Source: www.darkreading.com – Author: Dark Reading Staff Source: imageBROKER via Alamy Stock Photo The US Department of State is offering $10 million for information that can...
Day: February 15, 2024
Bugcrowd Secures $102M in Strategic Growth Funding to Scale AI-Powered Crowdsourced Security Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, February 12, 2024 – Bugcrowd has secured $102 million in strategic growth financing to scale its AI-powered crowdsourced security...
33M French Citizens Impacted in Country’s Largest-Ever Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: John Kellerman via Alamy Stock Photo The French data protection agency, the CNIL, has...
Prudential Financial Faces Cybersecurity Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Prudential Financial has disclosed a cybersecurity breach. Detected on February 5 2024, the breach involved unauthorized access to certain company systems. In...
Crypto-Money Laundering Records 30% Annual Decline – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Just over $22bn worth of cryptocurrency was laundered in 2023, a 30% drop from the previous year, with nefarious actors switching...
Microsoft, OpenAI Confirm Nation-States are Weaponizing Generative AI in Cyber-Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Nation-state threat actors are making use of generative AI tools, including large language models (LLMs) like ChatGPT, in their cyber operations,...
GoldPickaxe Trojan Blends Biometrics Theft and Deepfakes to Scam Banks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have warned of a sophisticated new Trojan designed to steal facial biometric data and use it to produce deepfakes of...
Water Hydra’s Zero-Day Attack Chain Targets Financial Traders – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Trend Micro Zero Day Initiative (ZDI) has recently unearthed a critical vulnerability, identified as CVE-2024-21412, which they’ve dubbed ZDI-CAN-23100. The...
PII Input Sparks Cybersecurity Alarm in 55% of DLP Events – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A substantial 55% of recent Data Loss Prevention (DLP) events have involved attempts to input personally identifiable information (PII), while 40%...
Iranian Hackers Target Israel and US to Sway Public Opinion in Hamas Conflict – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Google’s Threat Analyst Group has confirmed that Iran-backed hackers have used their cyber capabilities to undercut public support for the Israel-Hamas conflict...
Cybersecurity Spending Expected to be Slashed in 41% of SMEs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity spending is predicted to be cut by 41% of SMEs over the coming year amid the challenging economic environment, according...
Microsoft Fixes Two Zero-Days in February Patch Tuesday – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft has landed system administrators with a busy February after releasing updates for 73 vulnerabilities, including two zero-day flaws currently under...
Romantic AI Chatbots Fail the Security and Privacy Test – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Experts have warned users of AI-powered “relationship” chatbots that their data and privacy are at risk, after failing all 11 apps...
Southern Water Notifies Customers and Employees of Data Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Southern Water has confirmed that personal data of both customers and employees has been accessed in a recent ransomware attack. The...
Bank of America Customers at Risk After Data Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Bank of America has alerted its customers about a recent data breach that occurred through one of its service providers, Infosys...
CISA adds Microsoft Windows bugs to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Microsoft Windows bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 15, 2024 U.S. Cybersecurity and Infrastructure...
Nation-state actors are using AI services and LLMs for cyberattacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Nation-state actors are using AI services and LLMs for cyberattacks Pierluigi Paganini February 15, 2024 Microsoft and OpenAI warn that...
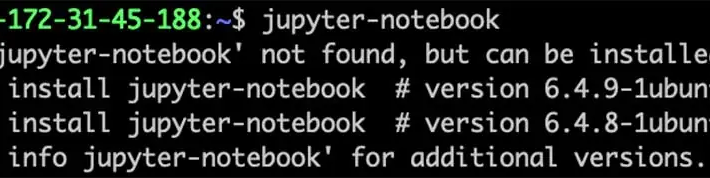
Abusing the Ubuntu ‘command-not-found’ utility to install malicious packages – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Abusing the Ubuntu ‘command-not-found’ utility to install malicious packages Pierluigi Paganini February 14, 2024 Researchers reported that attackers can exploit...
Zoom fixed critical flaw CVE-2024-24691 in Windows software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Zoom fixed critical flaw CVE-2024-24691 in Windows software Pierluigi Paganini February 14, 2024 Zoom addressed seven vulnerabilities in its desktop...
Microsoft Patch Tuesday for February 2024 fixed 2 actively exploited 0-days – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft Patch Tuesday for February 2024 fixed 2 actively exploited 0-days Pierluigi Paganini February 14, 2024 Microsoft Patch Tuesday security...
A ransomware attack took 100 Romanian hospitals down – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A ransomware attack took 100 Romanian hospitals down Pierluigi Paganini February 13, 2024 Authorities in Romania reported that at least...
Bank of America customer data compromised after a third-party services provider data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Bank of America customer data compromised after a third-party services provider data breach Pierluigi Paganini February 13, 2024 Bank of...
How Nation-State Actors Target Your Business: New Research Exposes Major SaaS Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 15, 2024The Hacker NewsSaaS Security / Risk Management With many of the highly publicized 2023 cyber attacks revolving around one...
Chinese Hackers Using Deepfakes in Advanced Mobile Banking Malware Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . A Chinese-speaking threat actor codenamed GoldFactory has been attributed to the development of highly sophisticated banking trojans, including a previously undocumented...
Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 15, 2024NewsroomThreat Intelligence / Vulnerability Microsoft on Wednesday acknowledged that a newly disclosed critical security flaw in Exchange Server has...
Google Threat Analysis Group’s Spyware Research: How CSVs Target Devices and Applications – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet A new publication from Google’s Threat Analysis Group focuses on commercial surveillance vendors, whose services are bought by governments for...
How to Use LogMeOnce Step-by-Step Guide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Image: LogMeOnce LogMeOnce is a decent password manager that includes a wide range of multifactor authentication (MFA) options. In this...
Incident Response Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy from TechRepublic Premium provides information on defining an incident, assigning an incident response team, documenting a plan and conducting a...
Network Security: A Top Priority for Healthcare Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireMon FireMon is purpose-built for compliance reporting with 12 built-in reports, over 500 controls, and the ability to customize using a native...
5 Reasons You Should See a DSPM This Valentine’s Day – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy It’s time to embrace the season of love and connection. Valentine’s Day is the perfect time to reevaluate our relationships—not just...