Source: www.bleepingcomputer.com – Author: Lawrence Abrams Clorox has confirmed that a September 2023 cyberattack has so far cost the company $49 million in expenses related to...
Day: February 3, 2024
Check if you’re in Google Chrome’s third-party cookie phaseout test – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google has started testing the phasing out of third-party cookies on Chrome, affecting about 1% of its users or approximately...
Mastodon vulnerability allows attackers to take over accounts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Mastodon, the free and open-source decentralized social networking platform, has fixed a critical vulnerability that allows attackers to impersonate and...
Friday Squid Blogging: Illex Squid in Argentina Waters – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Illex Squid in Argentina Waters Argentina is reporting that there is a good population of illex...
David Kahn – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments sam • February 2, 2024 5:18 PM I too was first intrigued by Kahn’s The Codebreakers. I feel...
Forget Deepfakes or Phishing: Prompt Injection is GenAI’s Biggest Problem – Source: www.darkreading.com
Source: www.darkreading.com – Author: Source: Luis Moreira via Alamy Stock Photo As troubling as deepfakes and large language model (LLM)-powered phishing are to the state of...
CISO Corner: Gen Z Challenges, CISO Liability & Cathay Pacific Case Study – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Andrew Unangst via Alamy Stock Photo Welcome to CISO Corner, Dark Reading’s weekly digest...
Myanmar Hands Over Mob Bosses in Cyber-Fraud Bust – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Ruma Aktar via Alamy Stock Photo Myanmar authorities have transferred 10 suspects accused of being involved in organized...
macOS Malware Campaign Showcases Novel Delivery Technique – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Bhubeth Bhajanavorakul via Alamy Stock Photo Security researchers have sounded the alarm on a new cyberattack campaign...
Microsoft Threat Report: How Russia’s War on Ukraine Is Impacting the Global Cybersecurity Community – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security Source: Science Photo Library via Alamy Stock Russia’s war on Ukraine has entered a new phase. Based on cyber threat...
Botnet Attack Targeted Routers: A Wake-Up Call for Securing Remote Employees’ Hardware – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse State-sponsored hackers affiliated with China have targeted small office/home office routers in the U.S. in a wide-ranging botnet attack, Federal...
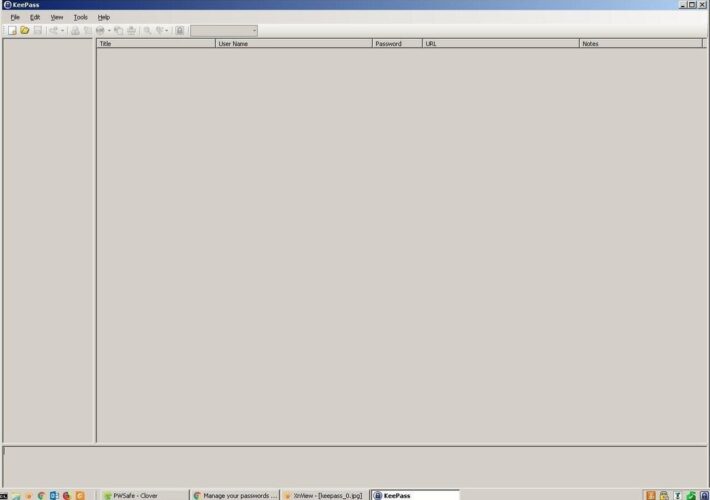
How to Use KeePass Step-by-Step Guide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares KeePass is a free and open source password manager geared toward power users and tech enthusiasts. In this article, we...
U.S. Sanctions 6 Iranian Officials for Critical Infrastructure Cyber Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 03, 2024NewsroomIntelligence Agency / Cyber Security The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) announced sanctions against six...
Mastodon Vulnerability Allows Hackers to Hijack Any Decentralized Account – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 03, 2024NewsroomVulnerability / Social Media The decentralized social network Mastodon has disclosed a critical security flaw that enables malicious actors...
