Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Hardware-based authentication company Yubico is now a publicly traded company on the Nasdaq First North Growth Market...
Day: September 21, 2023
Fake WinRAR PoC Exploit Conceals VenomRAT Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading In a new twist on the cybercrime penchant for trojanizing things, a threat actor recently...
FBI, CISA Issue Joint Warning on ‘Snatch’ Ransomware-as-a-Service – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Cybersecurity advisories from the FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) are usually...
Dig Security Enhances DSPM Platform to Secure Enterprise Data in On-Prem, File-Share Environments – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TEL AVIV, Israel, September 20, 2023 — Dig, the cloud data security leader, today announced the expansion of the Dig Data Security Platform to protect data...
OneLayer Expands Its Private Cellular Network Security Solutions to Operations and Asset Management – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 BOSTON, Sept. 20, 2023 /PRNewswire/ — OneLayer, a leader in securing private LTE/5G networks for enterprises, announced today the expansion of its private cellular...
83% of IT Security Professionals Say Burnout Causes Data Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 CAMBRIDGE, Mass. – Sept. 19, 2023 – Devo Technology, the cloud-native security analytics company, today unveiled the results of a new...
Bot Attack Costs Double to $86m Annually – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The typical business in the US and UK loses over 4% of their online revenue every year due to malicious bot...
Scams Now Make Up 75% of Cyber-Threats – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Scams involving human manipulation comprised 75% of all desktop threats in the first half of 2023, according to new data from...
US Government in Snatch Ransomware Warning – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Authorities in the US released a new cybersecurity advisory yesterday updating organizations on the latest tactics, techniques and procedures (TTPs) used...
Pro-Russia hacker group NoName launched a DDoS attack on Canadian airports causing severe disruptions – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pro-Russia hacker group NoName launched a DDoS attack on Canadian airports causing severe disruptions Pierluigi Paganini September 21, 2023 Pro-Russia...
Experts found critical flaws in Nagios XI network monitoring software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts found critical flaws in Nagios XI network monitoring software Pierluigi Paganini September 20, 2023 Researchers discovered multiple vulnerabilities in...
The dark web drug marketplace PIILOPUOTI was dismantled by Finnish Customs – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The dark web drug marketplace PIILOPUOTI was dismantled by Finnish Customs Pierluigi Paganini September 20, 2023 Finnish police announced the...
New Revelations from the Snowden Documents – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Jake Appelbaum’s PhD thesis contains several new revelations from the classified NSA documents provided to journalists by Edward Snowden. Nothing...
On the Cybersecurity Jobs Shortage – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier In April, Cybersecurity Ventures reported on extreme cybersecurity job shortage: Global cybersecurity job vacancies grew by 350 percent, from one...
P2PInfect botnet activity surges 600x with stealthier malware variants – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The P2PInfect botnet worm is going through a period of highly elevated activity volumes starting in late August and then...
T-Mobile app glitch let users see other people’s account info – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Today, T-Mobile customers said they could see other peoples’ account and billing information after logging into the company’s official mobile...
TransUnion denies it was hacked, links leaked data to 3rd party – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Credit reporting firm TransUnion has denied claims of a security breach after a threat actor known as USDoD leaked data...
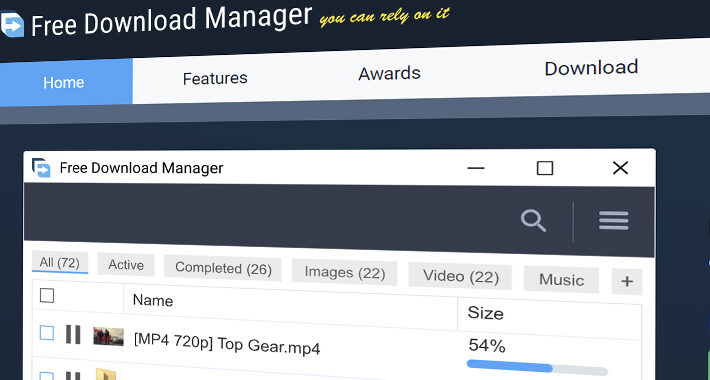
Free Download Manager releases script to check for Linux malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The developers of Free Download Manager (FDM) have published a script to check if a Linux device was infected through...
