Source: www.securityweek.com – Author: Ryan Naraine Patch Tuesday: Redmond patches critical, remote code execution vulnerabilities haunting Windows Kerberos and Windows Hyper-V. The post Microsoft Ships Urgent...
Day: January 9, 2024
Delinea Acquires Authomize to Tackle Identity-Based Threats – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Delinea acquires Israeli startup Authomize to add identity threat detection and response (IDTR) technologies to its product portfolio. The post...
CISA Warns of Apache Superset Vulnerability Exploitation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire CISA has added a critical-severity Apache Superset flaw (CVE-2023-27524) to its Known Exploited Vulnerabilities catalog. The post CISA Warns of...
Adobe Patches Code Execution Flaws in Substance 3D Stager – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Patch Tuesday: Adobe patches six security flaws in the Substance 3D Stager product and warned of code execution risks on...
Siemens, Schneider Electric Release First ICS Patch Tuesday Advisories of 2024 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Industrial giants Siemens and Schneider Electric publish a total of 7 new security advisories addressing 22 vulnerabilities. The post Siemens,...
Turkish Hackers Target Microsoft SQL Servers in Americas, Europe – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Researchers at Securonix warn that Turkish threat actors are targeting organizations in the Americas and Europe with ransomware campaigns. The...
Continuity in Chaos: Applying Time-Tested Incident Response to Modern Cybersecurity – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matt Honea Despite the drastically newer and more complex technology, many of the core incident response principles remain the exact same and...
Bosch Nutrunner Vulnerabilities Could Aid Hacker Attacks Against Automotive Production Lines – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Hackers can take complete control of Bosch Rexroth nutrunners, installing ransomware or altering settings to cause financial impact and brand...
LoanDepot Takes Systems Offline Following Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Mortgage lending firm LoanDepot has disclosed a cyberattack resulting in data encryption and system disruptions. The post LoanDepot Takes Systems...
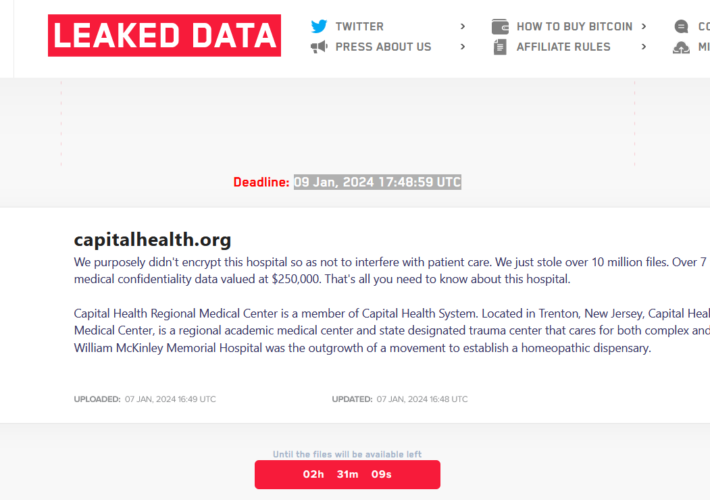
Ransomware Gang Claims Attack on Capital Health – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The LockBit ransomware gang claims to have stolen over 7 terabytes of data from hospital system Capital Health. The post...
Microsoft Patch Tuesday for January 2024 fixed 2 critical flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft Patch Tuesday for January 2024 fixed 2 critical flaws Microsoft Patch Tuesday security updates for January 2024 addressed a...
CISA adds Apache Superset bug to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Apache Superset bug to its Known Exploited Vulnerabilities catalog U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Apache...
LockBit ransomware gang claims the attack on Capital Health – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini LockBit ransomware gang claims the attack on Capital Health The LockBit ransomware gang claimed responsibility for the cyber attack on...
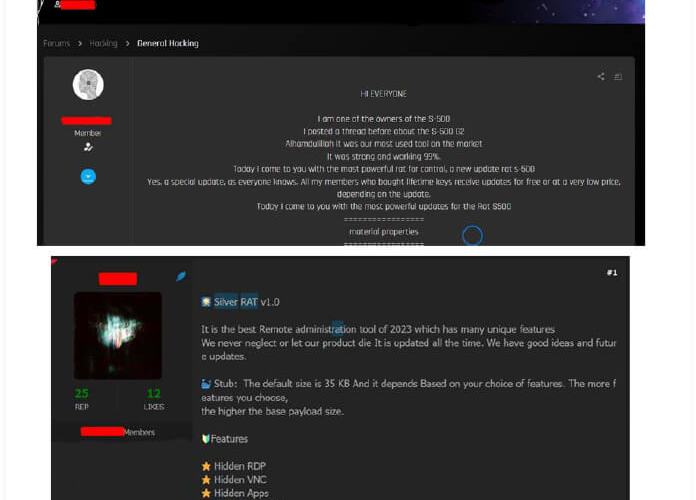
Syrian group Anonymous Arabic distributes stealthy malware Silver RAT – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Syrian group Anonymous Arabic distributes stealthy malware Silver RAT A hacker group that calls itself Anonymous Arabic is distributing a...