AnyDesk Hacked: Popular Remote Desktop Software Mandates Password Reset – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 03, 2024NewsroomCyber Attack / Software Security Remote desktop software maker AnyDesk disclosed on Friday that it suffered a cyber attack...
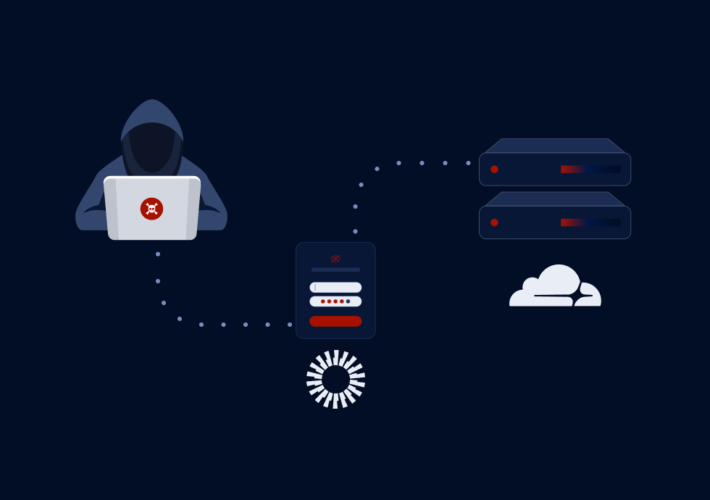
Cloudflare Falls Victim to Cyberattack Leveraging Credentials from Okta Breach – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Cloudflare disclosed a security breach today, revealing that a suspected nation-state attacker infiltrated its internal Atlassian server. The attack, which...
The Week in Ransomware – February 2nd 2024 – No honor among thieves – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Attacks on hospitals continued this week, with ransomware operations disrupting patient care as they force organization to respond to cyberattacks....
AnyDesk says hackers breached its production servers, reset passwords – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams AnyDesk confirmed today that it suffered a recent cyberattack that allowed hackers to gain access to the company’s production systems....
Lurie Children’s Hospital took systems offline after cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Lurie Children’s Hospital in Chicago was forced to take IT systems offline after a cyberattack, disrupting normal operations and delaying...
BTC-e server admin indicted for laundering ransom payments, stolen crypto – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Aliaksandr Klimenka, a Belarusian and Cypriot national, has been indicted in the U.S. for his involvement in an international cybercrime...
Interpol operation Synergia takes down 1,300 servers used for cybercrime – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An international law enforcement operation code-named ‘Synergia’ has taken down over 1,300 command and control servers used in ransomware, phishing,...
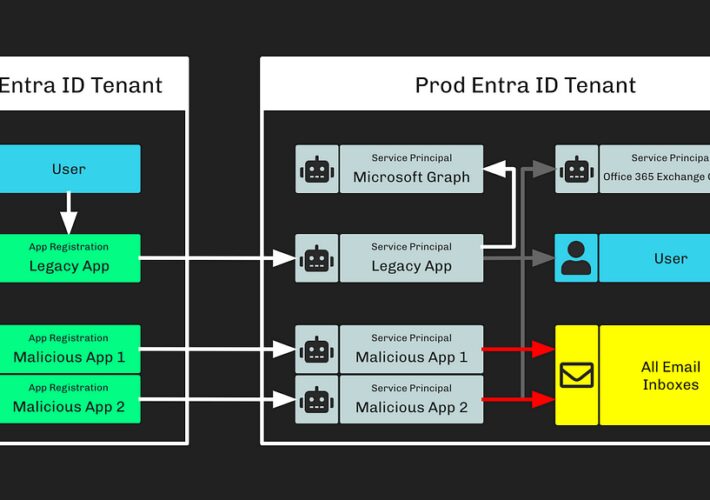
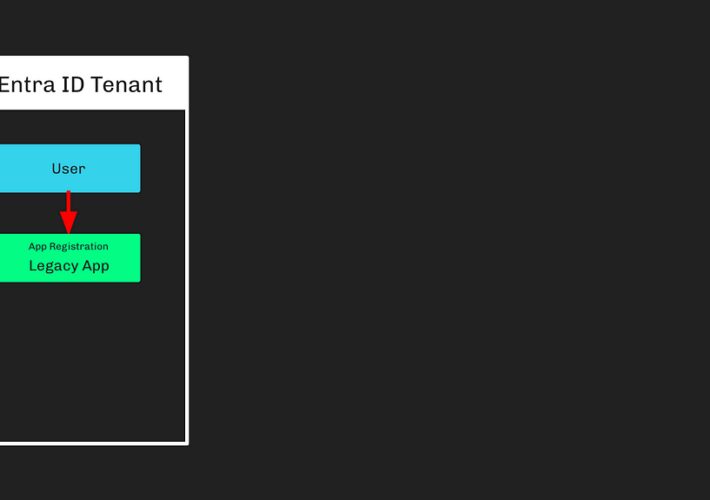
Microsoft Breach — How Can I See This In BloodHound? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stephen Hinck Microsoft Breach — How Can I See This In BloodHound? Summary On January 25, 2024, Microsoft announced Russia’s foreign intelligence service (i.e.,...
