Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK – Jan. 25, 2024 — SecurityScorecard today announced SecurityScorecard MAX™, a new partner-focused managed service from SecurityScorecard that builds on the company’s...
Day: January 26, 2024
Help Wanted From Convicted Cybercriminals – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Source: Andriy Popov via Alamy Stock Photo The most recent ISC2 Cybersecurity Workforce Study found a...
Pwn2Own 2024: Tesla Hacks, Dozens of Zero-Days in Electrical Vehicles – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Rosemary Roberts via Alamy Stock Photo In just two days at Pwn2Own 2024 in Tokyo, researchers have...
‘Midnight Blizzard’ Breached HPE Email Months Before Microsoft Hack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: trambler58 via Shutterstock Months before Russian threat actor “Midnight Blizzard” accessed and exfiltrated data from email accounts...
Panorays Study Finds 94% of CISOs Are Concerned About Third-party Cyber Threats, Yet Only 3% Have Implemented Security Measures – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK (January 25, 2024) – Panorays, a leading provider of third-party security risk management software, has conducted its 2024 CISO Survey of...
Protecting Children’s Data Needs to Be a Priority for All – Source: www.darkreading.com
Source: www.darkreading.com – Author: Steve Yin Source: Chad Ehlers via Alamy Stock Photo COMMENTARY Organizations are facing a challenging cybersecurity environment and a chaotic threat landscape....
Critical Cisco Unified Communications RCE Bug Allows Root Access – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading 1 Min Read Source: Anucha Cheechang via Shutterstock A critical security vulnerability in Cisco Unified...
‘CherryLoader’ Malware Allows Serious Privilege Execution – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer 2 Min Read Source: kevers via Alamy Stock Photo It’s the pits for admins: Researchers have discovered a...
Abu Dhabi Investment Firm Warns About Scam Efforts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: designer491 via Alamy Stock Photo The National Investor, an Abu Dhabi-based investment management and advisory firm, has warned that...
More Australian IT Leaders Could Be Looking to Replace Passwords With Passkeys in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott The Australian government announced in 2023 that it would phase out the use of passwords to access key government digital...
How to Prevent Phishing Attacks with Multi-Factor Authentication – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
23andMe data breach: Hackers stole raw genotype data, health reports – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Genetic testing provider 23andMe confirmed that hackers stole health reports and raw genotype data of customers affected by a credential...
Blackwood hackers hijack WPS Office update to install malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A previously unknown advanced threat actor tracked as ‘Blackwood’ is using sophisticated malware called NSPX30 in cyberespionage attacks against companies...
Russian TrickBot malware dev sentenced to 64 months in prison – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Russian national Vladimir Dunaev has been sentenced to five years and four months in prison for his role in creating...
iPhone apps abuse iOS push notifications to collect user data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Numerous iOS apps are using background processes triggered by push notifications to collect user data about devices, potentially allowing the...
Tesla hacked again, 24 more zero-days exploited at Pwn2Own Tokyo – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Security researchers hacked the Tesla infotainment system and demoed 24 more zero-days on the second day of the Pwn2Own Automotive...
Cisco warns of critical RCE flaw in communications software – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cisco is warning that several of its Unified Communications Manager (CM) and Contact Center Solutions products are vulnerable to a...
Hackers target WordPress database plugin active on 1 million sites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Malicious activity targeting a critical severity flaw in the ‘Better Search Replace’ WordPress plugin has been detected, with researchers observing...
AI is already being used by ransomware gangs, warns NCSC – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley In a newly published report, the UK’s National Cyber Security Centre (NCSC) has warned that malicious attackers are already taking...
