of Takedowns Akshaya Asokan (asokan_akshaya) ,...
Zenlayer Exposes 384 Million Records – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Exposed Database at Network Services Firm Included Server Log Details Prajeet Nair (@prajeetspeaks) • February 19,...
Webinar | 5 Ways Cybersecurity Leaders Can Leverage GenAI in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
New Guides Aim to Help Health Sector Beef Up Cyber, Privacy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 HIPAA/HITECH , Standards, Regulations & Compliance HHS OCR, NIST Finalize HIPAA Cyber Guide; HSCC Issues Security, Privacy Resource Marianne Kolbasuk McGee...
NIST Offers Concrete Steps for Secure Software Development – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Governance & Risk Management , Government New Guidelines Include ‘Absolutely Crucial’ Steps to Enhance Security, Experts...
Security Economics Knowledge Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...