China Accuses U.S. of Decade-Long Cyber Espionage Campaign Against Huawei Servers – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 21, 2023THNCyber Espionage / Spyware China’s Ministry of State Security (MSS) has accused the U.S. of breaking into Huawei’s servers,...
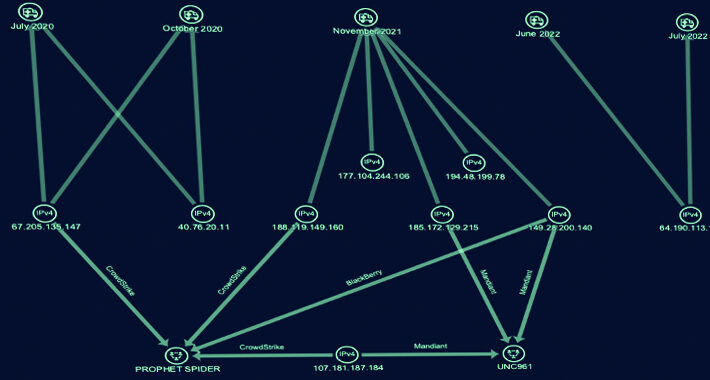
Cyber Group ‘Gold Melody’ Selling Compromised Access to Ransomware Attackers – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 21, 2023THNCyber Threat / Ransomware A financially motivated threat actor has been outed as an initial access broker (IAB) that...
Ukrainian Hacker Suspected to be Behind “Free Download Manager” Malware Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 21, 2023THNSupply Chain / Malware The maintainers of Free Download Manager (FDM) have acknowledged a security incident dating back to...
Beware: Fake Exploit for WinRAR Vulnerability on GitHub Infects Users with Venom RAT – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 21, 2023THNVulnerability / Exploit A malicious actor released a fake proof-of-concept (PoC) exploit for a recently disclosed WinRAR vulnerability on...
International Criminal Court Reveals System Breach and Plans to Bolster Security – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși The International Criminal Court (ICC) announced on September 19th that hackers breached their computer systems. ICC storages highly sensitive information...
Critical GitLab Pipeline Vulnerability Revealed. Users are urged to patch immediately – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși GitLab disclosed critical vulnerability that enables hackers to run pipelines as other users by leveraging scheduled security scan policies. The...
CrowdStrike Fal.Con 2023: CrowdStrike Brings AI and Cloud Application Security to Falcon – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb on September 20, 2023, 6:34 PM EDT CrowdStrike Fal.Con 2023: CrowdStrike Brings AI and Cloud Application Security to Falcon At...
‘Haywire’ Australian IT Skills Market Prompts Logicalis to Add Talent as a Service – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Image: kerkezz/Adobe Stock The IT skills shortage is no secret to Australia’s technology managers. Whether they’ve been hiring new talent...
Secure Equipment Repair Policy and Confidentiality Agreement – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Organizations must frequently work with third parties to repair laptops, desktops, tablets, smartphones, servers and other IT equipment. This policy from TechRepublic...
Orchestration Kitchen Workshop on Migrating CIAM from Keycloak to Amazon Cognito – Source: securityboulevard.com
Source: securityboulevard.com – Author: Heidi King Session will feature speaker from AWS Identity and explain how to move from open source on-premises identity system to developer-friendly...
Everything You Need to Know About Rezilion’s SOC 2 Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: rezilion What is SOC 2 compliance? What exactly does SOC 2 compliance mean? SOC 2 is a voluntary, yet indispensable security standard...
The art of security chaos engineering – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Roberts One truism of the cybersecurity world is that attackers have a much easier job than defenders. Malicious cyber actors only...