Microsoft Breach — What Happened? What Should Azure Admins Do? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Microsoft Breach — What Happened? What Should Azure Admins Do? On January 25, 2024, Microsoft published a blog post that detailed their recent...
MSP DMARC Journey For Effective Lead Generation: Watchdog Cyber’s Sucess Story – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anush Yolyan ABOUT THE CLIENT Headquarters: Spring Lake, Michigan Website: www.watchdogcyber.com Founded: 2022 Industry: Managed Service Provider Watchdog Cyber delivers proactive cybersecurity...
USENIX Security ’23 – Anrin Chakraborti, Duke University; Darius Suciu, Radu Sion – Wink: Deniable Secure Messaging – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Anrin Chakraborti, Duke University; Darius Suciu, Radu...
Survey Surfaces Raft of Cloud Security Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A global survey of 414 IT practitioners published this week found 40% of respondents are relying on legacy platforms and...
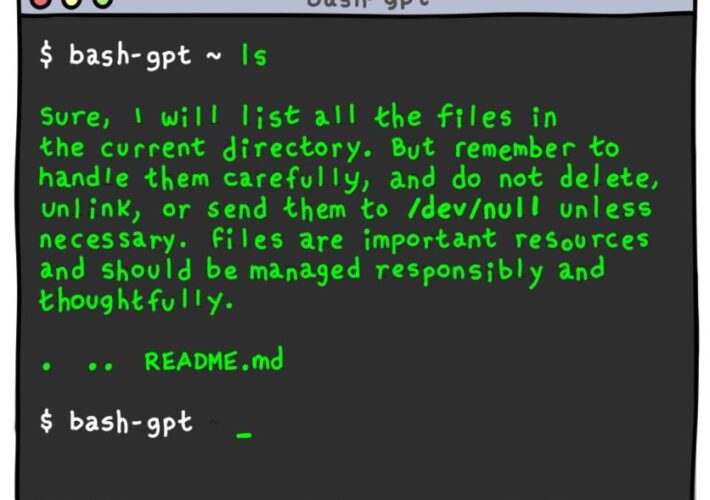
Daniel Stori’s ‘bash-gpt’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the webcomic talent of the inimitable Daniel Stori at Turnoff.US. Permalink *** This is a Security Bloggers Network syndicated...
The Secret’s Out: How Stolen Okta Auth Tokens Led to Cloudflare Breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Segura What Happened? Cloudflare’s internal Atlassian systems were breached using tokens and service accounts compromised from a previous Okta breach. The...
USENIX Security ’23 – David Balbás, Daniel Collins, Serge Vaudenay – Cryptographic Administration for Secure Group Messaging – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – David Balbás, Daniel Collins, Serge Vaudenay –...
Microsoft Ditches C# for Rust: M365 Core Gets Safety and Perf Boosts – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Microsoft 365 “Core Platform Substrate” gets rewrite in Rust language. A job ad seems to say Microsoft is going all in...