Source: thehackernews.com – Author: . Sep 21, 2023THNTelecom Security / Cyber Attack A previously undocumented threat actor dubbed Sandman has been attributed to a set of...
Day: September 21, 2023
Researchers Raise Red Flag on P2PInfect Malware with 600x Activity Surge – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 21, 2023THNBotnet / Cyber Threat The peer-to-peer (P2) worm known as P2PInfect has witnessed a surge in activity since late...
The Rise of the Malicious App – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 21, 2023The Hacker NewsSaaS Security / App Security Security teams are familiar with threats emanating from third-party applications that employees...
Cryptohack Roundup: Private Key Compromise Led to CoinEx Hit – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Mark Cuban Hot Wallet Hack; Crypto Regulation Mihir Bagwe...
Journey to the Cloud: Navigating the Transformation – Part 3 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Security Operations Nikko Asset Management’s Marcus Rameke on SaaS or PaaS vs. IaaS or On-Premises HCI CyberEdBoard •...
Canada Confirms DDoS Attack Disrupted Airport Arrival Kiosks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , DDoS Protection , Fraud Management & Cybercrime How in the World Did Self-Proclaimed Hacktivists Hit System...
LIVE Webinar | Identity Security Alchemy: Transforming Governance Challenges into Gold – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Wade Ellery VP of Solutions Architects and Senior Technical Evangelist, Radiant Logic Wade has extensive experience in enterprise IT direct and...
Breach Roundup: Effects of ISP Ransomware Attack in Colombia – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also, Clorox Product Shortages; California Passes Data Broker Restrictions Anviksha...
UK Parliament Approves Online Safety Bill – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Encryption & Key Management , Geo Focus: The United Kingdom , Geo-Specific Cabinet Ministers Call on Facebook to Stop Rollout of...
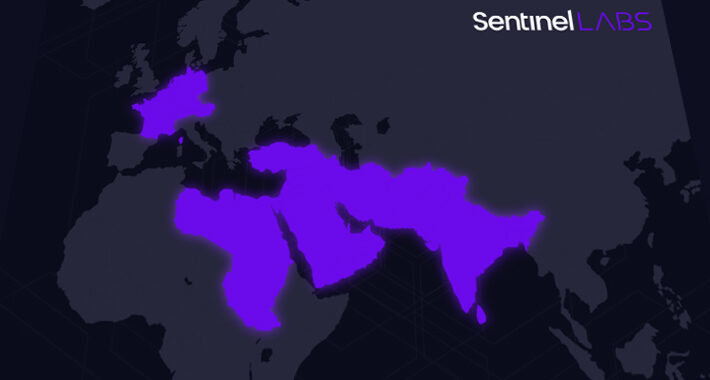
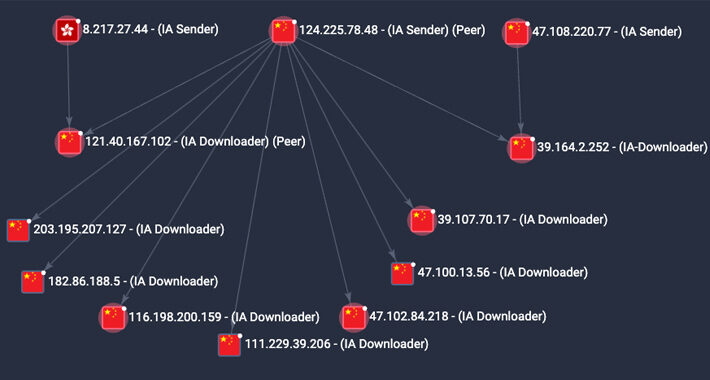
New ‘Sandman’ APT Group Hitting Telcos With Rare LuaJIT Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine A new and mysterious APT group has been spotted targeting telco service providers in Europe and Asia as part of...
Every Network Is Now an OT Network. Can Your Security Keep Up? – Source: www.securityweek.com
Source: www.securityweek.com – Author: John Maddison Every network today is now an OT network. Or it will be soon. Of course, part of this transformation is...
Navigating the Digital Frontier in Cybersecurity Awareness Month 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Torsten George This October will mark the 20th anniversary of Cybersecurity Awareness Month, a pivotal initiative launched under the guidance of the...
