Source: securityboulevard.com – Author: Jeffrey Burt The Chinese government is accusing the United States intelligence community of launching cyber-espionage campaigns against the country for years after...
Day: September 23, 2023
Randall Munroe’s XKCD ‘xkcd Phone Flip’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, maker of XKCD! Permalink *** This is a Security Bloggers...
Get the Gist of CJIS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Does your organization access CJIS? If so, the deadline for compliance is October 1st, 2023. In the latest CJIS Security...
The Battle Against Cyber Shadows: Ensuring PCI-DSS Compliance Amidst Hidden Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team Digital footprints are expanding at an unprecedented rate, with individuals leaving traces of their credit or debit card information every...
How Silverfort Can Help Organizations Align with NIST’s Cybersecurity Framework Version 2.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Don Hoffman As cyber threats continue to evolve and become more sophisticated, protecting identities and access has never been more critical. To...
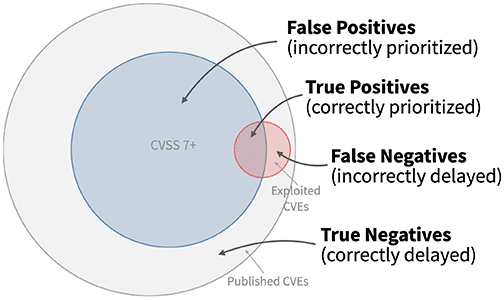
Mastering the Art of Vulnerability Prioritization: A Step-by-Step Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Aguiar The average vulnerability and patch management backlog now contains over 100,000 vulnerabilities, making better vulnerability prioritization essential to ensure the...
Apple Fixes Bugs That Infected Egyptian Politician’s iPhone – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Next-Generation Technologies & Secure Development , Threat Intelligence Cytrox’s Predator Found on Device of Ahmed Eltantawy Mihir Bagwe...
Cloud Smart Roadshow Tallahassee : Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Data Security & Resilience , Security Operations Presented by VMware 300 Minutes Learn how to navigate...
Cloud Smart Roadshow Minneapolis: Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Cloud Data Security & Resilience , Cloud Security 300 Minutes Learn how to navigate...
Cato Networks Raises $238M on $3B Valuation to Move Upmarket – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Access Security Brokers (CASB) , Data Loss Prevention (DLP) , Endpoint Security Equity Investment Will Allow Cato Networks to Tightly...
Cloud Smart Roadshow Bellevue (Seattle): Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Data Security & Resilience , Cloud Security , DevSecOps Presented by VMware 300 Minutes Learn how...
Cloud Smart Roadshow Costa Mesa (Irvine): Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Data Security & Resilience , Cloud Security , DevSecOps Presented by VMware 300 Minutes Learn how...
Chinese, North Korean Nation-State Groups Target Health Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Healthcare HHS Report Lists APT41, APT43 and Lazarus Among Top Threat...
Google CISO Phil Venables on Building Strong CIO-CISO Bonds – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Leadership & Executive Communication , Training & Security Leadership , Video CIO, CISO Must Join Forces to Upgrade Organization to More...
Recast Software Acquires Liquit, Consolidating the Endpoint and Application Management Markets – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Minneapolis, MN (September 21, 2023) — Recast Software, a leader in endpoint management, has acquired Liquit, a leader in application management. With the...
ClassLink Provides Cybersecurity Training Course to Help Schools Protect Public Directory Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 CLIFTON, N.J., Sept. 19, 2023 /PRNewswire/ — ClassLink, the leading provider of identity and access management (IAM) products for education, unveils Scope Your Google...
Wing Security Launches Compliance-Grade SaaS Security Solution for Just $1.5K – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 September 20, 2023, TEL AVIV, Israel – Today, Wing Security (Wing), the leader in SaaS Security Posture Management (SSPM), announced the launch of...
Latest Acquisition Powers AI-based Network Detection and Response and Open XDR Capabilities for WatchGuard – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SEATTLE – September 20, 2023 – WatchGuard® Technologies, a global leader in unified cybersecurity, today announced the acquisition of CyGlass Technology Services, a leading provider...
TikTok API Rules Stymie Analysis of US User Data, Academics Say – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading New terms of service for researchers to access TikTok’s API are a deterrent to analysis of the...
Hackers Let Loose on Voting Gear Ahead of US Election Season – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Election machine manufacturers are opening their wares to hackers in an effort to harden voting security ahead...
Akira Ransomware Mutates to Target Linux Systems, Adds TTPs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading Arika ransomware has continued to evolve since emerging as a threat in March, expanding its reach...
NFL, CISA Look to Intercept Cyber Threats to Super Bowl LVIII – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The NFL is workshopping game plays for Super Bowl LVIII — of the cybersecurity sort....
Apple Fixes 3 More Zero-Day Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In an emergency security update, Apple has identified three zero-day vulnerabilities affecting iPhones and Mac products that...
Dallas says Royal ransomware breached its network using stolen account – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The City of Dallas, Texas, said this week that the Royal ransomware attack that forced it to shut down all...
Nigerian man pleads guilty to attempted $6 million BEC email heist – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Kosi Goodness Simon-Ebo, a 29-year-old Nigerian national extradited from Canada to the United States last April, pleaded guilty to wire...
Recently patched Apple, Chrome zero-days exploited in spyware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Security researchers with the Citizen Lab and Google’s Threat Analysis Group (TAG) revealed today that three zero-days patched by Apple...
Government of Bermuda links cyberattack to Russian hackers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Government of British overseas territory Bermuda has linked a cyberattack affecting all its departments’ IT systems since Thursday to...
Crypto firm Nansen asks users to reset passwords after vendor breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Ethereum blockchain analytics firm Nansen asks a subset of its users to reset passwords following a recent data breach at...
T-Mobile denies new data breach rumors, points to authorized retailer – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams T-Mobile has denied suffering another data breach following Thursday night reports that a threat actor leaked a large database allegedly...
Hotel hackers redirect guests to fake Booking.com to steal cards – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Security researchers discovered a multi-step information stealing campaign where hackers breach the systems of hotels, booking sites, and travel agencies...