Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/cyber-week-2023-the-israel-national-cyber-directorate-presents-ai-cyber/ Category & Tags: CISO Suite,Governance, Risk &...
Day: September 20, 2023
Black Hat: Deepen Desai, Zscaler – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mitchell Ashley Speaker 1: This is Techstrong TV. Mitch Ashley: Hey, everybody, Mitch Ashley. I am at the Mandelay Bay Suite, the...
Unmasking Reverse Proxy Phishing: Protecting Your Online Identity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Casey Joyce Phishing attacks have long been a major concern in the cybersecurity landscape. These malicious attempts to steal sensitive information often...
What security or other risks might you encounter with IoT? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Introduction In today’s rapidly evolving digital landscape, the surge of Internet of Things (IoT) devices stands out as a transformative...
CrowdStrike Extends Scope of Managed Cybersecurity Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard At its Fal.Con 2023 conference, CrowdStrike made a host of announcements, including the addition of a slew of capabilities to...
Who’s Behind the 8Base Ransomware Website? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The victim shaming website operated by the cybercriminals behind 8Base — currently one of the more active ransomware groups — was...
Expert: Keep Calm, Avoid Overhyping China’s AI Capabilities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development China’s Ability to Diffuse AI Across Economy Lags Ability to...
Journey to the Cloud: Navigating the Transformation – Part 2 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Nikko Asset Management’s Marcus Rameke on the Advantages of HCI On-Premises CyberEdBoard • September 19, 2023...
Generative AI: Embrace It, But Put Up Guardrails – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Cisco’s Pam Lindemoen and Daniel...
Why Entities Should Review Their Online Tracker Use ASAP – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , HIPAA/HITECH Nick Heesters of HHS OCR on the Agency’s Top Areas of HIPAA Scrutiny...
Cyber Experts Urge House Committee to Avoid Federal Shutdown – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Cybersecurity Spending , Government Annual Federal Funding Will Expire in 12 Days Marianne Kolbasuk McGee (HealthInfoSec) •...
CrowdStrike to Buy AppSec Startup Bionic for Reported $350M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Deal Will Offer Visibility Into Application Behavior, Vulnerability Prioritization Michael Novinson (MichaelNovinson) • September 19, 2023...
China-Linked Actor Taps Linux Backdoor in Forceful Espionage Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading “Earth Lusca,” a China-linked cyber espionage actor that’s been actively targeting government organizations in Asia, Latin...
Trend Micro Patches Zero-Day Endpoint Vulnerability – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Trend Micro has released an advisory covering a critical zero-day flaw — tracked as CVE-2023-41179 — that...
MGM, Caesars Face Regulatory, Legal Maze After Cyber Incidents – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading In the wake of the new Securities and Exchange Commission (SEC) regulatory requirements to disclose “material” cyber...
Qatar Cyber Chiefs Warn on Mozilla RCE Bugs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The National Cyber Security Agency in Qatar is warning Adobe users to urgently apply patches following the...
Name That Toon: Somewhere in Sleepy Hollow – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist Harken, readers! ‘Tis you we love! Come up with a clever cybersecurity-related caption for the cartoon, above! (Our favorite...
Clorox Sees Product Shortages Amid Cyberattack Cleanup – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The Clorox Company is starting to feel the pinch of product shortages after a recent...
CapraRAT Impersonates YouTube to Hijack Android Devices – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A known Pakistan-linked threat actor is dangling romance-based content lures to spread Android-based spyware that mimics YouTube...
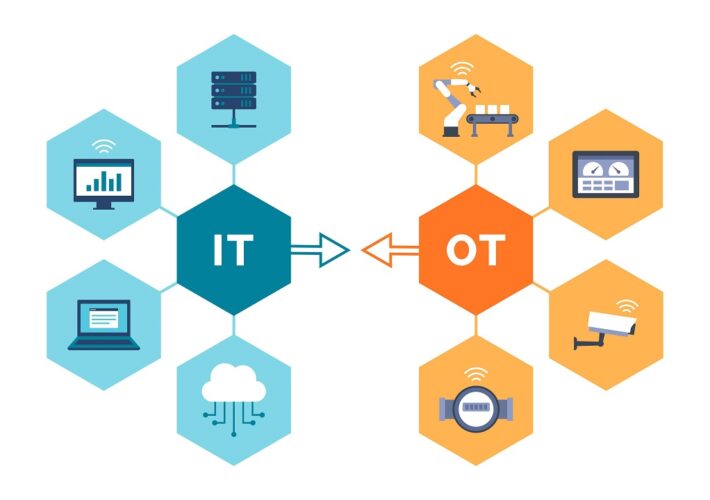
Engineering-Grade OT Protection – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andrew Ginter, Vice President of Industrial Security, Waterfall Security Solutions The following are excerpts from a book set to be launched Nov....
Welcome to the Resilience Revolution, Where Defenders Act More Like Attackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Dark Reading News Desk interviewed Kelly Shortridge, senior principal at Fastly at Black Hat USA 2023 about...
‘ShroudedSnooper’ Backdoors Use Ultra-Stealth in Mideast Telecom Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading A potentially novel threat actor recently compromised two Middle East-based telecommunications organizations, using two backdoors with...