TransUnion Denies Breach After Hacker Publishes Allegedly Stolen Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Credit reporting firm TransUnion this week denied being breached, after a hacker published online 3Gb of information allegedly stolen from...
Legit Security Raises $40 Million in Series B Financing – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Application security posture management firm Legit Security on Wednesday announced that it has raised $40 million in a Series B...
Cisco to Acquire Splunk for $28 Billion – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Cisco on Thursday announced that it has entered into a definitive agreement to acquire data analysis, security and observability solutions...
Atlassian Security Updates Patch High-Severity Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Atlassian this week announced patches for four high-severity vulnerabilities impacting its Jira, Confluence, Bitbucket, and Bamboo products. Tracked as CVE-2023-22513...
Car Cybersecurity Study Shows Drop in Critical Vulnerabilities Over Past Decade – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Research-focused security services provider IOActive has conducted an analysis of car vulnerability trends over the past decade and determined that...
UK’s New Online Safety Law Adds to Crackdown on Big Tech Companies – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press British lawmakers have approved an ambitious but controversial new internet safety law with wide-ranging powers to crack down on digital...
Critical Infrastructure Organizations Warned of Snatch Ransomware Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The FBI and the cybersecurity agency CISA on Wednesday published an advisory warning critical infrastructure organizations of ongoing Snatch ransomware...
Snatch ransomware – what you need to know – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley What’s happened? The FBI and US Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint advisory warning organisations about...
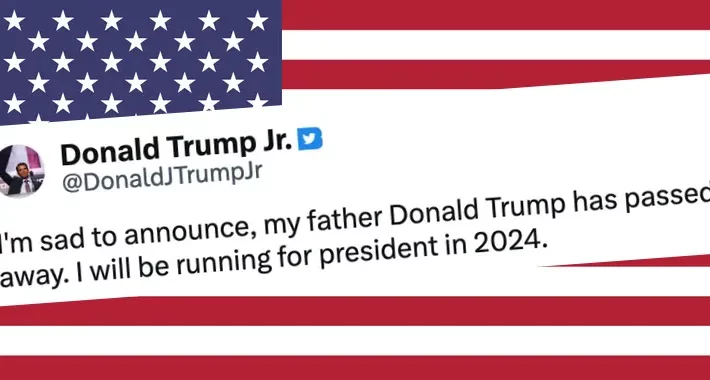
Donald Trump Jr’s hacked Twitter account announces his father has died – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Donald Trump Jr may not have just inherited his famous father’s name. He may also have inherited his bad password...
Smashing Security podcast #340: Heated seats, car privacy, and Graham’s porn video – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Do you know what data your car is collecting about you? Do you think it’s right for a car manufacturer...
UK-US Confirm Agreement for Personal Data Transfers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK government has announced its decision to establish a data bridge with the US, enabling the free flow of personal...
New Ransomware Victims Surge by 47% with Gangs Targeting Small Businesses – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Ransomware attackers are shifting away from “big game” targets and towards easier, less defended organizations, a new report from Trend Micro...
International Criminal Court attacked by cyber criminals – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: One of the world’s most high-profile and highly regarded institutions, the International Criminal Court (ICC), has reported that its...
Black Hat Fireside Chat: Flexxon introduces hardened SSD drives as a last line defense – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Creating ever smarter security software to defend embattled company networks pretty much sums up the cybersecurity industry. Related: The security role...
News alert: Omdia finds risk-based vulnerability management set to encompass the VM market – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido LONDON, Sept. 18, 2023 – The first comparative research into the evolution of the vulnerability management market authored by Omdia has found risk-based vulnerability...
Overview of IoT threats in 2023 – Source: securelist.com
Source: securelist.com – Author: Vitaly Morgunov, Yaroslav Shmelev, Kaspersky Security Services, Kaspersky ICS CERT IoT devices (routers, cameras, NAS boxes, and smart home components) multiply every...
Will Generative AI Kill the Nigerian Prince Scam? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading It was nearly two decades ago that Weldong Xu, a 38-year-old Harvard professor, was arraigned at...
GitLab Users Advised to Update Against Critical Flaw Immediately – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading GitLab users need to update their servers urgently to protect against a new critical flaw that could...