Source: www.securityweek.com – Author: Ionut Arghire iOS zero-click attack targeting Kaspersky iPhones bypassed hardware-based security protections to take over devices. The post Mysterious Apple SoC Feature...
Year: 2023
Barracuda Zero-Day Used to Target Government, Tech Organizations in US, APJ – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The new Barracuda ESG zero-day CVE-2023-7102 has been used by Chinese hackers to target organizations in the US and APJ...
Cyberattack Disrupts Operations of First American, Subsidiaries – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A cyberattack appears to have caused significant disruption to the systems and operations of title insurer First American and its...
Refocusing on Cybersecurity Essentials in 2024: A Critical Review – Source: www.securityweek.com
Source: www.securityweek.com – Author: Torsten George By supplementing traditional perimeter defense mechanisms with principles of data integrity, identity management, and risk-based prioritization, organizations can reduce their...
AI and Lossy Bottlenecks – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier Artificial intelligence is poised to upend much of society, removing human limitations inherent in many systems. One such limitation is...
New iPhone Security Features to Protect Stolen Devices – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Apple is rolling out a new “Stolen Device Protection” feature that seems well thought out: When Stolen Device Protection is...
Experts warn of critical Zero-Day in Apache OfBiz – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of critical Zero-Day in Apache OfBiz Pierluigi Paganini December 28, 2023 Experts warn of a zero-day flaw that...
Xamalicious Android malware distributed through the Play Store – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Xamalicious Android malware distributed through the Play Store Pierluigi Paganini December 27, 2023 Researchers discovered a new Android malware dubbed...
Barracuda fixed a new ESG zero-day exploited by Chinese group UNC4841 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Barracuda fixed a new ESG zero-day exploited by Chinese group UNC4841 Pierluigi Paganini December 27, 2023 Security firm Barracuda addressed...
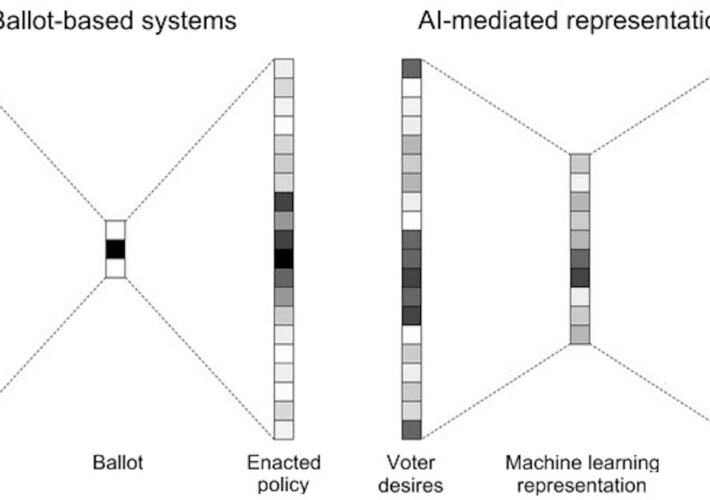
Elections 2024, artificial intelligence could upset world balances – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Elections 2024, artificial intelligence could upset world balances Pierluigi Paganini December 27, 2023 Governments should recognize electoral processes as critical...
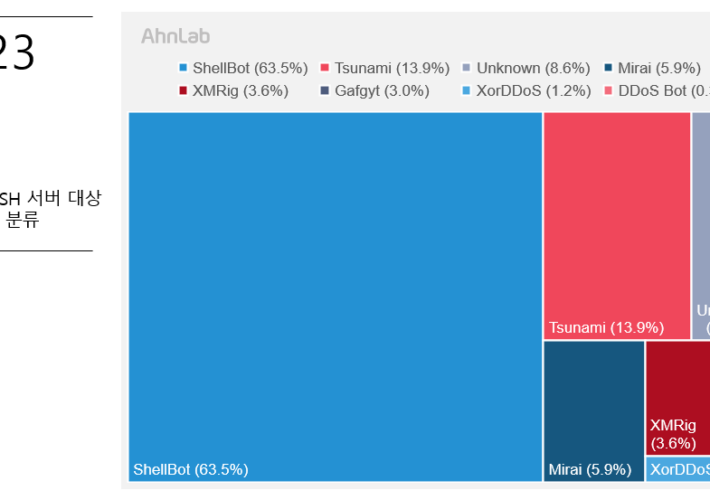
Experts analyzed attacks against poorly managed Linux SSH servers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts analyzed attacks against poorly managed Linux SSH servers Pierluigi Paganini December 27, 2023 Researchers warn of attacks against poorly...
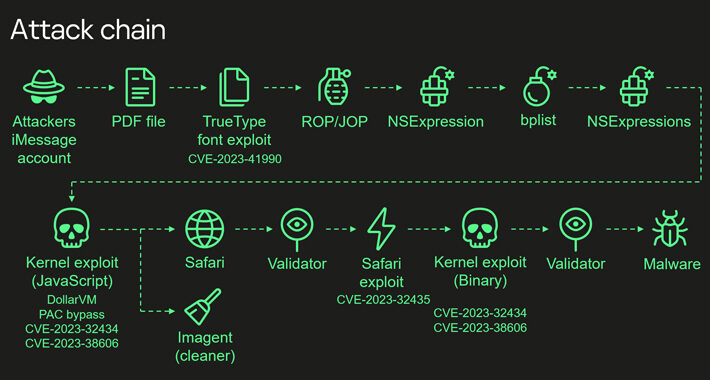
Most Sophisticated iPhone Hack Ever Exploited Apple’s Hidden Hardware Feature – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 28, 2023NewsroomSpyware / Hardware Security The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it...
