Source: www.bleepingcomputer.com – Author: Bill Toulas Cloudflare’s Firewall and DDoS prevention can be bypassed through a specific attack process that leverages logic flaws in cross-tenant security...
Year: 2023
Microsoft fixes Outlook prompts to reopen closed windows – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has resolved a known issue that caused Outlook Desktop to unexpectedly prompt users to reopen previously closed windows. “This...
A Closer Look at the Snatch Data Ransom Group – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and...
Hackers Impersonate Meta Recruiter to Target Aerospace Firm – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Lazarus Deploys New Backdoor to Target Aerospace Firm Vasudevan...
Avoid libwebp Electron Woes On macOS With positron – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr If you’ve got on this blog (directly, or via syndication) you’d have to have been living under a rock to not...
A Closer Look at the Snatch Data Ransom Group – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and...
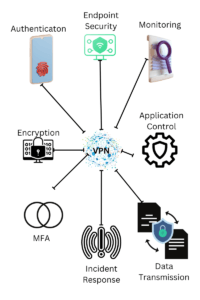
Discover Endpoint VPN in 2023: Unlocking Secure Remote Access – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Introduction In today’s interconnected world, the need for secure remote access to networks and data has never been more crucial....
DEF CON 31 – Lorenzo Cococcia ‘s ‘War Stories – Finding Foes And Yourself With Latency Trilateration’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/def-con-31-lorenzo-cococcia-s-war-stories-finding-foes-and-yourself-with-latency-trilateration/ Category & Tags: Security Bloggers Network,Cybersecurity,cybersecurity education,DEF...
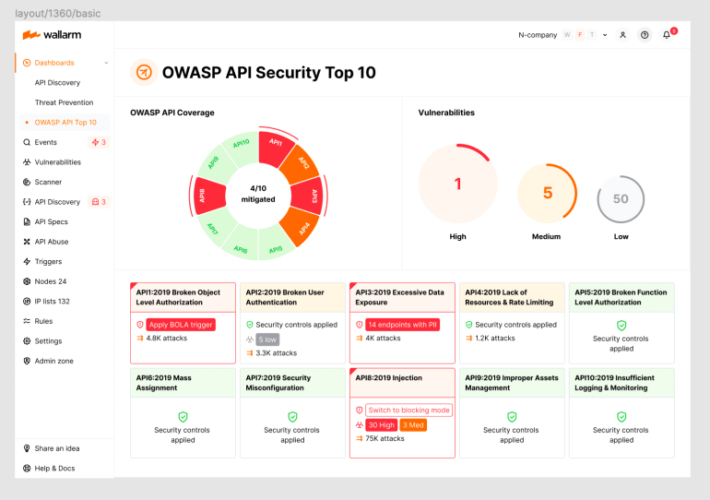
2023 OWASP Top-10 Series: API10:2023 Unsafe Consumption of APIs – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Welcome to the 11th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...
The Cyber Defense Index 2022-23 – A benchmark of the digital security preparedness of enterprises across the threat landscapes of the worlds top economies by MIT Technology Review Insights.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft Entra – The Comprensive Guide to Secure Azure AD & User Identities by Mohamed Mokhtar & Microsoft Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Reporte sobre el desarrollo de la FUERZA LABORAL DE CIBERSEGURIDAD 2023 by OEA, CIC y CISCO en una era de escasez de talento y habilidades.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Governance Framework for National Cybersecurity Strategies by European Union Agency for Cybersecurity – enisa
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Coming AI Hackers – Council for the responsible use of AI by Bruce Schneier
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SANS DFIR – CHEAT SHEETS & NOTEBOOKS – The most complete reference !!!
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity in a Digital Era by McKinsey. Digital McKinsey and Global Risk Practice.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Artificial Intelligence Risk Management Framework – AI RMF 1.0 By NIST
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Digest of Cyber Organized Crime by UNODC – United Nations Office on Drugs and Crime
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ChatGPT for Cybersecurity by Joas Antonio dos Santos – malwareanalysis #reverseengineering
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Risk Report 2023 by RiskLens
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SANS Institute – Incident Handler´s Handbook by Patrick Kral
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Russia´s Cyber Tactics – Lessons Learnead 2022 by Information Protection of Ukraine
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Global Cybersecurity Outlook 2023 Insight Report by WEF – World Economic Forum in collaboration with Accenture
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Digital Forensics and Incident Response (DFIR) Framework for Operational Technology (OT) by NIST – Eran Salfati and Michael Pease
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Internet Crime Report 2022 by FBI Internet Crime Compliance Center
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CYBERSECURITY The Ultimate Hiring Guide by Stanton house
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Salary for US market and Recruiting Trends Guide 2023 by Stanton House
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The 2023 Crypto Crime Report by Chainalysis – Everithing you need to know about cryptocurrency-based crime
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THE ARMY RED TEAM HANDBOOK – The Guide to Making Better Decisions version 9 by – University of Foreign Military and Cultural Studies (UFMCS).
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Windows Ransomware Detection and Protection – Securing Windows endpoints , the cloud and infrastructure using Microsoft Intune, Sentinel SIEM and Defender by Marius Sandbu – packt.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...