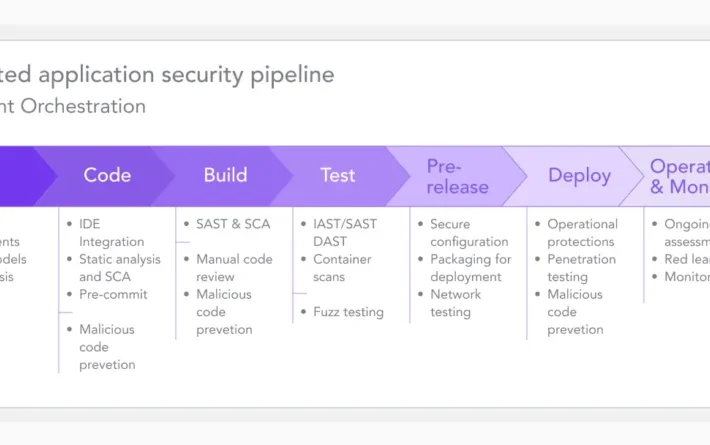
CI/CD Pipeline Security: Best Practices Beyond Build and Deploy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Julie Peterson CI/CD Pipeline Security Given the demand for rapid innovation and the adoption of agile methodologies, Continuous Integration/Continuous Deployment (CI/CD) pipelines...
USENIX Security ’23 – Wenjun Qiu, David Lie, Lisa Austin – Calpric: Inclusive and Fine-grain Labeling of Privacy Policies with Crowdsourcing and Active Learning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, January 25, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Malicious AdTech Spies on People as NatSec Targets – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Patternz and Nuviad enable potentially hostile governments to track individuals by misusing ad bidding. Two companies are allegedly tracking target...
AI Will Fuel Rise in Ransomware, UK Cyber Agency Says – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The accelerating innovation of generative AI will increase the risks of ransomware and other cyberthreats over the next two years...
That new X cryptocurrency? It’s a scam. – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog In the dynamic landscape of online scams, our Avast team has identified a new and bold scam, using the likeness...
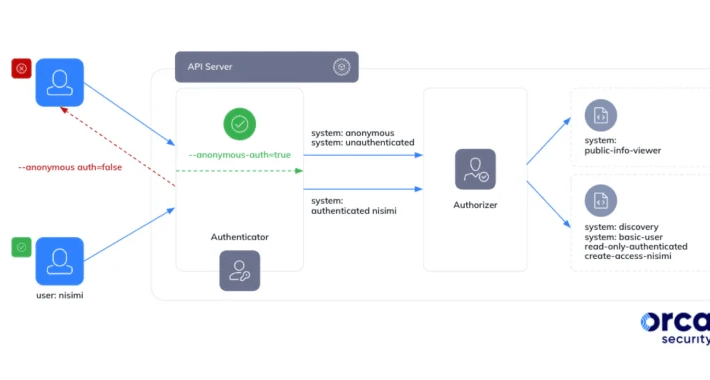
Shield GKE’s Achilles Heel using RBAC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ben Hirschberg If you’re using GKE (Google Kubernetes Engine), you should be extremely cautious when adding roles to the system:authenticated group because...
Organizations are Embracing Cyber Insurance, But It’s Not Easy: Survey – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The growing number and sophistication of cyberattacks and the financial impact such incidents can have a company’s financial picture are...
Meet the Ona: Radu Boian – Source: securityboulevard.com
Source: securityboulevard.com – Author: ltabo Meet the Ona: Radu Boian ltabo Thu, 01/25/2024 – 15:01 Hi, my name is Radu, I am 31 years old and...
The Cybersecurity Horizon: AI, Resilience and Collaboration in 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Steve Winterfeld In the ever-evolving landscape of cybersecurity, securing your company’s operations and safeguarding customer experiences is an intricate and crucial challenge,...
Scoping Chatbots for Safe and Effective Experiences – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michal Oglodeck Mark McNasby, CEO and co-founder of Ivy.ai, co-authored this article. Artificial intelligence has turned our world upside down, and organizations...
Russian Hacker Sentenced to Over 5 Years in US Prison – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Vladimir Dunaev Acknowledged Acting ‘Recklessly’ in Working for Cybercriminal Group Chris Riotta (@chrisriotta) • January...