New Rugmi Malware Loader Surges with Hundreds of Daily Detections – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 28, 2023NewsroomMalware / Cyber Threat A new malware loader is being used by threat actors to deliver a wide range...
Life in the Swimlane with Kevin Mata, Director of Cloud Operations and Automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
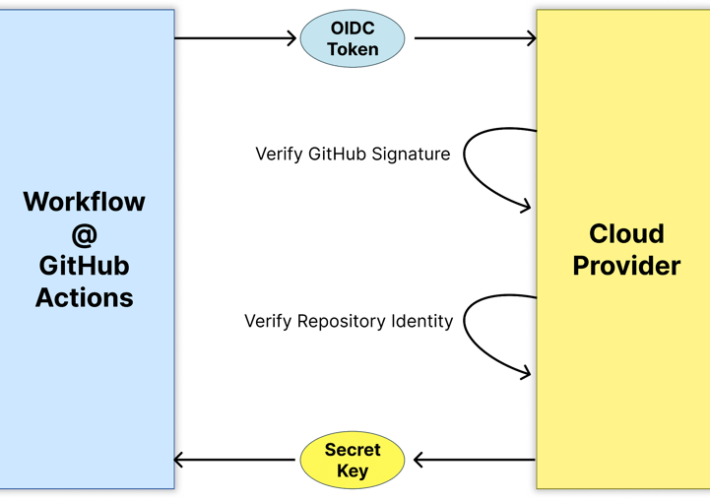
SLSA Provenance Blog Series, Part 3: The Challenges of Adopting SLSA Provenance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gal Ofri In part 2 of the series, we dived into the internals of the provenance document to understand its content and...
USENIX Security ’23 – Hailun Ding, Juan Zhai, Yuhong Nan, Shiqing Ma – ‘AIRTAG: Towards Automated Attack Investigation By Unsupervised Learning With Log Texts’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
USENIX Security ’23 – Noé Zufferey, Mathias Humbert, Romain Tavenard, Kévin Huguenin ‘Watch Your Watch: Inferring Personality Traits From Wearable Activity Trackers’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
MY TAKE: Rising geopolitical tensions suggest a dire need for tighter cybersecurity in 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido Russia’s asymmetrical cyber-attacks have been a well-documented, rising global concern for most of the 2000s. I recently...
Data In-Flight: Applying Zero Trust to Airline Travel and Content Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team No matter which airport you travel through or how many times you travel through it, one element remains the same...
Randall Munroe’s XKCD ‘Definitely’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
The (Face-)Book of Mammon [book review] – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Harley I have, at best, an uneasy relationship with Facebook. To paraphrase something that I’m writing at the moment (more about...
USENIX Security ’23 – ‘Auditory Eyesight: Demystifying μs-Precision Keystroke Tracking Attacks On Unconstrained Keyboard Inputs’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yazhou Tu, Liqun Shan, Md Imran Hossen, Sara Rampazzi, Kevin Butler, Xiali Hei Many thanks to USENIX for publishing their...
Cyberattack Tempo Ratchets Up in Israel – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Cyber Israel Warns of a Wave of Phishing Attempts Mihir Bagwe (MihirBagwe)...
OnDemand Panel | Securing Operational Excellence: Insights into Fortifying OT Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Strengthening OT Security with HCLTech and Microsoft December 27, 2023 In an age reliant on operational technology, ensuring robust...
LIVE Webinar | A Zero Trust Journey for Data Security and Enterprise AI Implementations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Next-Generation Technologies & Secure Development , Zero Trust Presented by LightBeam.AI 60 minutes ...
LIVE Webinar | From Access to Awareness: Unveiling the Zero Trust Data Landscape – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Priyadarshi Prasad Co-Founder and Chief Product Officer, LightBeam.ai Priyadarshi (PD) Prasad is the co-founder and chief product officer at LightBeam.ai. An...
New CMMC Rule Offers Tiered Security Levels for Contractors – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific Defense Department Proposes New Security Requirements for Defense Industrial Base Chris Riotta...
Lawmakers Push NIST for Transparency in AI Research Funding – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development NIST Fails to Provide Information on Award Process for AI...
Why CISOs Need to Make Cyber Insurers Their Partners – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Jenks Source: Olekcii Mach via Alamy Stock Photo In the current threat landscape, the relationship between cyber-insurance providers and potential (or...
How Cybercriminals Will Sway 2024 US Elections, Or Try To – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Casimiro PT via Shutterstock Foreign interference actors, mostly operating out of Russia, Iran, and China, are ramping...










![the-(face-)book-of-mammon-[book-review]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2023/12/109252/the-face-book-of-mammon-book-review-source-securityboulevard-com.jpg)