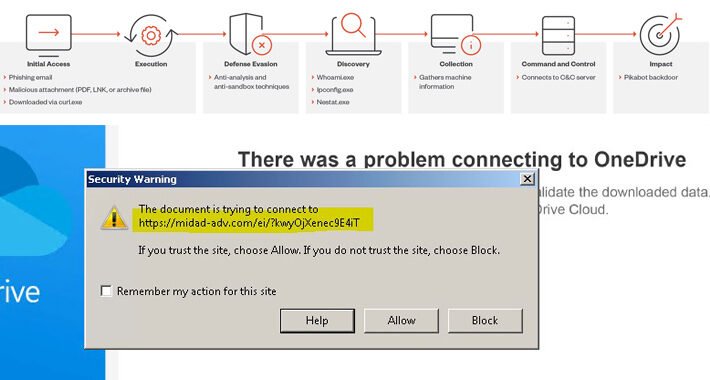
Alert: Water Curupira Hackers Actively Distributing PikaBot Loader Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024NewsroomMalware / Cyber Threat A threat actor called Water Curupira has been observed actively distributing the PikaBot loader malware...
Turkish Hackers Exploiting Poorly Secured MS SQL Servers Across the Globe – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024NewsroomData Security / Cyber Attack Poorly secured Microsoft SQL (MS SQL) servers are being targeted in the U.S., European...
Why Public Links Expose Your SaaS Attack Surface – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024The Hacker NewsSaaS Security / Data Security Collaboration is a powerful selling point for SaaS applications. Microsoft, Github, Miro,...
ONLINE FRAUD SCHEMES: A WEB OF DECEIT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
PIN-Stealing Android Malware – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier This is an old piece of malware—the Chameleon Android banking Trojan—that now disables biometric authentication in order to steal the...
Midwives clinic takes nine months to deliver news of data breach – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley CBC News in Canada is reporting that clients of a pregnancy care clinic in Ontario have had their personal information...
Sexual assault in the metaverse investigated by British police – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The Daily Mail reports on what may be the first time UK police have investigated a sexual assault in cyberspace:...
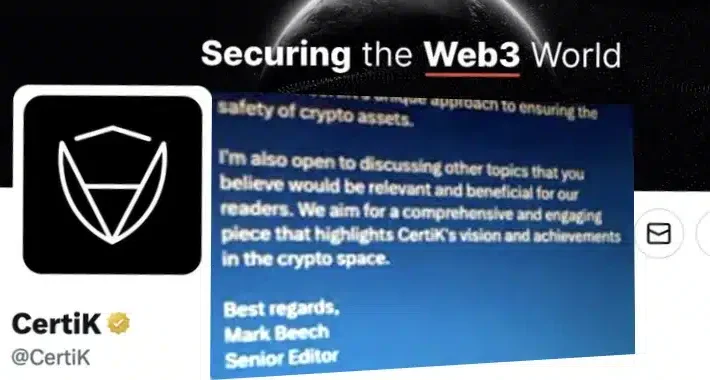
CertiK Twitter account hijacked by cryptocurrency scammer posing as Forbes journalist – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Web3 security outfit CertiK has fallen foul of scammers, who managed to hijack its Twitter account to share a malicious...
Cybersecurity firm Mandiant has its Twitter account hacked to promote cryptocurrency scam – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Google-owned cybersecurity company Mandiant has found itself in the awkward position of having to wrestle back control of its Twitter...
2023 NSA CYBERSECURITY Year In Review
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Data Confidentiality: Identifying and Protecting Assets Against Data Breaches
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIST CSF 2.0
Draft & Implementation Examples The NIST Cybersecurity Framework is a technical guide for organisations to improve their cybersecurity. It outlines steps to govern, identify, protect, detect,...
NETWORK PENETRATION TESTING
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NCSC Cyber Security Framework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
National Computer Security Day
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft Office and Windows HTML Remote Code Execution
Looking at the reason that triggers the Alert, it has been found out that the system is trying to exploit the CVE-2023-36884 vulnerability which is a...